Which type of encryption does WPA1 use for data protection?
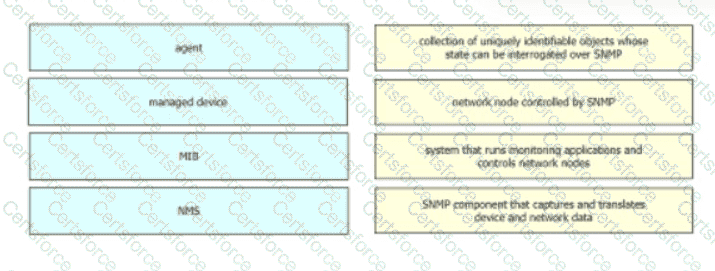
Drag and drop the SNMP components from the left onto the description on the right.
Which syslog severity level is considered the most severe and results in the system being considered unusable?
What is a specification for SSIDS?
What is a characteristic of private IPv4 addressing?
What are two differences between WPA2 and WPA3 wireless security? (Choose two.)
What is the maximum bandwidth of a T1 point-to-point connection?
A network engineer must back up 20 network router configurations globally within a customer environment. Which protocol allows the engineer to perform this function using the Cisco IOS MIB?
Refer to the exhibit.
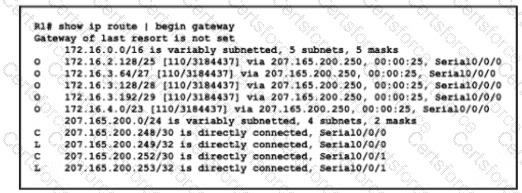
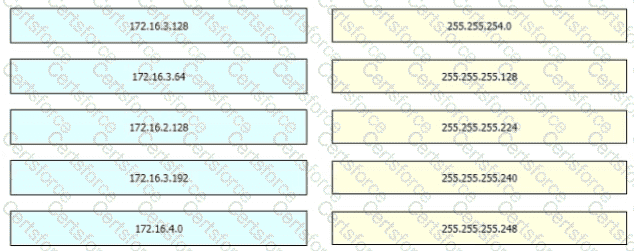
Drag and drop the learned prefixes from the left onto the subnet masks on the right