What is the difference between an IPv6 link-local address and a unique local address?
What does physical access control regulate?
Refer to the exhibit.
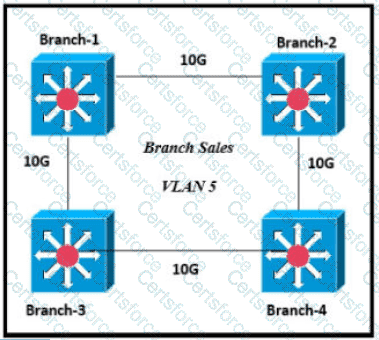
Only four switches are participating in the VLAN spanning-tree process.
Branch-1 priority 614440
Branch-2: priority 39082416
Branch-3: priority 0
Branch-4: root primary
Which switch becomes the permanent root bridge for VLAN 5?
Which feature of Digest Authentication prevents credentials from being sent in plaintext?
Which architecture is best for small offices with minimal wireless needs and no central management?
Refer to the exhibit.
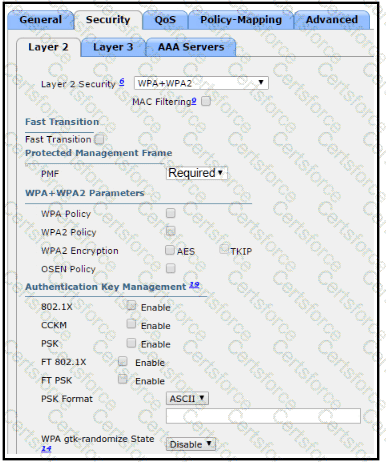
The network engineer is configuring a new WLAN and is told to use a static password for authentication instead of the RADIUS servers. Which additional set of tasks must the engineer perform to complete the configuration?
Refer to the exhibit.
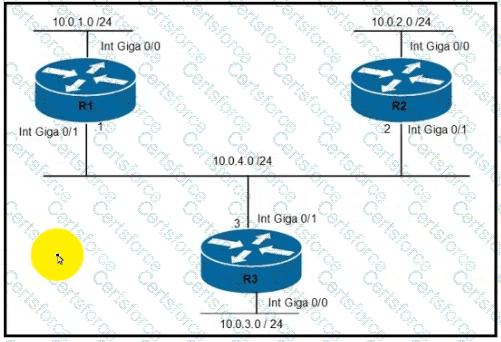
Router R1 must be configured to reach the 10.0.3.0/24 network from the 10.0.1.0/24 segment.
Which command must be used to configure the route?
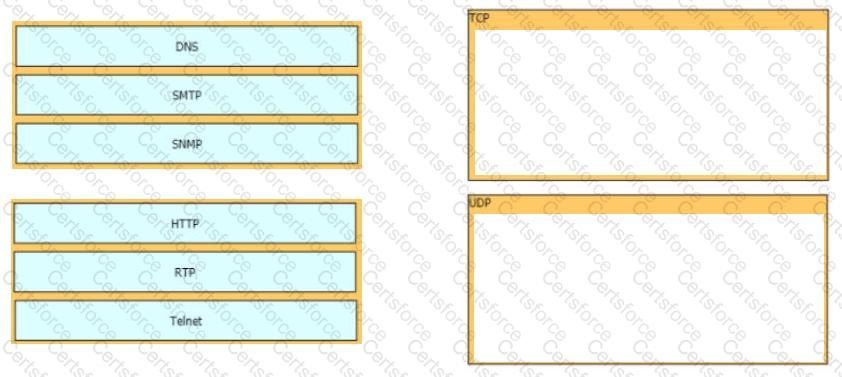
Drag and drop the TCP/IP protocols from the left onto the transmission protocols on the right
Which technology allows for logical Layer 3 separation on physical network equipment?
How does MAC learning function?
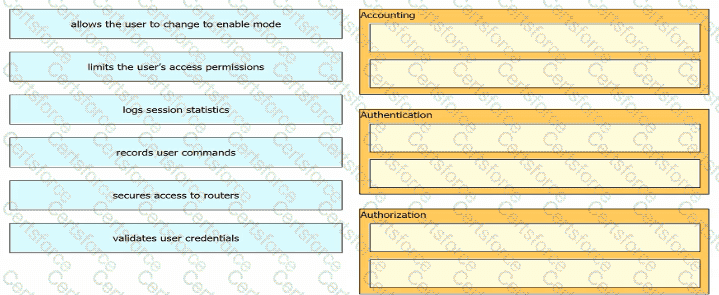
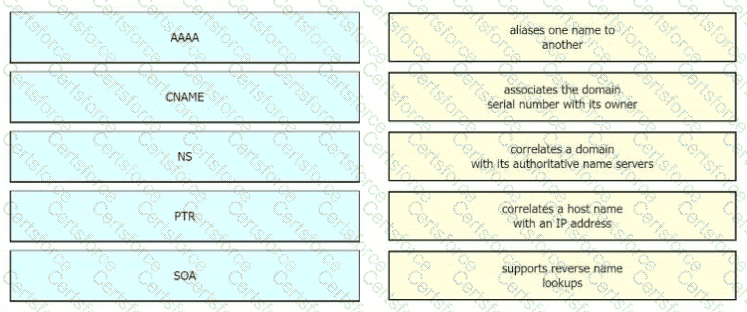
Drag and drop the descriptions of AAA services from the left onto the corresponding services on the right.
Refer to the exhibit.
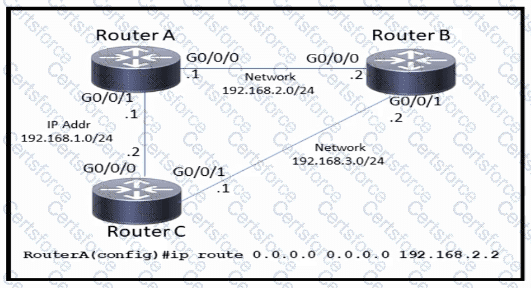
Which command must be issued to enable a floating static default route on router A?
Which two network actions occur within the data plane? (Choose two.)
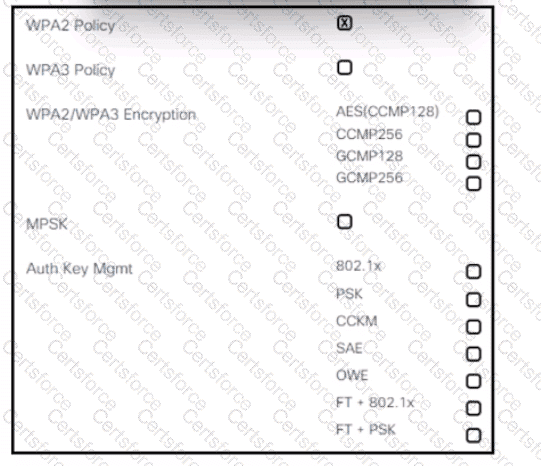
Refer to the exhibit. An engineer is creating a secure preshared key based SSID using WPA2 for a wireless network running on 2.4 GHz and 5 GHz. Which two tasks must the engineer perform to complete the process? (Choose two.)
What is one reason to implement LAG on a Cisco WLC?
Refer to the exhibit.
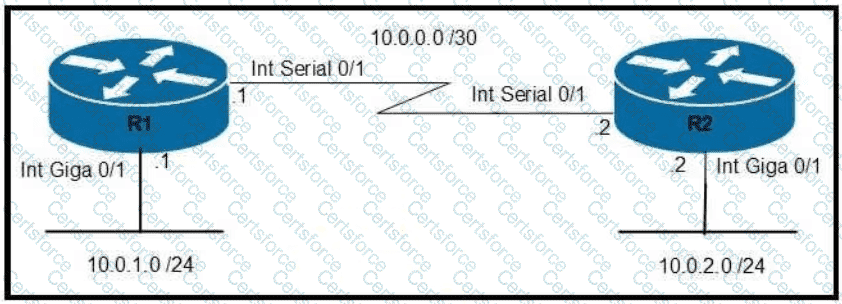
Which command configures OSPF on the point-to-point link between routers R1 and R2?
Refer to the exhibit.
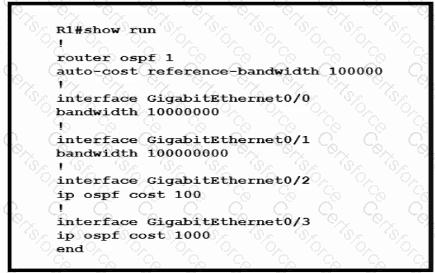
Router R1 resides in OSPF Area 0. After updating the R1 configuration to influence the paths that it will use to direct traffic, an engineer verified that each of the four Gigabit interfaces has the same route to 10.10.0.0/16. Which interface will R1 choose to send traffic to reach the route?
Refer to the exhibit.
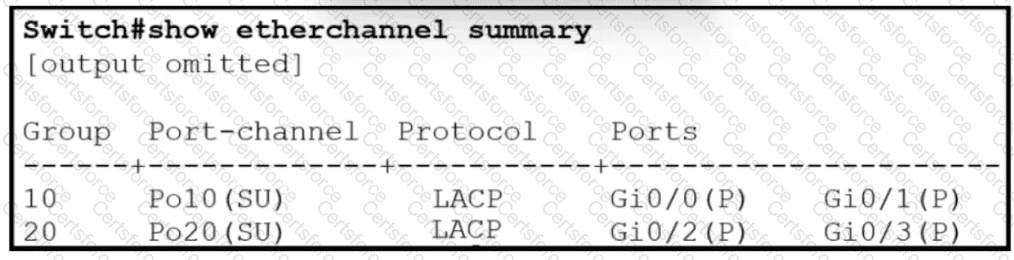
Which two commands when used together create port channel 10? (Choose two.)
What does the term "spirt MAC” refer to in a wireless architecture?
Drag and drop the TCP or UDP details from the left onto their corresponding protocols on the right.
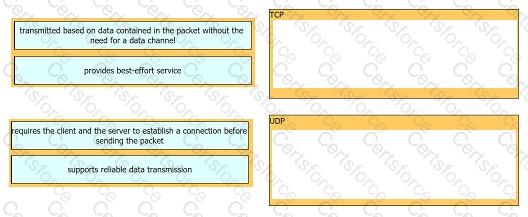
Refer to the exhibit.
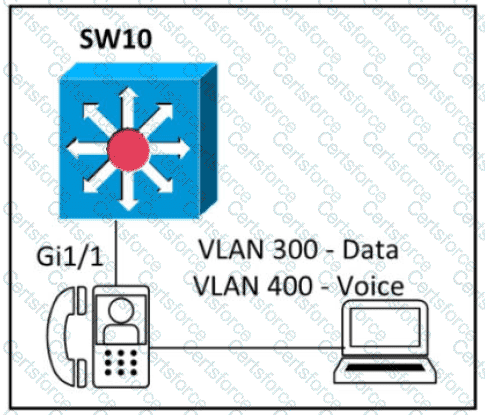
An engineer must configure GigabitEthernet1/1 to accommodate voice and data traffic Which configuration accomplishes this task?

Which two outcomes are predictable behaviors for HSRP? (Choose two)
On workstations running Microsoft Windows, which protocol provides the default gateway for the device?
How does automation leverage data models to reduce the operational complexity of a managed network?
Which syslog message logging level displays interface line protocol up/down events?
How do TCP and UDP differ in the way they guarantee packet delivery?
What protocol allows an engineer to back up 20 network router configurations globally while using the copy function?
Refer to the exhibit.
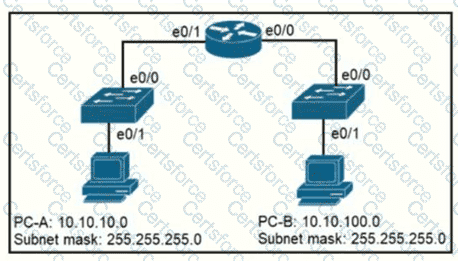
When PC-A sends traffic to PC-B, which network component is in charge of receiving the packet from PC-A verifying the IP addresses, and forwarding the packet to PC-B?
Refer to the exhibit.
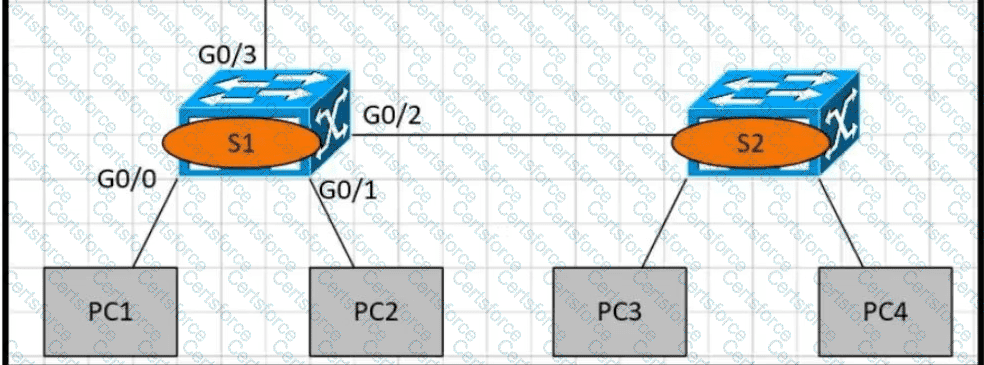
PC1 is trying to ping PC3 for the first time and sends out an ARP to S1 Which action is taken by S1?
What is a recommended approach to avoid co-channel congestion while installing access points that use the 2.4 GHz frequency?
Refer to the Exhibit.
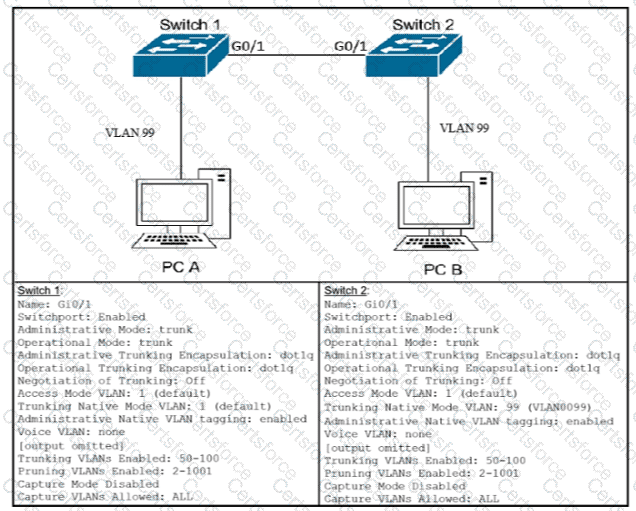
After the switch configuration the ping test fails between PC A and PC B Based on the output for switch 1. which error must be corrected?
Which function is performed by the collapsed core layer in a two-tier architecture?
What is the primary effect of the spanning-tree portfast command?
Drag the IPv6 DNS record types from the left onto the description on the right.
Which QoS feature drops traffic that exceeds the committed access rate?
All physical cabling is in place. A company plans to deploy 32 new sites.
The sites will utilize both IPv4 and IPv6 networks.
1 . Subnet 172.25.0.0/16 to meet the subnet requirements and maximize
the number of hosts
Using the second subnet
• Assign the first usable IP address to e0/0 on Sw1O1
• Assign the last usable IP address to e0/0 on Sw102
2. Subnet to meet the subnet requirements and maximize
the number of hosts
c Using the second subnet
• Assign an IPv6 GUA using a unique 64-Bit interface identifier
on e0/0 on Sw101
• Assign an IPv6 GUA using a unique 64-Bit interface identifier
on eO/O on swi02
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.

A network security team noticed that an increasing number of employees are becoming victims of phishing attacks. Which security program should be implemented to mitigate the problem?
Why are API keys used to enforce rate limiting?
Why would a network administrator choose to implement RFC 1918 address space?
Which role does AI play in monitoring network data flow?
Which two spanning-tree states are bypassed on an interface running PortFast? (Choose two.)
Refer to the exhibit.
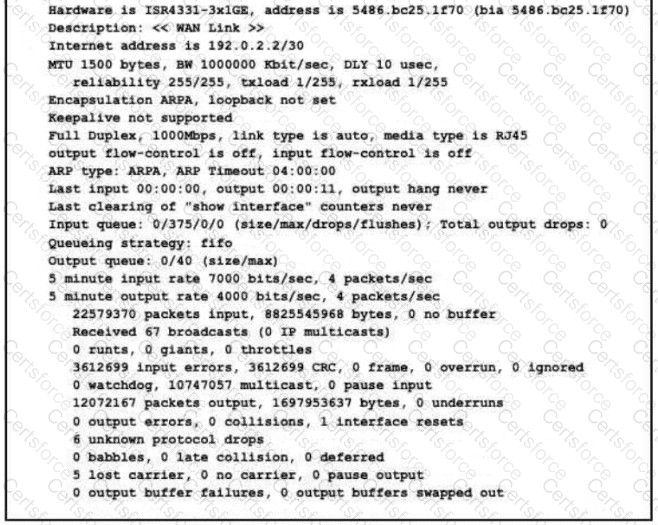
What is a reason for poor performance on the network interface?
A network engineer must configure two new subnets using the address block 10 70 128 0/19 to meet these requirements:
• The first subnet must support 24 hosts
• The second subnet must support 472 hosts
• Both subnets must use the longest subnet mask possible from the address block
Which two configurations must be used to configure the new subnets and meet a requirement to use the first available address in each subnet for the router interfaces? (Choose two )
Which PoE mode enables powered-device detection and guarantees power when the device is detected?
OSPF must be configured between routers R1 and R2. Which OSPF configuration must be applied to router R1 to avoid a DR/BDR election?
A network administrator is setting up a new IPv6 network using the 64-bit address 2001 0EB8 00C1 2200:0001 0000 0000 0331/64 To simplify the configuration the administrator has decided to compress the address Which IP address must the administrator configure?
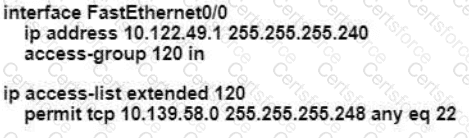
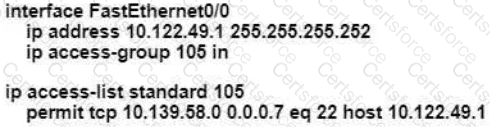
An engineer is configuring remote access to a router from IP subnet 10.139.58.0/28. The domain name, crypto keys, and SSH have been configured. Which configuration enables the traffic on the destination router?
A)
B)
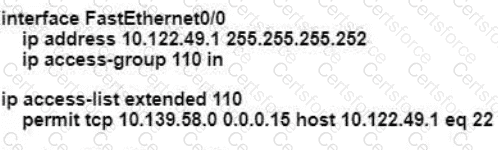
C)
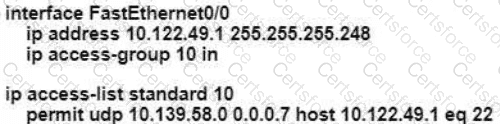
D)
Which action is taken by the data plane within a network device?
Which remote access protocol provides unsecured remote CLI access?
Drag and drop the network topology architecture types from the left onto the corresponding function on the right. Not all architecture types are used.
