Asoftware company deployed a new application based on its internal code repository Several customers are reporting anti-malware alerts on workstations used to test the application Which of the following is the most likely cause of the alerts?
A SOC analyst is investigating an event in which a penetration tester was able to successfully create and execute a payload. The analyst pulls the following command history from the affected server-
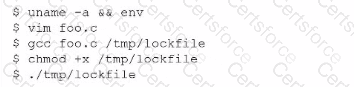
Which of the following should the analyst implement lo improve the security of the server?
Which of the following tests explains why AI output could be inaccurate?
A compliance officer is reviewing the data sovereignty laws in several countries where the organization has no presence Which of the following is the most likely reason for reviewing these laws?
During a security review for the CI/CD process, a security engineer discovers the following information in a testing repository from the company:
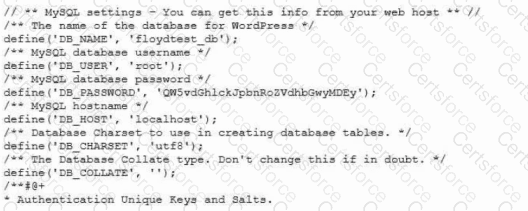
Which of the following options is the best countermeasure to prevent this issue in the future?
Engineers at a cloud service provider can now access newly deployed customer environments from their personal laptops. The engineers are concerned that unmanaged systems may present unknown vulnerabilities to customer environments, which might become a significant liability to the service provider. Which of the following deployments provides the most secure solution to prevent access through non-authorized endpoints?
Recent repents indicate that a software tool is being exploited Attackers were able to bypass user access controls and load a database. A security analyst needs to find the vulnerability and recommend a mitigation. The analyst generates the following output:
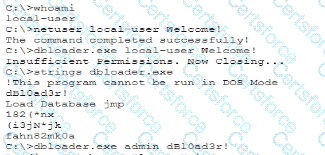
Which of the following would the analyst most likely recommend?
Due to locality and budget constraints, an organization’s satellite office has a lower bandwidth allocation than other offices. As a result, the local securityinfrastructure staff is assessing architectural options that will help preserve network bandwidth and increase speed to both internal and external resources while not sacrificing threat visibility. Which of the following would be the best option to implement?
After an organization met with its ISAC, the organization decided to test the resiliency of its security controls against a small number of advanced threat actors. Which of the following will enable the security administrator to accomplish this task?
A building camera is remotely accessed and disabled from the remote console application during off-hours. A security analyst reviews the following logs:
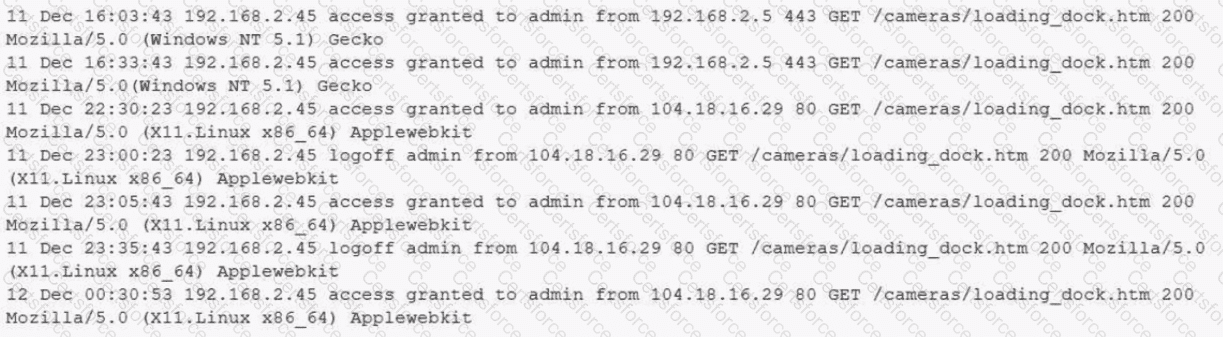
A security architect is onboarding a new EDR agent on servers that traditionally do not have internet access. In order for the agent to receive updates and report back to the management console, some changes must be made. Which of the following should the architect do to best accomplish this requirement? (Select two).