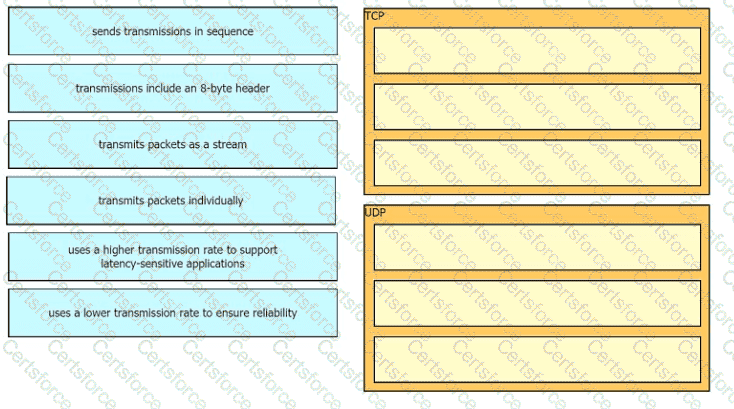
Drag the descriptions of IP protocol transmissions from the left onto the IP traffic types on the right.
What is a difference between RADIUS and TACACS+?
Using direct sequence spread spectrum, which three 2.4-GHz channels are used to limit collisions?
A wireless administrator has configured a WLAN; however, the clients need access to a less congested 5-GHz network for their voice quality. What action must be taken to meet the requirement?
What are two descriptions of three-tier network topologies? (Choose two)
How do traditional campus device management and Cisco DNA Center device management differ in regards to deployment?
A user configured OSPF in a single area between two routers A serial interface connecting R1 and R2 is running encapsulation PPP By default which OSPF network type is seen on this interface when the user types show ip ospf interface on R1 or R2?
A network engineer must configure the router R1 GigabitEthernet1/1 interface to connect to the router R2 GigabitEthernet1/1 interface. For the configuration to be applied the engineer must compress the address 2001:0db8:0000:0000:0500:000a:400F:583B. Which command must be issued on the interface?
Which network plane is centralized and manages routing decisions?
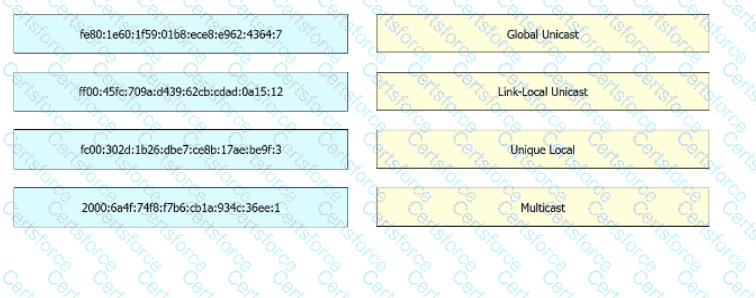
which IPv6 address block forwards packets to a multicast address rather than a unicast address?
Which two primary drivers support the need for network automation? (Choose two.)
Refer to the exhibit.

Which route type does the routing protocol Code D represent in the output?
An engineer must configure traffic for a VLAN that is untagged by the switch as it crosses a trunk link. Which command should be used?
Refer to Exhibit.
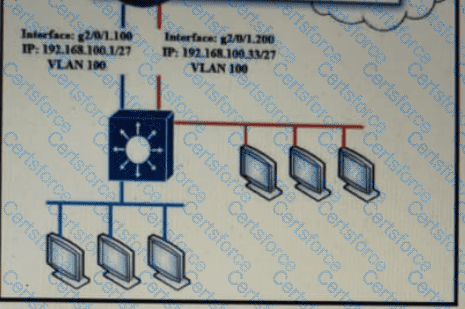
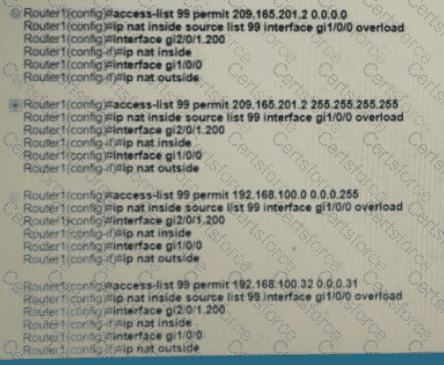
Which configuration must be applied to the router that configures PAT to translate all addresses in VLAN 200 while allowing devices on VLAN 100 to use their own IP addresses?
How do AAA operations compare regarding user identification, user services and access control?
What are two differences between optical-fiber cabling and copper cabling? (Choose two)
What prevents a workstation from receiving a DHCP address?
A network administrator enabled port security on a switch interface connected to a printer. What is the next configuration action in order to allow the port to learn the MAC address of the printer and insert it into the table automatically?
What are two characteristics of a controller-based network? (Choose two)
How does a Cisco Unified Wireless network respond to Wi-Fi channel overlap?
Which design element is a best practice when deploying an 802.11b wireless infrastructure?
What is a characteristic of a Layer 2 switch?
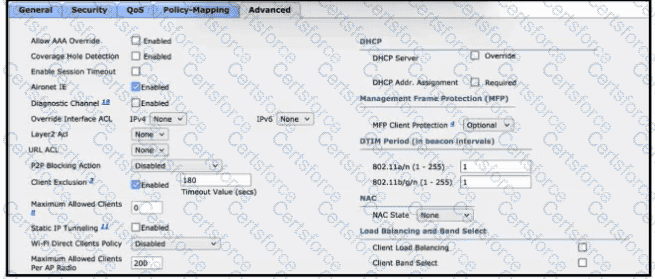
Refer to the exhibit. After a recent internal security audit, the network administrator decided to block all P2P-capable devices from the selected SSID. Which configuration setting must the administrator apply?
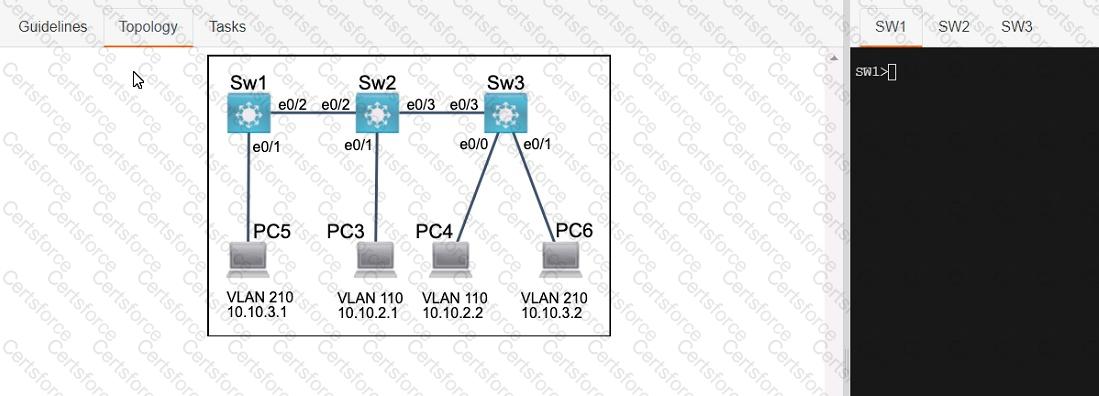
Three switches must be configured for Layer 2 connectivity. The company requires only the designated VLANs to be configured on their respective switches and permitted accross any links between switches for security purposes. Do not modify or delete VTP configurations.
The network needs two user-defined VLANs configured:
VLAN 110: MARKETING
VLAN 210: FINANCE
1. Configure the VLANs on the designated switches and assign them as access ports to the interfaces connected to the PCs.
2. Configure the e0/2 interfaces on Sw1 and Sw2 as 802.1q trunks with only the required VLANs permitted.
3. Configure the e0/3 interfaces on Sw2 and Sw3 as 802.1q trunks with only the required VLANs permitted.
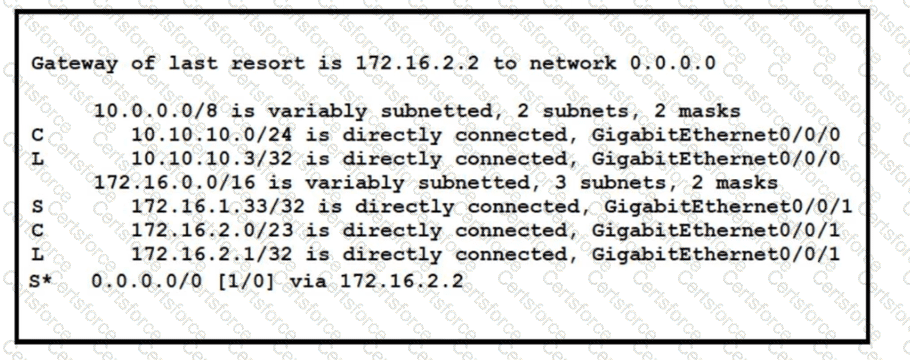
Refer to the exhibit. A packet sourced from 10.10.10.1 is destined for 172.16.3.254. What is the subnet mask of the destination route?
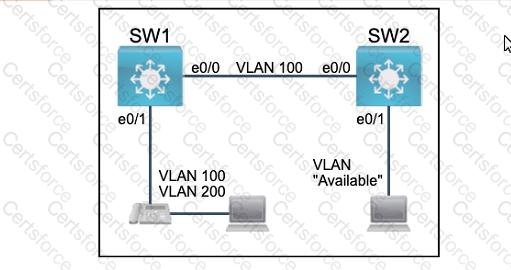
All physical cabling between the two switches is installed. Configure the network connectivity between the switches using the designated VLANs and interfaces.
1. Configure VLAN 100 named Compute and VLAN 200 named Telephony where required for each task.
2. Configure Ethernet0/1 on SW2 to use the existing VLAN named Available.
3. Configure the connection between the switches using access ports.
4. Configure Ethernet0/1 on SW1 using data and voice VLANs.
5. Configure Ethemet0/1 on SW2 so that the Cisco proprietary neighbor discovery protocol is turned off for the designated interface only.
What is a characteristic of private IPv4 addressing?
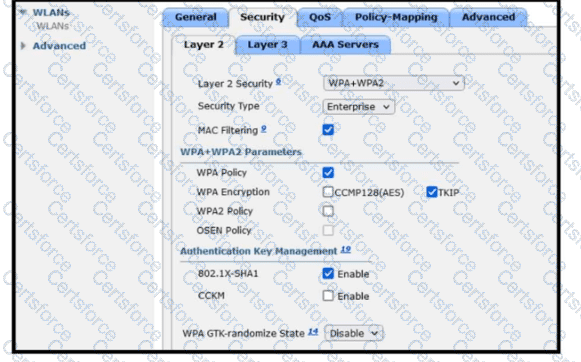
Refer to the exhibit. A guest WLAN must be created that prompts the client for a username and password on the local web page of the WLC. Which two actions must be performed on the Layer 2 tab before enabling the Authentication option on the Layer 3 tab? (Choose two.)
A default route must be configured to temporarily use a local broadband modem with the IP address of 192.168.1.1 until a WAN circuit is installed. The WAN circuit will use an external routing protocol that exchanges network prefixes between two separate autonomous systems on the Internet. Only a default route will be received by the ISP Which configuration must be applied to allow the new WAN circuit to take precedence when It Is In place?
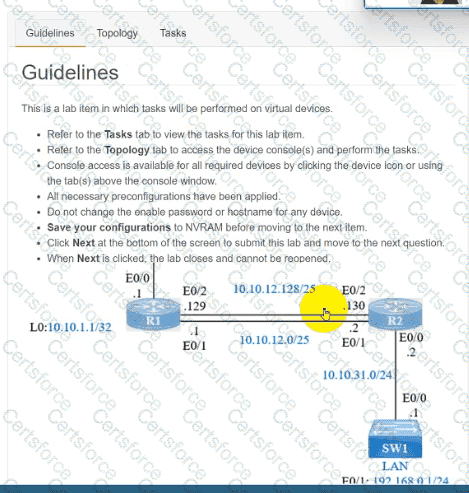
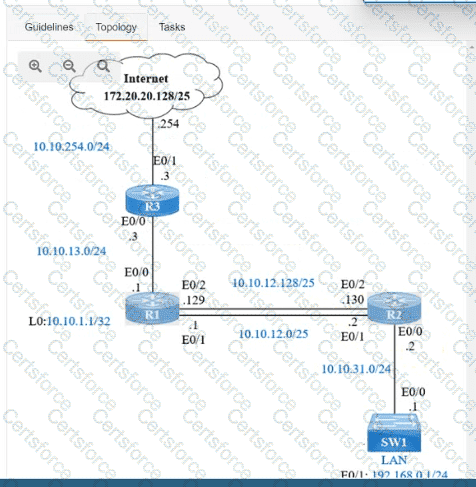
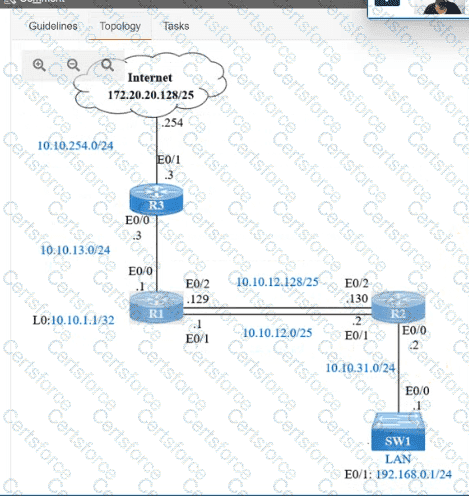
IP connectivity and OSPF are preconfigured on all devices where necessary. Do not make any changes to the IP addressing or OSPF. The company policy uses connected interfaces and next hops when configuring static routes except for load balancing or redundancy without floating static. Connectivity must be established between subnet 172.20.20.128/25 on the Internet and the LAN at 192.168.0.0/24 connected to SW1:
1. Configure reachability to the switch SW1 LAN subnet in router R2.
2. Configure default reachability to the Internet subnet in router R1.
3. Configure a single static route in router R2 to reach to the Internet subnet considering both redundant links between routers R1 and R2. A default route is NOT allowed in router R2.
4. Configure a static route in router R1 toward the switch SW1 LAN subnet where the primary link must be through Ethernet0/1. and the backup link must be through Ethernet0/2 using a floating route. Use the minimal administrative distance value when required.
Refer to the exhibit.
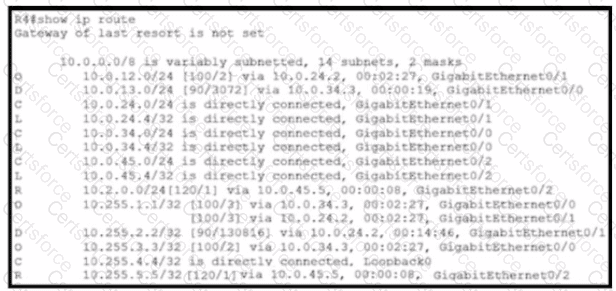
Of the routes learned with dynamic routing protocols, which has the least preferred metric?
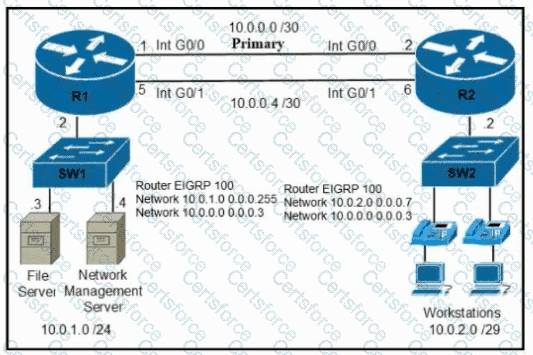
Refer to the exhibit. A secondary route is required on router R1 to pass traffic to the LAN network on R2 if the primary link fails. Which command must be entered to configure the router?

Refer to the exhibit. Which next hop is used to route packets to the application server at 152.168.32.85?
Which type of protocol is VRRP?
How does MAC learning function?
What is a similarity between global and unique local IPv6 addresses?
Refer to the exhibit.
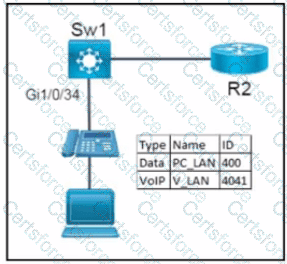
Network services must be enabled on interface Gil/0734. Which configuration meets the needs for this implementation?
A)
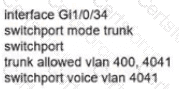
B)
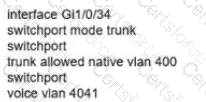
C)
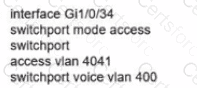
D)
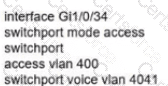
Which default condition must be considered when an encrypted mobility tunnel is used between two Cisco WLCs?
Which technology allows multiple operating systems lo run a single physical server?
What is the default interface for in-band wireless network management on a WLC?
Drag and drop the IPv6 address from the left onto the type on the right.
Refer to the exhibit.
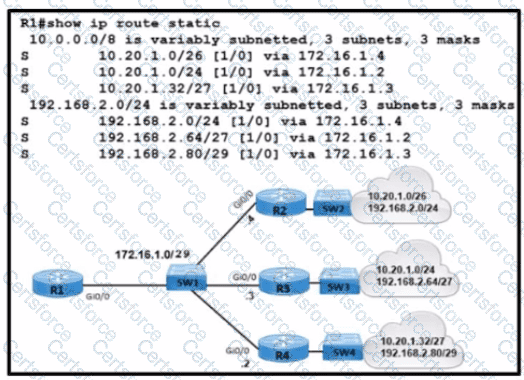
What is the correct next hop for router R1 to reach IP addresses 192.168.2.86 and 10.20.1.50?
What is a characteristic of a Layer 2 switch?
Which two principles must be considered when using per-hop behavior in QoS? (Choose two.)
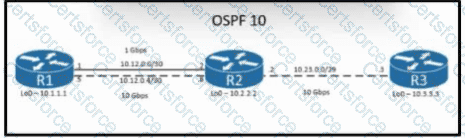
Refer to the exhibit. The loopback IP of R3 has been learned via the two interfaces on R1. R1 is configured with a reference bandwidth of 10 Gbps. Based on the metric calculations, which next hop IP would be used for outgoing routing?
What is a characteristic of an SSID in wireless networks?
What is the total number of users permitted to simultaneously browse the controller management pages when using the AireOS GUI?
How is Al used to identify issues within network traffic?
Refer to the exhibit.
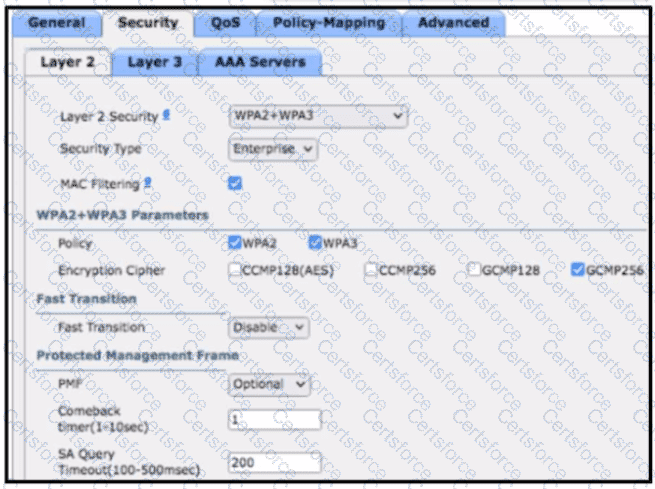
An engineer must document all Wi-Fi services on a new wireless LAN controller. The Wi-Fi SSID "Office_WLan" has Layer 2 Security. What is determined by this configuration?
What is the difference between the TCP and UDP protocols?