A SOC analyst is investigating an event in which a penetration tester was able to successfully create and execute a payload. The analyst pulls the following command history from the affected server-
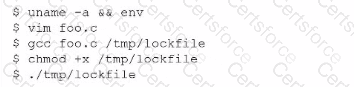
Which of the following should the analyst implement lo improve the security of the server?
Submit