What are two differences between WPA2 and WPA3 wireless security? (Choose two.)
Which (unction generally performed by a traditional network device is replaced by a software-defined controller?
Refer to the exhibit.
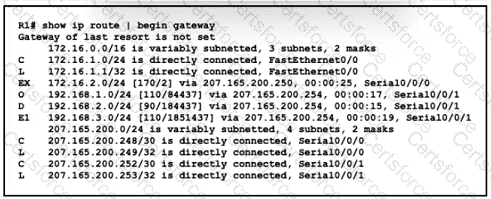
Which prefix did router R1 learn from internal EIGRP?
Refer to the exhibit.

Given the following switch MAC addresses, which switch will be elected as the root bridge?
SW1: 0C:5A:05:53:27:17
SW2: 0C:0A:A8:1A:3C:9D
SW3: 0C:0A:18:81:83:19
SW4: 0C:0A:05:22:05:97
A client experiences slow throughput from a server that is directly connected to the core switch in a data center. A network engineer finds minimal latency on connections to the server, but data transfers are unreliable, and the output of the show Interfaces counters errors command shows a high FCS-Err count on the interface that is connected to the server. What is the cause of the throughput issue?
What is a zero-day exploit?
What is a reason why an administrator would choose to implement an automated network management approach?
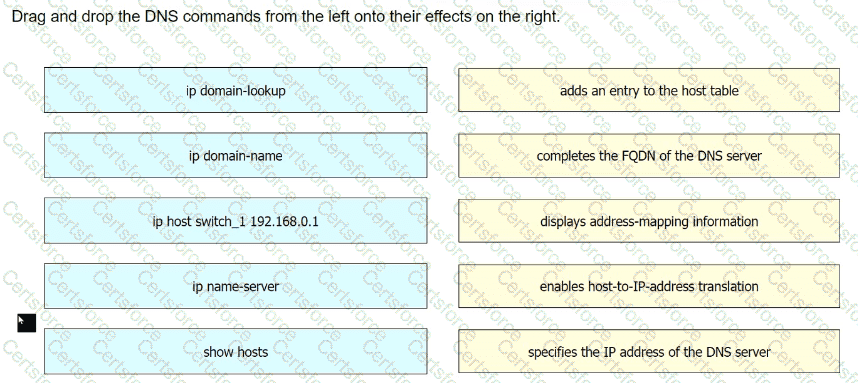
Drag and drop the DNS commands from the left onto their effects on the right.
Refer to the exhibit.
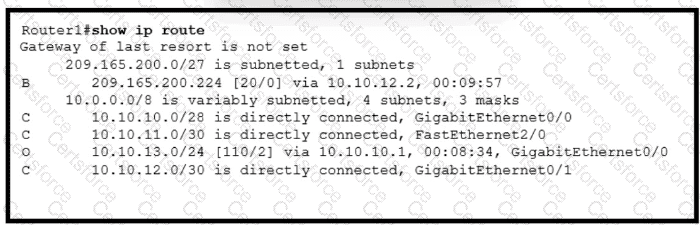
Which action by the router when a packet is sourced from 10.10.10.2 and destined 10.10.10.16?
What is an Ansible inventory?
Refer to the exhibit.
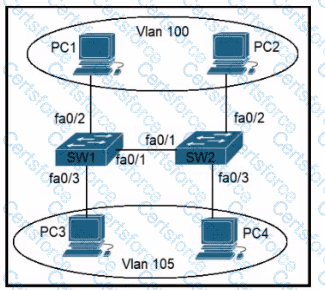
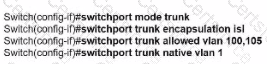
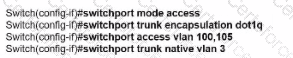
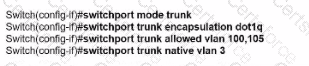
An engineer configures interface fa0/1 on SW1 and SW2 to pass traffic from two different VLANs. For security reasons, company policy requires the native VLAN to be set to a nondefault value. Which configuration meets this requirement?
A)
B)
C)

D)
Drag and drop the use cases for device-management technologies from the left onto the corresponding.
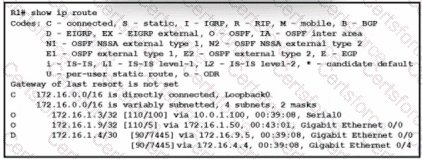
Refer to the exhibit. How does router R1 handle traffic to the 172.16.1.4/30 subnet?
Refer to the exhibit.
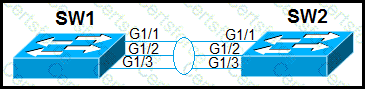
Which configuration establishes a Layer 2 LACP EtherChannel when applied to both switches?
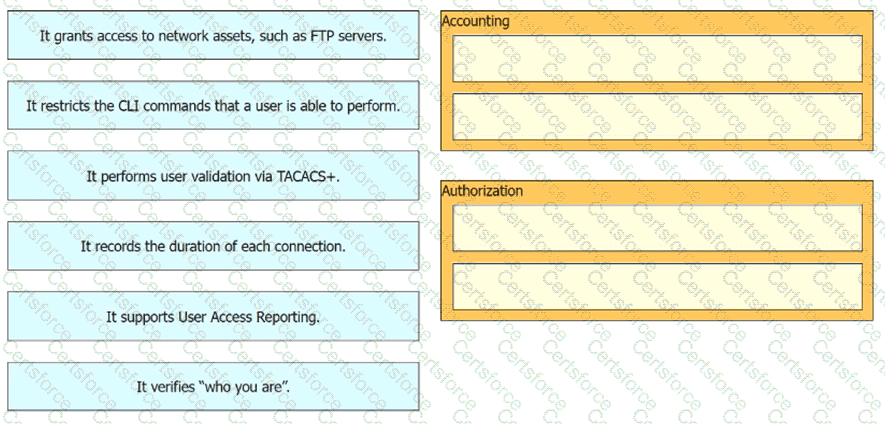
Drag and drop the statement about AAA services from the left to the corresponding AAA services on the right.
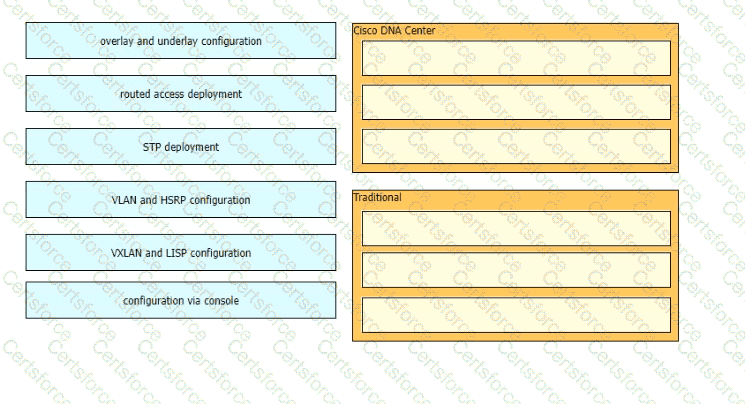
Drag and drop the network topology architecture types from the left onto the corresponding function on the right. Not all architecture types are used.

How do UTP and STP cables compare?
Which encryption method is used by WPA3?
Which capability does TFTP provide?
Refer to the exhibit.

Which types of JSON data is shown