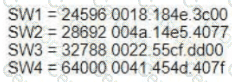
Refer to the exhibit.
Traffic sourced from the loopback0 Interface is trying to connect via ssh to the host at 10.0.1.15. What Is the next hop to the destination address?
An engineer is tasked to configure a switch with port security to ensure devices that forward unicasts multicasts and broadcasts are unable to flood the port The port must be configured to permit only two random MAC addresses at a time Drag and drop the required configuration commands from the left onto the sequence on the right Not all commands are used.

Drag and drop the TCP or UDP details from the left onto their corresponding protocols on the right.
OSPF must be configured between routers R1 and R2. Which OSPF configuration must be applied to router R1 to avoid a DR/BDR election?
Refer to the exhibit.
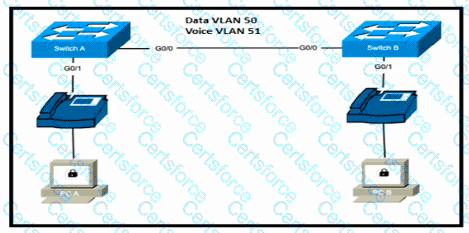
Switch A is newly configured. All VLANs are present in the VLAN database. The IP phone and PC A on Gi0/1 must be configured for the appropriate VLANs to establish connectivity between the PCs. Which command set fulfills the requirement?
A)
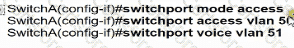
B)

C)

D)

Refer to the exhibit.
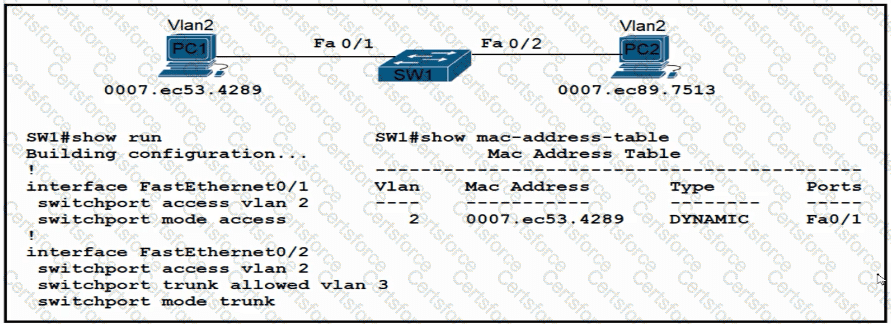
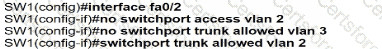
An engineer has started to configure replacement switch SW1. To verify part of the configuration, the engineer issued the commands as shown and noticed that the entry for PC2 is missing. Which change must be applied to SW1 so that PC1 and PC2 communicate normally?
A)
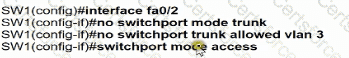
B)
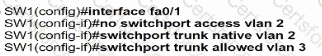
C)
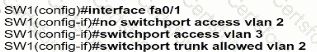
D)
What provides centralized control of authentication and roaming In an enterprise network?
What is an expected outcome when network management automation is deployed?
What is the function of the controller in a software-defined network?
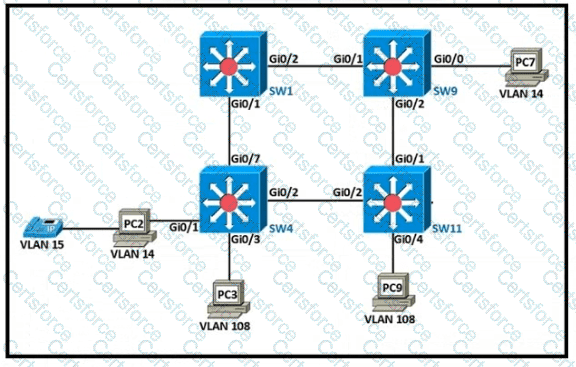
Refer to the exhibit.
The following must be considered:
• SW1 is fully configured for all traffic
• The SW4 and SW9 links to SW1 have been configured
• The SW4 interface Gi0/1 and Gi0/0 on SW9 have been configured
• The remaining switches have had all VLANs adde d to their VLAN database
Which configuration establishes a successful ping from PC2 to PC7 without interruption to traffic flow between other PCs?
A)

B)
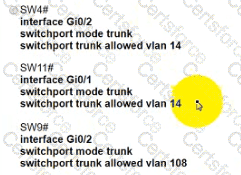
C)

D)

Refer to the exhibit.
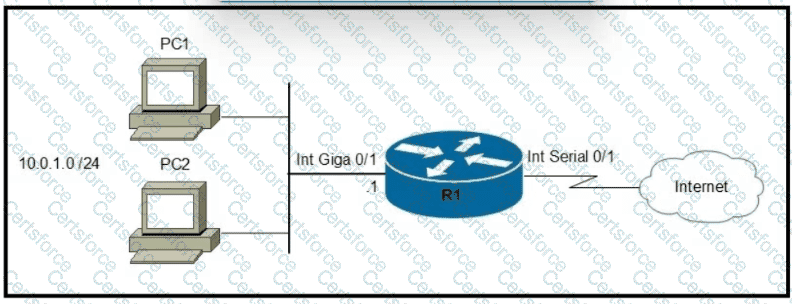
Which two commands must be configured on router R1 to enable the router to accept secure remote-access connections? (Choose two)
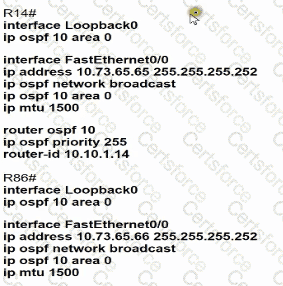
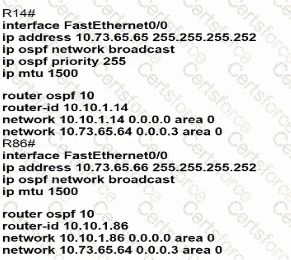
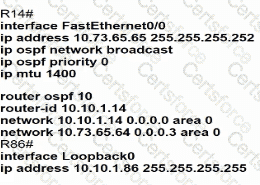
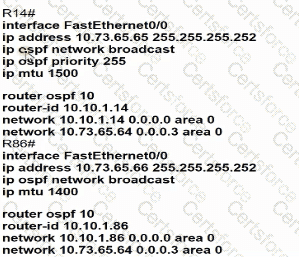
Refer to the exhibit.

Which configuration allows routers R14 and R86 to form an OSPFv2 adjacency while acting as a central point for exchanging OSPF information between routers?
A)
B)
C)
D)
Refer to the exhibit.
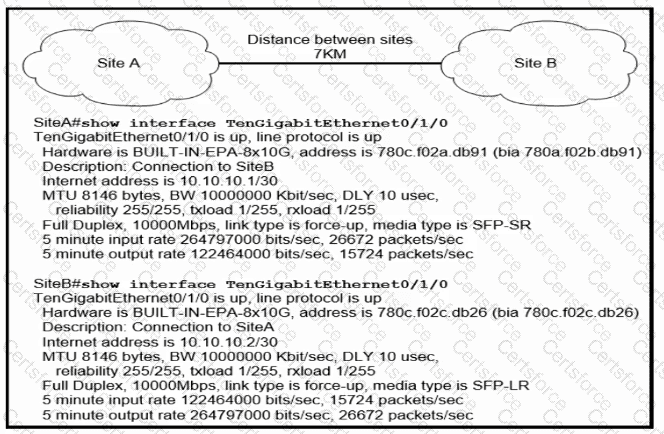
Site A was recently connected to site B over a new single-mode fiber path. Users at site A report Intermittent connectivity Issues with applications hosted at site B. What is the reason for the problem?
A network engineer must configure two new subnets using the address block 10 70 128 0/19 to meet these requirements:
• The first subnet must support 24 hosts
• The second subnet must support 472 hosts
• Both subnets must use the longest subnet mask possible from the address block
Which two configurations must be used to configure the new subnets and meet a requirement to use the first available address in each subnet for the router interfaces? (Choose two )
What is a function of a Next-Generation IPS?
Refer to the exhibit.
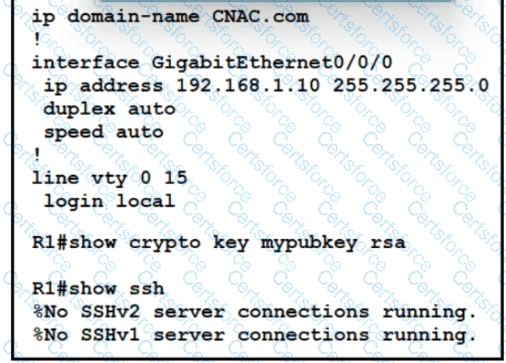
Which two commands must be added to update the configuration of router R1 so that it accepts only encrypted connections? (Choose two )
What causes a port to be placed in the err-disabled state?
Which interface mode must be configured to connect the lightweight APs in a centralized architecture?
Which protocol is used for secure remote CLI access?
Refer to the exhibit.
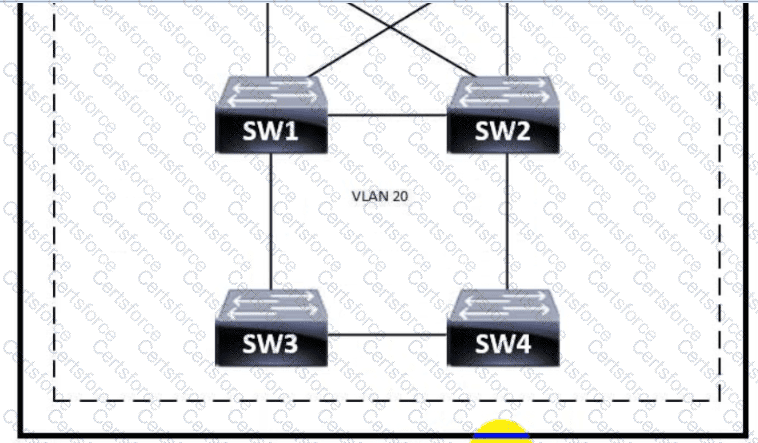
Which switch becomes the root of a spanning tree for VLAN 20 if all li links are of equal speed?