A security analyst wants to use lessons learned from a poor incident response to reduce dwell lime in the future The analyst is using the following data points
Which of the following would the analyst most likely recommend?
A company migrated a critical workload from its data center to the cloud. The workload uses a very large data set that requires computational-intensive data processing. The business unit that uses the workload is projecting the following growth pattern:
• Storage requirements will double every six months.
• Computational requirements will fluctuate throughout the year.
• Average computational requirements will double every year.
Which of the following should the company do to address the business unit's requirements?
During a periodic internal audit, a company identifies a few new, critical security controls that are missing. The company has a mature risk management program in place, and the following requirements must be met:
The stakeholders should be able to see all the risks.
The risks need to have someone accountable for them.
Which of the following actions should the GRC analyst take next?
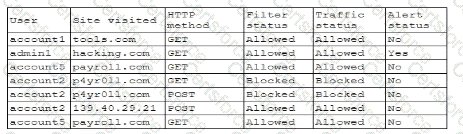
A user submits a help desk ticket stating then account does not authenticatesometimes. An analyst reviews the following logs for the user:
Which of the following best explains the reason the user's access is being denied?
An engineering team determines the cost to mitigate certain risks is higher than the asset values The team must ensure the risks are prioritized appropriately. Which of the following is the best way to address the issue?
A developer needs toimprove the cryptographic strength of a password-storage component in a web application without completely replacing the crypto-module. Which of the following is the most appropriate technique?
A company detects suspicious activity associated with external connections Security detection tools are unable tocategorize this activity. Which of the following is the best solution to help the company overcome this challenge?
An organization recently implemented a policy that requires all passwords to be rotated every 90 days. An administrator observes a large volume of failed sign-on logs from multiple servers that are often accessed by users. The administrator determines users are disconnecting from the RDP session but not logging off. Which of the following should the administrator do to prevent account lockouts?
A security administrator is performing a gap assessment against a specific OS benchmark The benchmark requires the following configurations be applied to endpoints:
• Full disk encryption
* Host-based firewall
• Time synchronization
* Password policies
• Application allow listing
* Zero Trust application access
Which of the following solutions best addresses the requirements? (Select two).
Operational technology often relies upon aging command, control, and telemetry subsystems that were created with the design assumption of: