Which of the following provides the MOST up-to-date information about the effectiveness of an organization's overall IT control environment?
Which of the following BEST balances the costs and benefits of managing IT risk*?
Which of the following analyses is MOST useful for prioritizing risk scenarios associated with loss of IT assets?
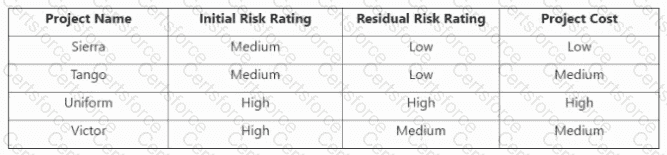
What can be determined from the risk scenario chart?
Mitigating technology risk to acceptable levels should be based PRIMARILY upon:
Senior management is deciding whether to share confidential data with the organization's business partners. The BEST course of action for a risk practitioner would be to submit a report to senior management containing the:
Which of the following BEST enables a risk practitioner to focus on risk factors that could potentially affect the results of an IT initiative?
An unauthorized individual has socially engineered entry into an organization's secured physical premises. Which of the following is the BEST way to prevent future occurrences?
Which of the following is a risk practitioner's BEST recommendation to help reduce IT risk associated with scheduling overruns when starting a new application development project?
Which of the following will BEST help to ensure the continued effectiveness of the IT risk management function within an organization experiencing high employee turnover?
Which of the following is MOST important for a risk practitioner to verify when periodically reviewing risk response action plans?
An organization's chief information officer (CIO) has proposed investing in a new. untested technology to take advantage of being first to market Senior management has concerns about the success of the project and has set a limit for expenditures before final approval. This conditional approval indicates the organization's risk:
Which of the following is the MOST essential factor for managing risk in a highly dynamic environment?
Which of the following is the FIRST step when conducting a business impact analysis (BIA)?
Which of the following aspects of an IT risk and control self-assessment would be MOST important to include in a report to senior management?
The BEST way to demonstrate alignment of the risk profile with business objectives is through:
Which of the following is the BEST method for determining an enterprise's current appetite for risk?
Which of the following is MOST important to update when an organization's risk appetite changes?
Which of the following is the MOST important component in a risk treatment plan?
Which of the following would BEST facilitate the maintenance of data classification requirements?
Which of the following is the MOST important foundational element of an effective three lines of defense model for an organization?
Which of the following is MOST important to consider before determining a response to a vulnerability?
An assessment of information security controls has identified ineffective controls. Which of the following should be the risk practitioner's FIRST course of action?
A violation of segregation of duties is when the same:
Which of the following will BEST support management reporting on risk?
An organization is considering the adoption of an aggressive business strategy to achieve desired growth From a risk management perspective what should the risk practitioner do NEXT?
Which of the following BEST reduces the likelihood of fraudulent activity that occurs through use of a digital wallet?
Which of the following should be a risk practitioner’s MOST important consideration when developing IT risk scenarios?
Which of the following should be the PRIMARY consideration when assessing the automation of control monitoring?
Which of the following should be the MOST important consideration when performing a vendor risk assessment?
Which of the following would BEST help an enterprise prioritize risk scenarios?
Which of the following would BEST help an enterprise define and communicate its risk appetite?
A risk practitioner has been asked to assess the risk associated with a new critical application used by a financial process team that the risk practitioner was a member of two years ago. Which of the following is the GREATEST concern with this request?
An organization has allowed several employees to retire early in order to avoid layoffs Many of these employees have been subject matter experts for critical assets Which type of risk is MOST likely to materialize?
Which of the following is the PRIMARY reason for logging in a production database environment?
Who should be accountable for ensuring effective cybersecurity controls are established?
Which of the following provides the MOST mitigation value for an organization implementing new Internet of Things (loT) devices?
An IT department has organized training sessions to improve user awareness of organizational information security policies. Which of the following is the BEST key performance indicator (KPI) to reflect effectiveness of the training?
Which of the following key risk indicators (KRIs) provides the BEST insight into the risk associated with IT systems being unable to meet the required availability service level in the future?
Which of the following is the PRIMARY purpose of a risk register?
Which of the following is the BEST recommendation to address recent IT risk trends that indicate social engineering attempts are increasing in the organization?
The PRIMARY objective of collecting information and reviewing documentation when performing periodic risk analysis should be to:
Which of the following is the MAIN benefit to an organization using key risk indicators (KRIs)?
During a risk assessment, a risk practitioner learns that an IT risk factor is adequately mitigated by compensating controls in an associated business process. Which of the following would enable the MOST effective management of the residual risk?
When establishing leading indicators for the information security incident response process it is MOST important to consider the percentage of reported incidents:
An organization uses a vendor to destroy hard drives. Which of the following would BEST reduce the risk of data leakage?
Which of the following is the MOST important document regarding the treatment of sensitive data?
Which risk response strategy could management apply to both positive and negative risk that has been identified?
To mitigate the risk of using a spreadsheet to analyze financial data, IT has engaged a third-party vendor to deploy a standard application to automate the process. Which of the following parties should own the risk associated with calculation errors?
A risk heat map is MOST commonly used as part of an IT risk analysis to facilitate risk: