Which of the following would be the GREATEST risk associated with a new implementation of single sign-on?
Which of the following roles would be MOST helpful in providing a high-level view of risk related to customer data loss?
The PRIMARY goal of conducting a business impact analysis (BIA) as part of an overall continuity planning process is to:
Which of the following provides The BEST information when determining whether to accept residual risk of a critical system to be implemented?
Which of the following scenarios represents a threat?
Which of the following is the PRIMARY objective of providing an aggregated view of IT risk to business management?
Which of the following would be MOST helpful in assessing the risk associated with data loss due to human vulnerabilities?
The following is the snapshot of a recently approved IT risk register maintained by an organization's information security department.
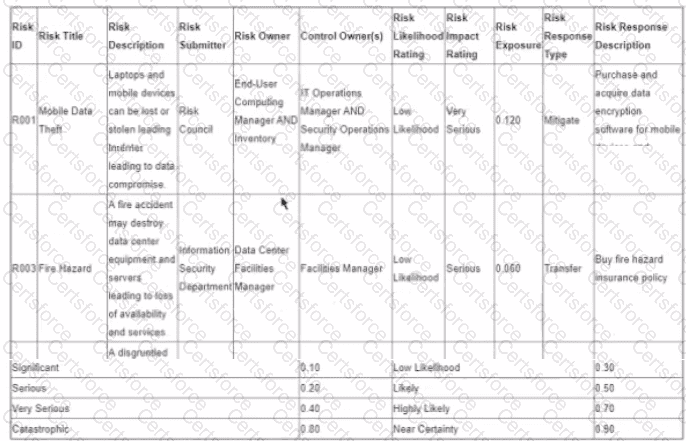
After implementing countermeasures listed in ‘’Risk Response Descriptions’’ for each of the Risk IDs, which of the following component of the register MUST change?
Who should be accountable for authorizing information system access to internal users?
An organization has adopted an emerging technology without following proper processes. Which of the following is the risk practitioner's BEST course of action to address this risk?
During a risk assessment, the risk practitioner finds a new risk scenario without controls has been entered into the risk register. Which of the following is the MOST appropriate action?
Which of the following should be management's PRIMARY focus when key risk indicators (KRIs) begin to rapidly approach defined thresholds?
Which of the following would BEST help secure online financial transactions from improper users?
Which of the following would BEST help to address the risk associated with malicious outsiders modifying application data?
An organization's risk practitioner learns a new third-party system on the corporate network has introduced vulnerabilities that could compromise corporate IT systems. What should the risk practitioner do
FIRST?
Several vulnerabilities have been identified in an organization’s core financial systems. Which of the following would be the risk practitioner’s BEST course of action?
Which of the following is a drawback in the use of quantitative risk analysis?
Senior management has requested more information regarding the risk associated with introducing a new application into the environment. Which of the following should be done FIRST?
What is the BEST recommendation to reduce the risk associated with potential system compromise when a vendor stops releasing security patches and updates for a business-critical legacy system?
An organization has detected unauthorized logins to its client database servers. Which of the following should be of GREATEST concern?
Which of the following is the BEST approach when a risk practitioner has been asked by a business unit manager to exclude an in-scope system from a risk assessment?
Which of the following should a risk practitioner recommend FIRST when an increasing trend of risk events and subsequent losses has been identified?
Which of the following should be the GREATEST concern to a risk practitioner when process documentation is incomplete?
An application owner has specified the acceptable downtime in the event of an incident to be much lower than the actual time required for the response team to recover the application. Which of the following should be the NEXT course of action?
An organization uses a biometric access control system for authentication and access to its server room. Which control type has been implemented?
Which of the following is the GREATEST benefit of a three lines of defense structure?
An organization has opened a subsidiary in a foreign country. Which of the following would be the BEST way to measure the effectiveness of the subsidiary's IT systems controls?
Participants in a risk workshop have become focused on the financial cost to mitigate risk rather than choosing the most appropriate response. Which of the following is the BEST way to address this type of issue in the long term?
An organization is planning to implement a Zero Trust model. From a cybersecunty perspective, which of the following is MOST important to ensure successful alignment with the overall inten Zero Trust?
An organizations chief technology officer (CTO) has decided to accept the risk associated with the potential loss from a denial-of-service (DoS) attack. In this situation, the risk practitioner's BEST course of action is to:
The PRIMARY reason for periodically monitoring key risk indicators (KRIs) is to:
Which of the following is the GREATEST benefit of updating the risk register to include outcomes from a risk assessment?
Which of the following would be a weakness in procedures for controlling the migration of changes to production libraries?
The MOST important measure of the effectiveness of risk management in project implementation is the percentage of projects:
Which of the following MOST effectively limits the impact of a ransomware attack?
Which of the following is the BEST approach when a risk treatment plan cannot be completed on time?
When implementing an IT risk management program, which of the following is the BEST time to evaluate current control effectiveness?
Which of the following is MOST helpful when determining whether a system security control is effective?
Which of the following is MOST helpful to management when determining the resources needed to mitigate a risk?
During the risk assessment of an organization that processes credit cards, a number of existing controls have been found to be ineffective and do not meet industry standards. The overall control environment may still be effective if:
An organization is outsourcing a key database to be hosted by an external service provider. Who is BEST suited to assess the impact of potential data loss?
What is the PRIMARY reason an organization should include background checks on roles with elevated access to production as part of its hiring process?
A highly regulated enterprise is developing a new risk management plan to specifically address legal and regulatory risk scenarios What should be done FIRST by IT governance to support this effort?
IT management has asked for a consolidated view into the organization's risk profile to enable project prioritization and resource allocation. Which of the following materials would
be MOST helpful?
Which of the following would MOST effectively enable a business operations manager to identify events exceeding risk thresholds?
An organization has implemented a policy requiring staff members to take a minimum of five consecutive days' leave per year to mitigate the risk of malicious insider activities. Which of the following is the BEST key performance indicator (KPI) of the effectiveness of this policy?
Which of the following should be given the HIGHEST priority when developing a response plan for risk assessment results?
Which of the following is MOST useful input when developing risk scenarios?
The PRIMARY advantage of implementing an IT risk management framework is the: