What are two benefits for using private IPv4 addressing? (Choose two.)
Which group of channels in the 802.11b/g/n/ax 2.4 GHz frequency bands are non-overlapping channels?
Refer to the exhibit.
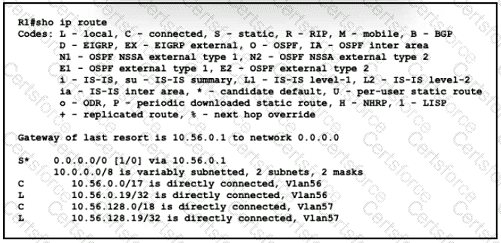
When router R1 is sending traffic to IP address 10.56.192 1, which interface or next hop address does it use to route the packet?
Refer to the exhibit.
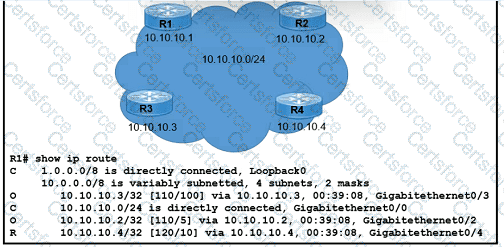
Which next-hop IP address has the least desirable metric when sourced from R1?
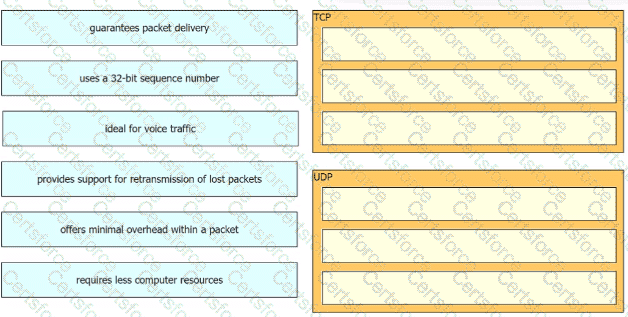
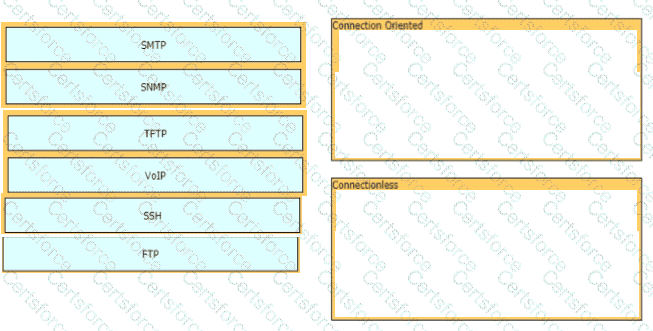
Drag and drop the characteristics of transport layer protocols from the left onto the corresponding protocols on the right.
Refer to the exhibit.
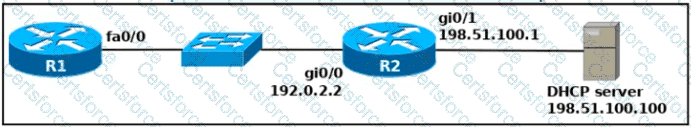
An engineer deploys a topology in which R1 obtains its IP configuration from DHCP. If
the switch and DHCP server configurations are complete and correct. Which two sets of commands must be configured on R1 and R2 to complete the task? (Choose two)
Refer to the exhibit.
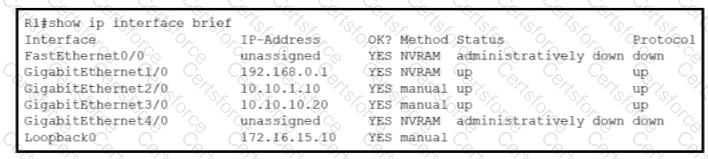
What does router R1 use as its OSPF router-ID?
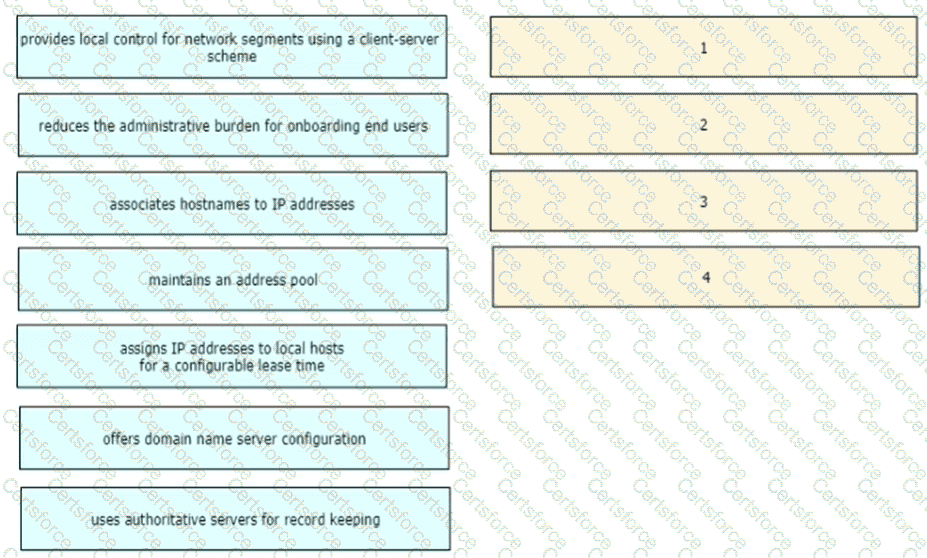
Drag the descriptions of device management from the left onto the types of device management on the right.
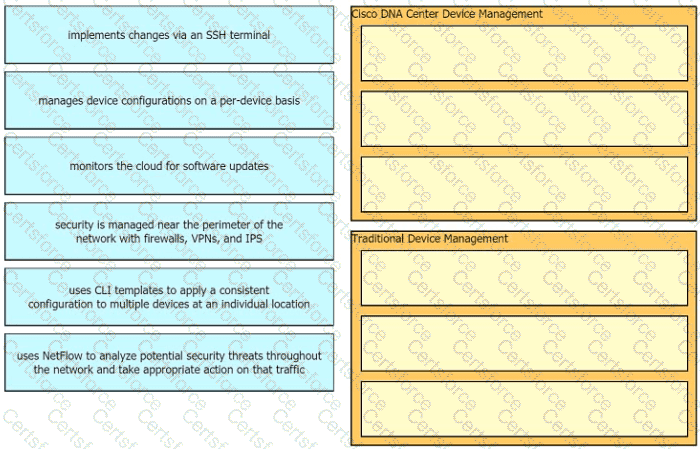
Which architecture is best for small offices with minimal wireless needs and no central management?
Which REST method updates an object in the Cisco DNA Center Intent API?
Where does a switch maintain DHCP snooping information?
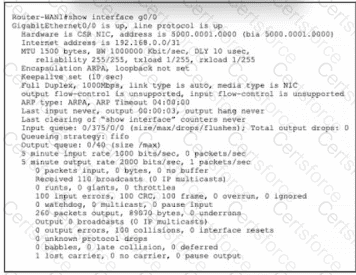
Refer to the exhibit. Router-WAN1 has a new connection via Gi0/0 to the ISP. Users running the web applications indicate that connectivity is unstable to the internet. What is causing the interface issue?
What is the primary purpose of private address space?
How does network automation help reduce network downtime?
A network engineer is configuring a new router at a branch office. The router is connected to an upstream WAN network that allows the branch to communicate with the head office. The central time server with IP address 172.24.54.8 is located behind a firewall at the head office. Which command must the engineer configure so that the software clock of the new router synchronizes with the time server?
Drag and drop the network protocols from the left onto the correct transport services on the right.
in Which way does a spine and-leaf architecture allow for scalability in a network when additional access ports are required?
When configuring IPv6 on an interface, which two IPv6 multicast groups are joined? (Choose two)
Drag and drop the functions of DHCP from the left onto any of the positions on the right Not all functions are used
Which command entered on a switch configured with Rapid PVST* listens and learns for a specific time period?
Which technology allows for multiple operating systems to be run on a single host computer?
Refer to the exhibit.
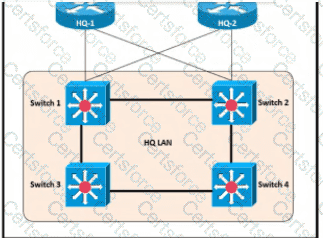
After the election process what is the root bridge in the HQ LAN?
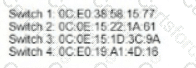
Refer to the exhibit.
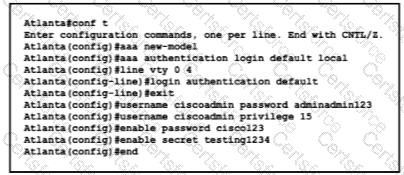
Which password must an engineer use to enter the enable mode?
What criteria is used first during me root port selection process?
Which command on a port enters the forwarding state immediately when a PC is connected to it?
What causes a port to be placed in the err-disabled state?
What is a DHCP client?
What occurs to frames during the process of frame flooding?
Which type of address is the public IP address of a NAT device?
What is a role of wireless controllers in an enterprise network?
How does QoS optimize voice traffic?
If a notice-level messaging is sent to a syslog server, which event has occurred?
Which device controls the forwarding of authentication requests for users when connecting to the network using a lightweight access point?
An email user has been lured into clicking a link in an email sent by their company's security organization. The webpage that opens reports that it was safe but the link could have contained malicious code. Which type of security program is in place?
What are two functions of an SDN controller? (Choose two)
When implementing a router as a DHCP server, which two features must be configured'? (Choose two)
What is a function of a remote access VPN?
Which WLC port connects to a switch to pass normal access-point traffic?
Refer to the exhibit.
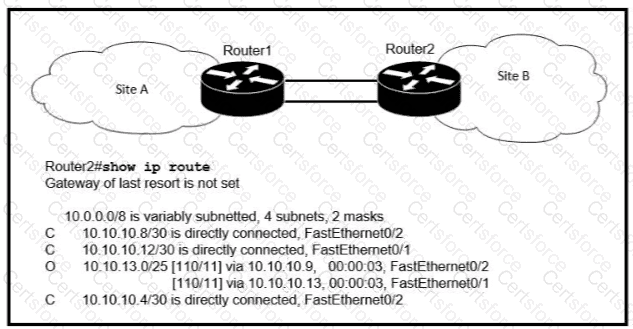
If OSPF is running on this network, how does Router 2 handle traffic from Site B to 10.10.13/25 at Site A?
Which two outcomes are predictable behaviors for HSRP? (Choose two.)
What is a purpose of traffic shaping?
Which command do you enter so that a switch configured with Rapid PVST + listens and learns for a specific time period?
An engineer must configure a/30 subnet between two routers. Which usable IP address and subnet mask combination meets this criteria?
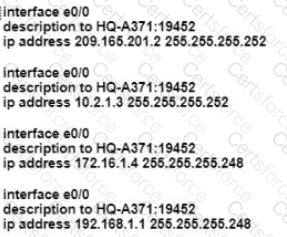
How will Link Aggregation be Implemented on a Cisco Wireless LAN Controller?
Which technology is used to improve web traffic performance by proxy caching?
What is the benefit of using FHRP?
Which two minimum parameters must be configured on an active interface to enable OSPFv2 to operate? (Choose two)
By default, how Does EIGRP determine the metric of a route for the routing table?
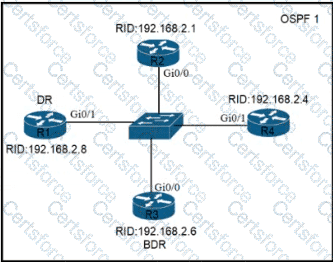
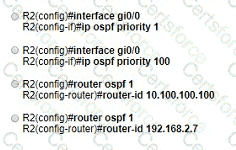
Refer to the exhibit. All routers in the network are configured R2 must be the DR. After the engineer connected the devices, R1 was elected as the DR. Which command sequence must be configure on R2 to Be elected as the DR in the network?