An analyst reviews a SIEM and generates the following report:
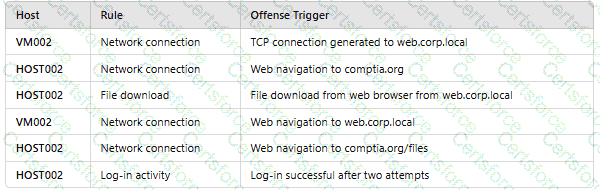
OnlyHOST002is authorized for internet traffic. Which of the following statements is accurate?
During a security assessment using an CDR solution, a security engineer generates the following report about the assets in me system:
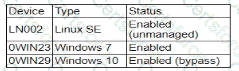
After five days, the EDR console reports an infection on the host 0WIN23 by a remote access Trojan Which of the following is the most probable cause of the infection?
After several companies in the financial industry were affected by a similar incident, they shared information about threat intelligence and the malware used for exploitation. Which of the following should the companies do to best indicate whether the attacks are being conducted by the same actor?
A security analyst is troubleshooting the reason a specific user is having difficulty accessing company resources The analyst reviews the following information:
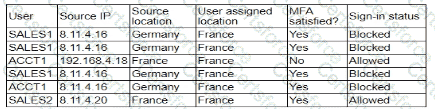
Which of the following is most likely the cause of the issue?
During a recent audit, a company's systems were assessed- Given the following information:
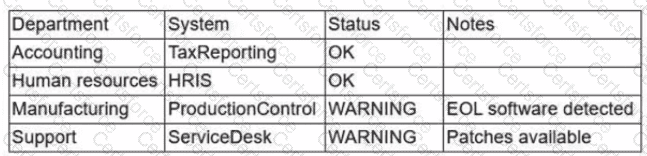
Which of the following is the best way to reduce the attack surface?
An audit finding reveals that a legacy platform has not retained loos for more than 30 days The platform has been segmented due to its interoperability with newer technology. As a temporarysolution, the IT department changed the log retention to 120 days. Which of the following should the security engineer do to ensure the logs are being properly retained?
A company SIEM collects information about the log sources. Given the following report information:
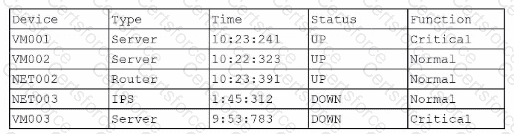
Which of the following actions should a security engineer take to enhance the security monitoring posture?
A global organization is reviewing potential vendors to outsource a critical payroll function. Each vendor's plan includes using local resources in multiple regions to ensure compliance with all regulations. The organization's Chief Information Security Officer is conducting a risk assessment on the potential outsourcing vendors' subprocessors. Which of the following best explains the need for this risk assessment?
A security administrator needs to automate alerting. The server generates structured log files that need to be parsed to determine whether an alarm has been triggered Given the following code function:
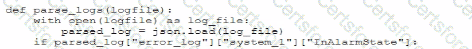
Which of the following is most likely the log input that the code will parse?
A)
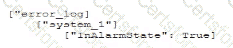
B)

C)
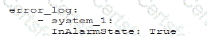
D)
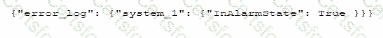
A security officer received several complaints from usersabout excessive MPA push notifications at night The security team investigates and suspects malicious activities regarding user account authentication Which of the following is the best way for the security officer to restrict MI~A notifications''