What is an advantage of using SDN versus traditional networking when it comes to security?
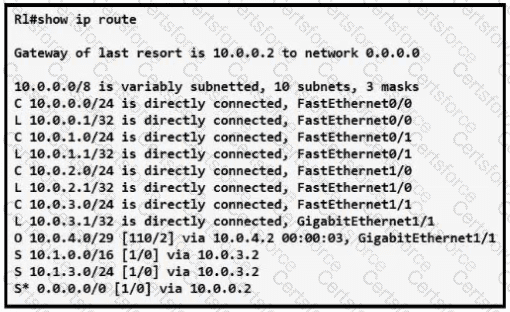
Refer to the exhibit.
How does router R1 forward packets destined to 10.0.4.10?
Which two northbound APIs are found in a software-defined network? (Choose two.)
Which AP feature provides a captive portal for users to authenticate, register, and accept terms before accessing the internet?
Which header must be included in a REST request from an application that requires JSON-formatted content?
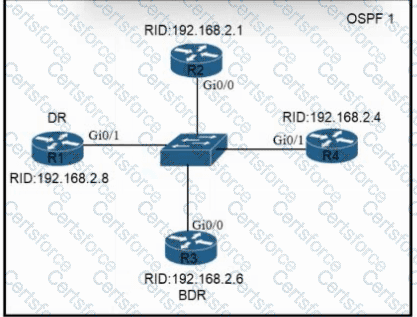
Refer to the exhibit. All routers In the network are configured. R2 must be the DR. After the engineer connected the devices, R1 was elected as the DR. Which command sequence must be configured on R2 to be elected as the DR in the network?

What is the purpose of the service-set identifier?
What is a function of Layer 3 switches?
What is a characteristic of private IPv4 addressing?
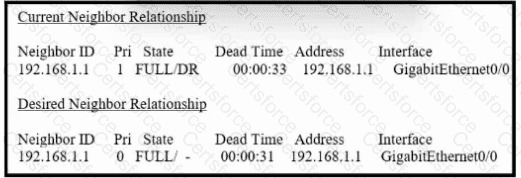
Refer to the exhibit. How must OSPF be configured on the GigabitEthernet0/0 interface of the neighbor device to achieve the desired neighbor relationship?
How does MAC learning function?
Which switch port configuration must be configured when connected to an AP running in FlexConnect mode, and the WLANs use flex local switching?
Which action prevents debug messages from being sent via syslog while allowing other messages when an abnormally high number of syslog messages are generated by a device with the debug process turned on?
What differentiates the TCP and UDP protocols?
How does automation affect network management processes?
A new DHCP server has been deployed in a corporate environment with lease time set to eight hours. Which CMD command on a Windows-based device allows the engineer to verify the DHCP lease expiration?
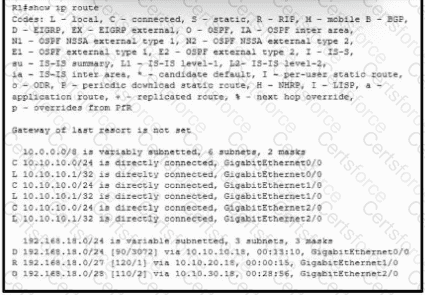
Refer to the exhibit. Which interface does a packet take to reach the host address of 192.168.18.16?
What is a reason to implement HSRP on a network?
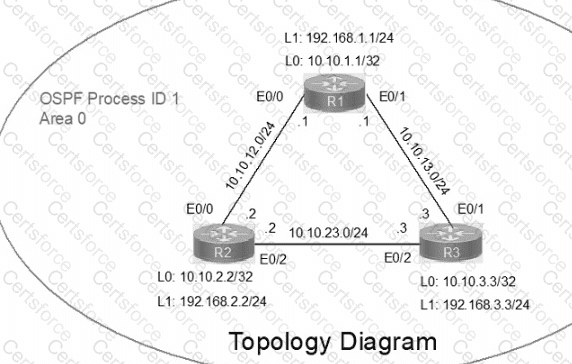
IP connectivity between the three routers is configured. OSPF adjacencies must be established.
1. Configure R1 and R2 Router IDs using the interface IP addresses from the link that is shared between them.
2. Configure the R2 links with a max value facing R1 and R3. R2 must become the DR. R1 and R3 links facing R2 must remain with the default OSPF configuration for DR election. Verify the configuration after clearing the OSPF process.
3. Using a host wildcard mask, configure all three routers to advertise their respective Loopback1 networks.
4. Configure the link between R1 and R3 to disable their ability to add other OSPF routers.
What is the function of the controller in a software-defined network?
Refer to the exhibit.
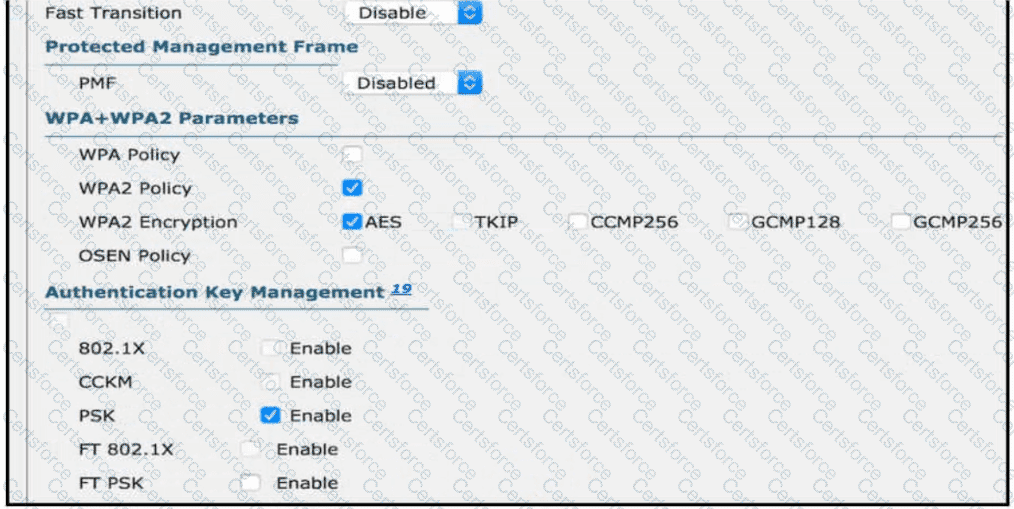
Users need to connect to the wireless network with IEEE 802. 11r-compatible devices. The connection must be maintained as users travel between floors or to other areas in the building What must be the configuration of the connection?
Refer to the exhibit.
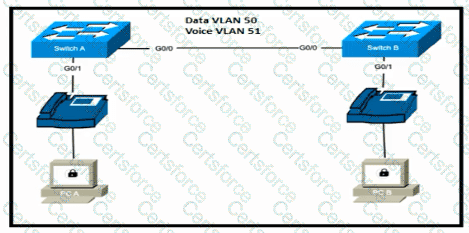
Switch A is newly configured. All VLANs are present in the VLAN database. The IP phone and PC A on Gi0/1 must be configured for the appropriate VLANs to establish connectivity between the PCs. Which command set fulfills the requirement?
A)
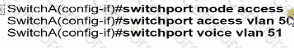
B)

C)

D)

A network engineer is installing an IPv6-only capable device. The client has requested that the device IP address be reachable only from the internal network. Which type of IPv6 address must the engineer assign?
Refer to the exhibit.
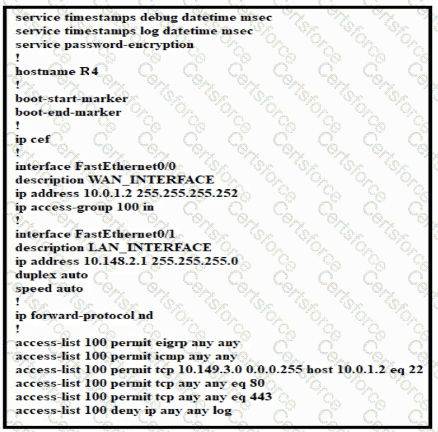
Which configuration enables DHCP addressing for hosts connected to interface FastEthernetO/1 on router R4?
Refer to the exhibit.
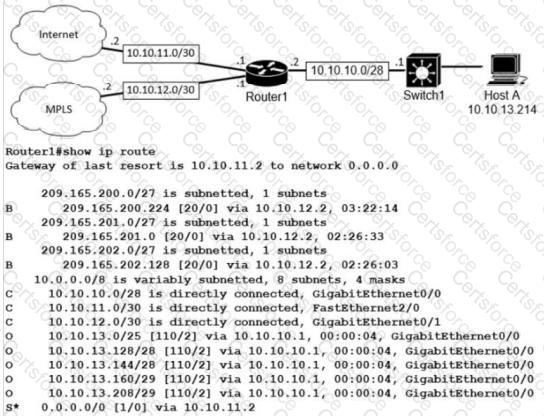
What is the prefix length for the route that router1 will use to reach host A?
Refer to the exhibit.
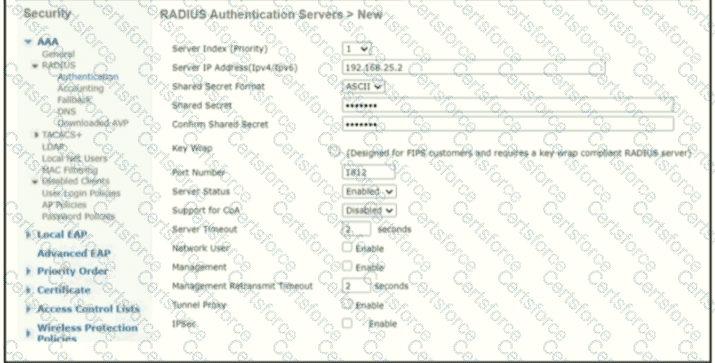
A network engineer configures the Cisco WLC to authenticate local wireless clients against a RADIUS server Which task must be performed to complete the process?
Refer to the exhibit.
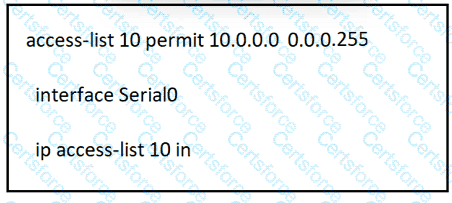
A network administrator must permit traffic from the 10.10.0.0/24 subnet to the WAN on interlace Seria10. What is the effect of the configuration as the administrator applies the command?
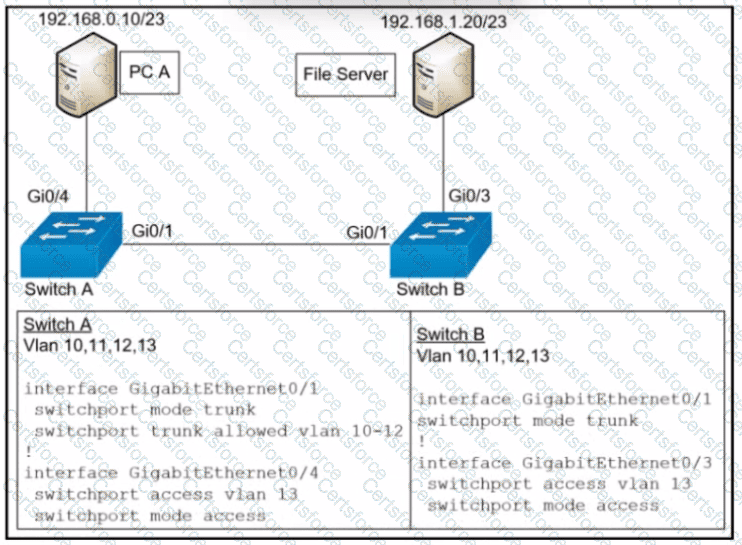
Refer to the exhibit.
PC A and the file server. Which commend must be configured on switch A to prevent interruption of other communications?
What does WPA3 provide in wireless networking?
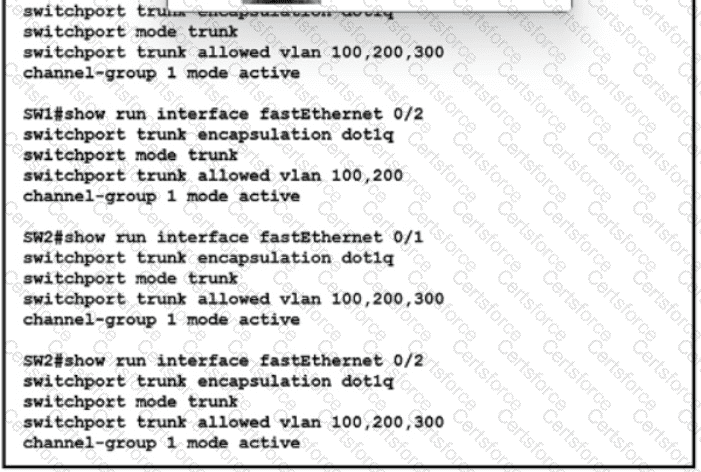
Refer to the exhibit. An engineer is building a new Layer 2 LACP EtherChannel between SW1 and SW2. and they executed the given show commands to verify the work Which additional task must be performed so that the switches successfully bundle the second member in the LACP port-channel?
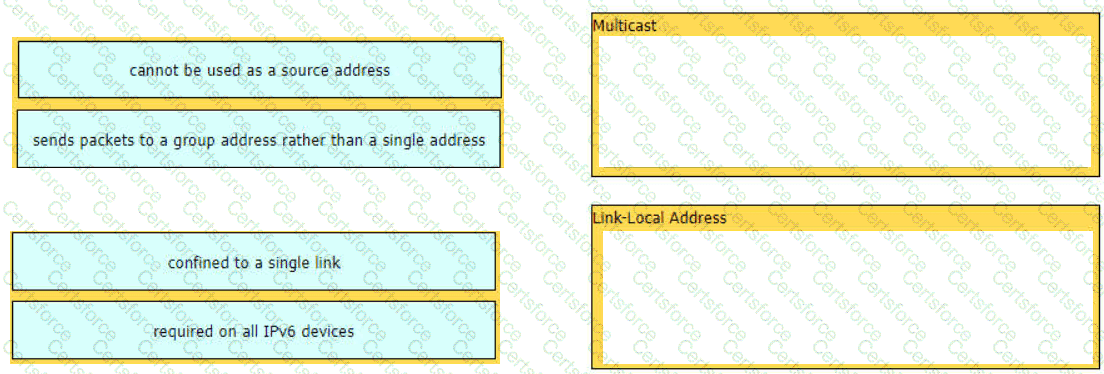
Drag and drop the characteristic from the left onto the IPv6 address type on the right.
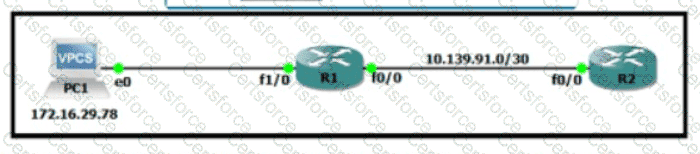
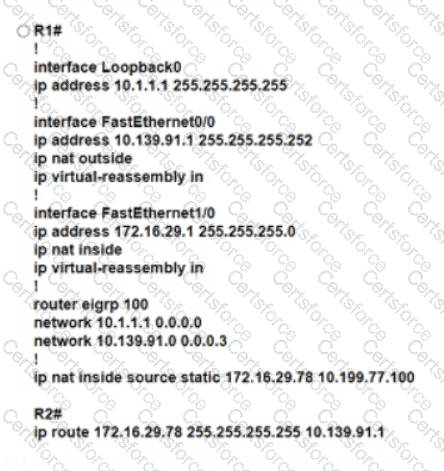
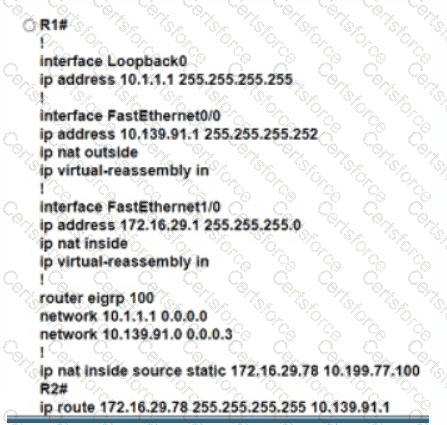
Refer to the exhibit. An engineer must translate the PC1 IP address to 10.199.77.100 and permit PC1 to ping the loopback 0 on router R2. What command set must be used?
A)
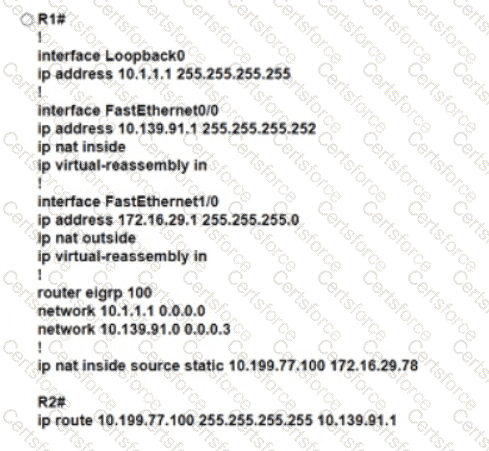
B)
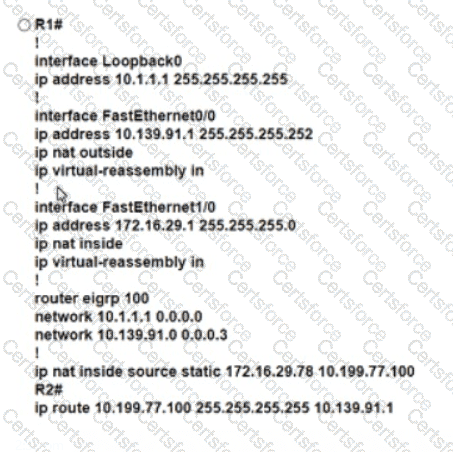
C)
D)
What Is the path for traffic sent from one user workstation to another workstation on a separate switch In a Ihree-lter architecture model?
The service password-encryption command is entered on a router. What is the effect of this configuration?
Which mode must be set for APs to communicate to a Wireless LAN Controller using the Control and Provisioning of Wireless Access Points (CAPWAP) protocol?
What does an SDN controller use as a communication protocol to relay forwarding changes to a southbound API?
When a WLAN with WPA2 PSK is configured in the Wireless LAN Controller GUI which format is supported?
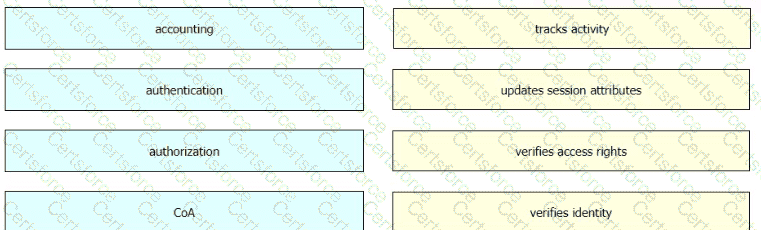
What is the primary different between AAA authentication and authorization?
Refer to the exhibit.
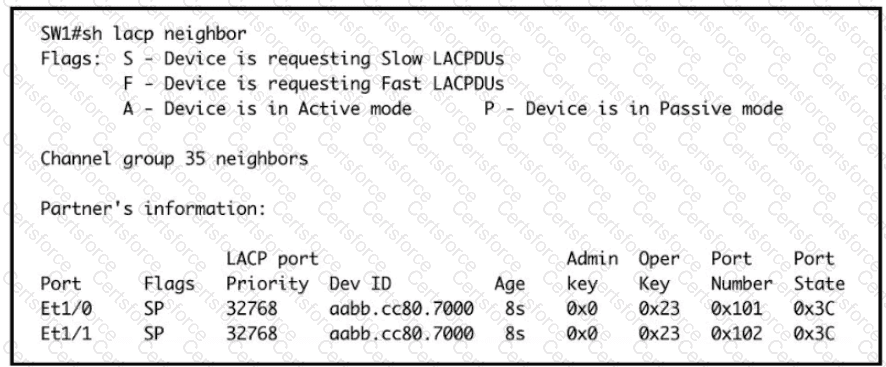
Based on the LACP neighbor status, in which mode is the SW1 port channel configured?
Drag and drop the AAA lerms from the left onto the descriptions on the right.
Refer to the exhibit.
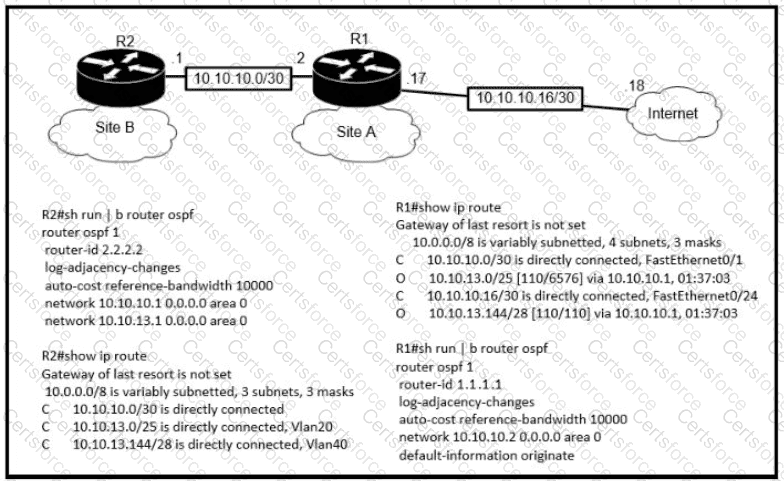
The default-information originate command is configured under the R1 OSPF configuration After testing workstations on VLAN 20 at Site B cannot reach a DNS server on the Internet Which action corrects the configuration issue?

Refer to the exhibit. Which type of JSON data is shown?
What are two reasons that cause late collisions to increment on an Ethernet interface? (Choose two)
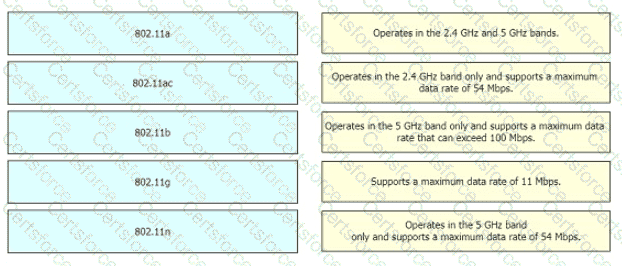
Drag and drop the 802.11 wireless standards from the left onto the matching statements on the right
What is a similarity between OM3 and OM4 fiber optic cable?
Refer to the exhibit.
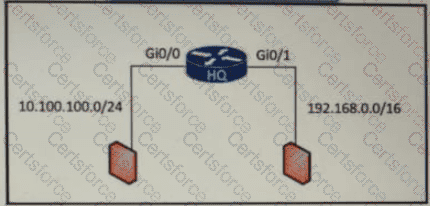
An access list is required to permit traffic from any host on interface G0/0 and deny traffic from interface G/0/1. Which access list must be applied?

Which feature on the Cisco Wireless LAN Controller when enabled restricts management access from specific networks?
Refer to the exhibit.
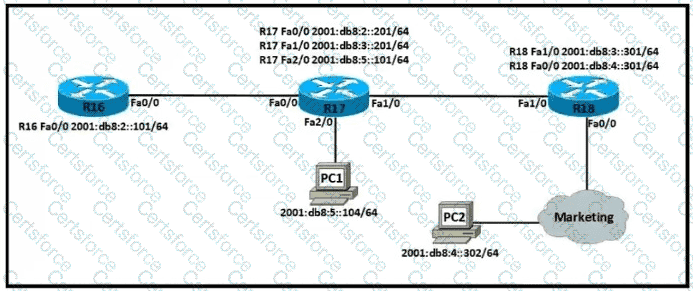
Which IPv6 configuration is required for R17 to successfully ping the WAN interface on R18?
A)
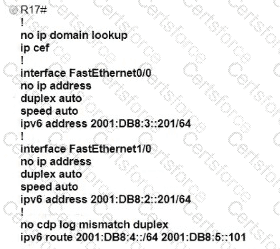
B)
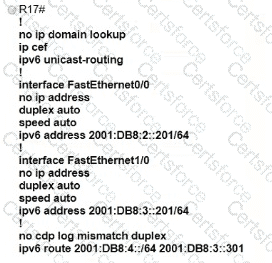
C)

D)
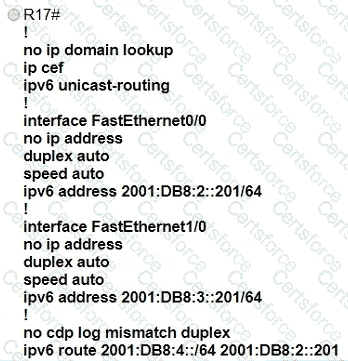
Refer to the exhibit.
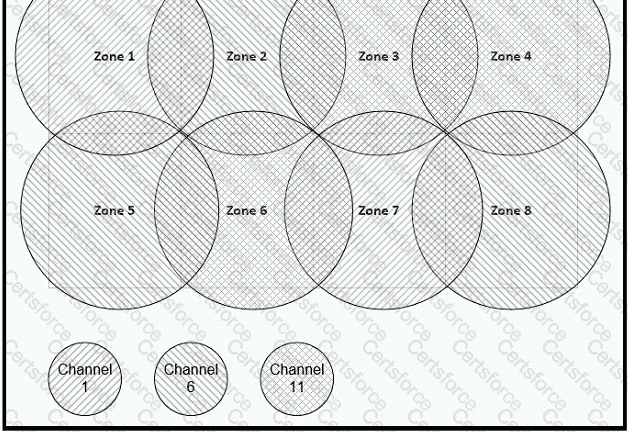
Between which zones do wireless users expect to experience intermittent connectivity?
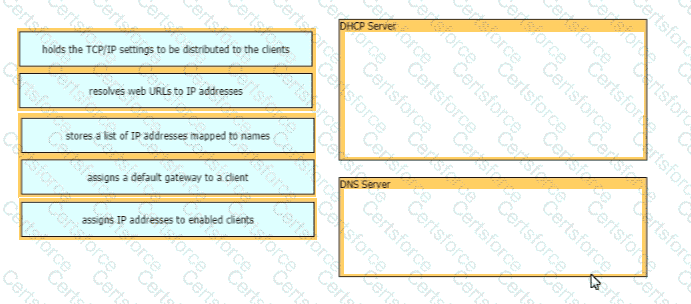
Drag and drop the functions from the left onto the correct network components on the right