Which IPv6 address block sends packets to a group address rather than a single address?
What is the purpose of traffic shaping?
Which type of wireless encryption is used for WPA2 in preshared key mode?
What are two fundamentals of virtualization? (choose two)
A manager asks a network engineer to advise which cloud service models are used so employees do not have to waste their time installing, managing, and updating software which is only used occasionally Which cloud service model does the engineer recommend?
Refer to the exhibit.
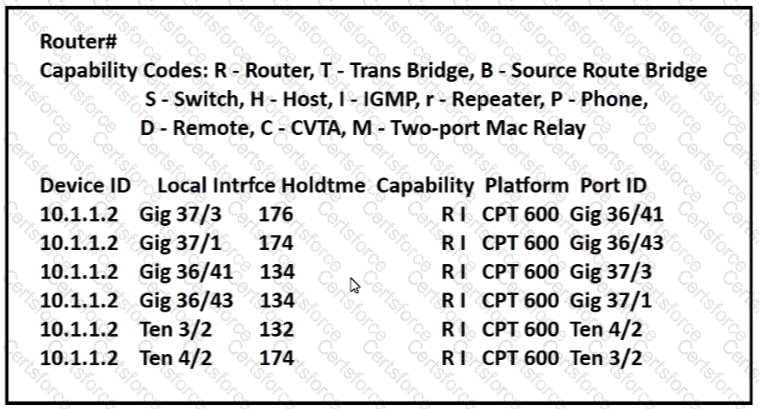
Which command provides this output?
An engineer needs to add an old switch back into a network. To prevent the switch from corrupting the VLAN database which action must be taken?
Which attribute does a router use to select the best path when two or more different routes to the same destination exist from two different routing protocols.
Which statement identifies the functionality of virtual machines?
Refer to the exhibit.
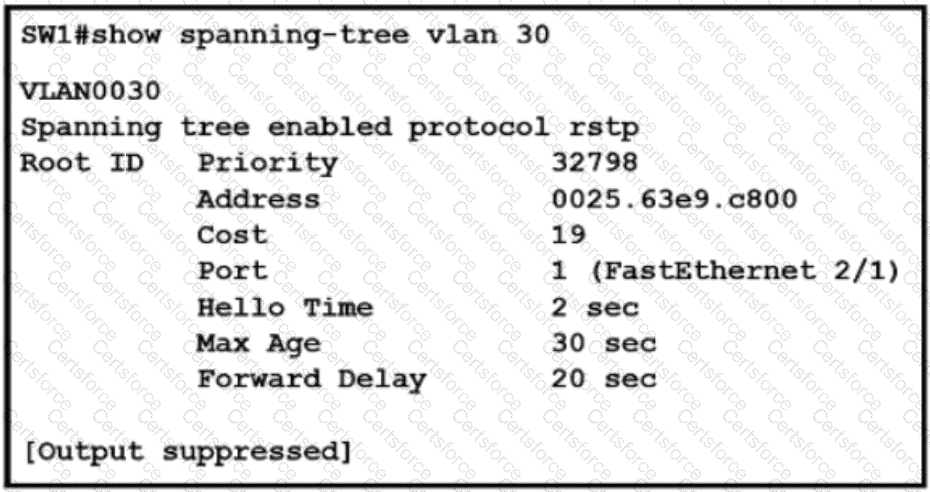
What two conclusions should be made about this configuration? (Choose two )
How does HSRP provide first hop redundancy?
Aside from discarding, which two states does the switch port transition through while using RSTP (802.1w)? (Choose two)
What does a router do when configured with the default DNS lookup settings, and a URL is entered on the CLI?
Which CRUD operation corresponds to the HTTP GET method?
When DHCP is configured on a router, which command must be entered so the default gateway is automatically distributed?
Which QoS Profile is selected in the GUI when configuring a voice over WLAN deployment?
Refer to the exhibit.
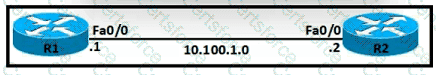
An OSPF neighbor relationship must be configured using these guidelines:
• R1 is only permitted to establish a neighbor with R2
• R1 will never participate in DR elections
• R1 will use a router-id of 101.1.1.
Which configuration must be used?
A)
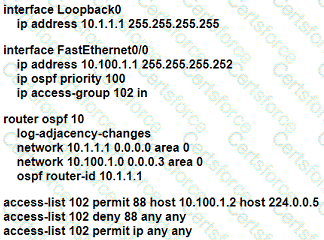
B)
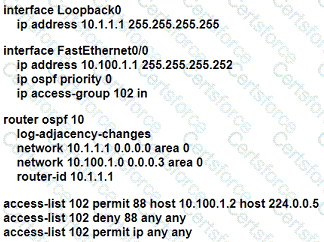
C)
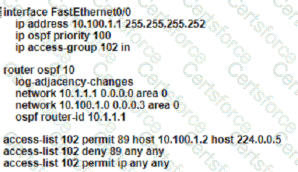
D)
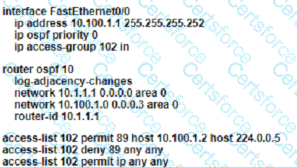
Which two command sequences must you configure on switch to establish a Layer 3 EtherChannel with an open-standard protocol? (Choose two )
What is the function of a hub-and-spoke WAN topology?
Refer to the exhibit.
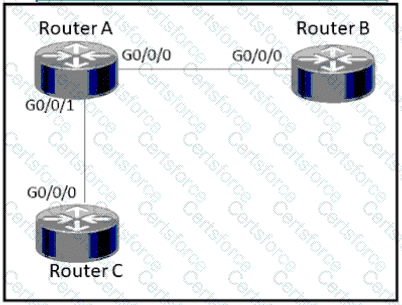
How must router A be configured so that it only sends Cisco Discovery Protocol Information to router C?
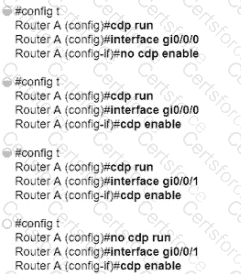
What are two benefits of controller-based networking compared to traditional networking?
Refer to the exhibit.
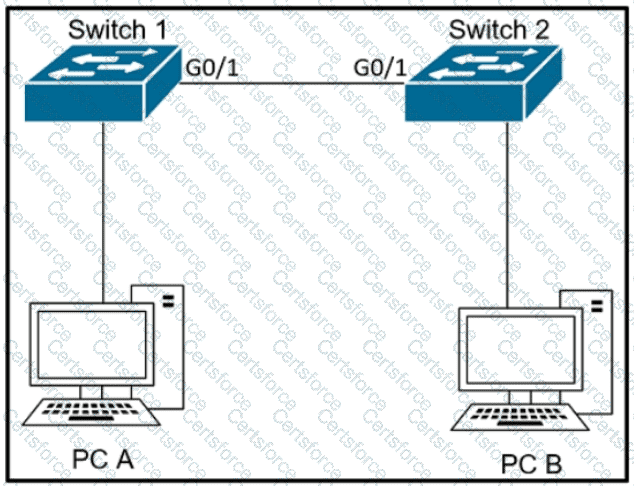
The network administrator wants VLAN 67 traffic to be untagged between Switch 1 and Switch 2 while all other VLANs are to remain tagged.
Which command accomplishes this task?
Which IPv6 address range is suitable for anycast addresses for distributed services such DHCP or DNS?
SIP-based Call Admission Control must be configured in the Cisco WLC GUI. SIP call-snooping ports are configured. Which two actions must be completed next? (Choose two.)
Refer to the exhibit.
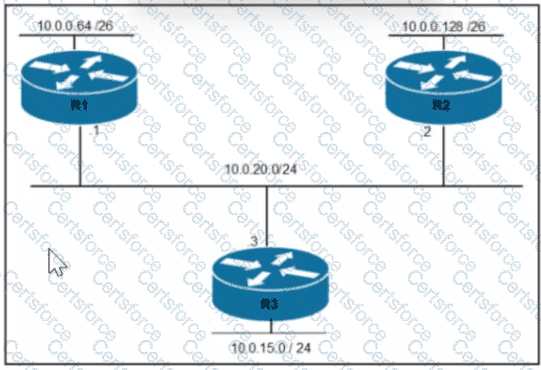
Rooter R1 is added to the network and configured with tie 10 0 0 64/26 and 10.0.20.0/24 subnets However traffic destined for the LAN on R3 is not access. Which command when executed on R1 defines a tunic route to reach the R3 LAN?
A)
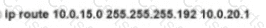
B)
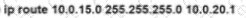
C)
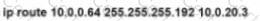
An engineer configured an OSPF neighbor as a designated router. Which state verifies the designated router is in the proper mode?
Refer to the exhibit.

Which action must be taken so that neighbofing devices rapidly discover switch Cat9300?
What is a link-local all-nodes IPv6 multicast address?
What is the collapsed layer in collapsed core architectures?
How do traditional campus device management and Cisco DNA Center device management differ in regards to deployment?
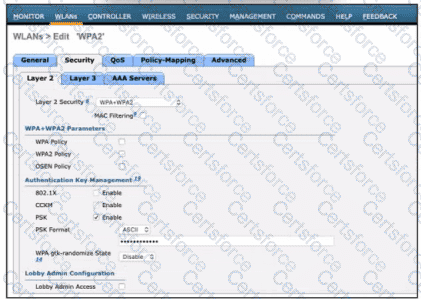
Refer to the exhibit. A network engineer is configuring a WLAN to use a WPA2 PSK and allow only specific clients to join. Which two actions must be taken to complete the process? (Choose two.)
Refer to the exhibit.
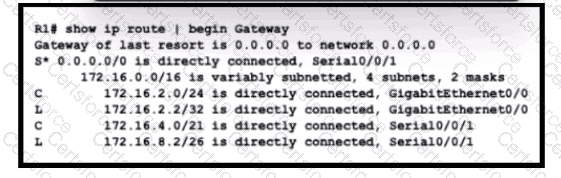
What is the subnet mask for route 172.16.4.0?
Which AP mode wirelessly connects two separate network segments each set up within a different campus building?
What are two behaviors of a point-to-point WAN topology? (Choose two.)
Aswitch receives a frame with the destination MAC address 3C:5D: 7E:9F: 1A:2B.
Switch# show ethernet-frame-and-mac-address-table
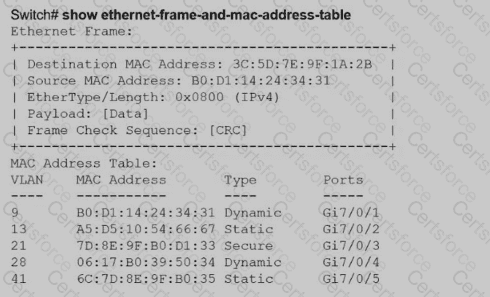
How does the switch handle the frame?
What is the maximum length of characters used in an SSID?

Refer to the exhibit. An LACP EtherChannel between two directly connected switches is in the configuration process.
Which command must be configured on switch SW2’s Gi0/1-2 interfaces to establish the channel to SW1?
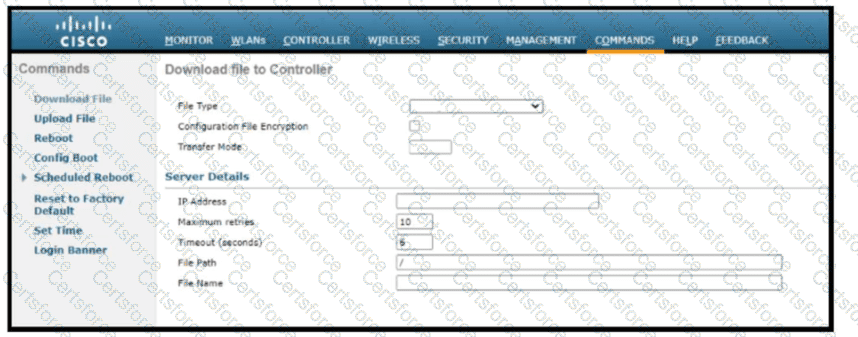
Refer to the exhibit. Which tasks must be performed on the Download File tab to install new software using TCP port 22?)
Which type of DNS record is used to specify the mail server responsible for accepting email messages on behalf of a recipient's domain?
Refer to the exhibit.
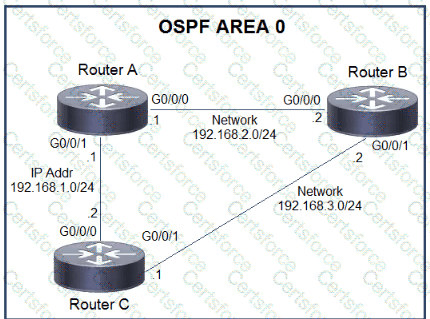
Which action must be taken to ensure that router A is elected as the DR for OSPF area 0?
A switch is forwarding a frame out of all interfaces except the interface that received the frame. What is the technical term for this process?
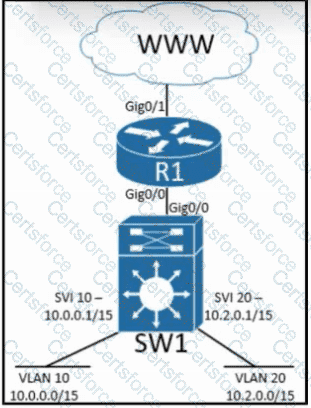
Refer to the exhibit. Inter-VLAN routing is configured on SW1. Client A is running Linux as an OS in VLAN 10 with a default gateway IP 10.0.0.1 but cannot ping client B in VLAN 20 running Windows. What action must be taken to verify that client A has the correct IP settings?
What is the function of generative AI in network operations?
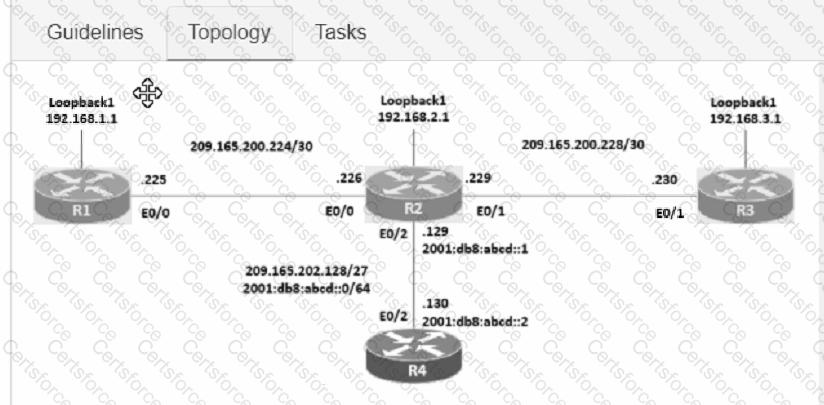
Connectivity between four routers has been established. IP connectivity must be configured in the order presented to complete the implementation. No dynamic routing protocols are included.
1. Configure static routing using host routes to establish connectivity from router R3 to the router R1 Loopback address using the source IP of 209.165.200.230.
2. Configure an IPv4 default route on router R2 destined for router R4.
3. Configure an IPv6 default router on router R2 destined for router R4.
Which plane is centralized in software-defined networking (SDN)?
What is a characteristic of RSA?
Drag and drop the device behaviors from the left onto the matching HSRP slate on the right.

Why would VRRP be implemented when configuring a new subnet in a multivendor environment?
The SW1 interface g0/1 is in the down/down state. Which two configurations are valid reasons for the interface conditions?(choose two)
Refer to the exhibit.
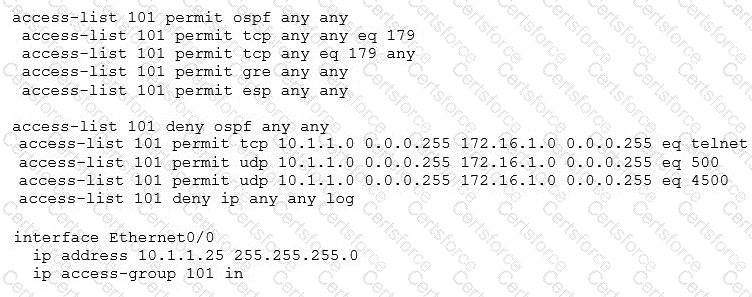
A network administrator has been tasked with securing VTY access to a router. Which access-list entry accomplishes this task?