A security engineer is developing a solution to meet the following requirements?
• All endpoints should be able to establish telemetry with a SIEM.
• All endpoints should be able to be integrated into the XDR platform.
• SOC services should be able to monitor the XDR platform
Which of the following should the security engineer implement to meet the requirements?
A security engineer receives an alert from the threat intelligence platform with the following information:
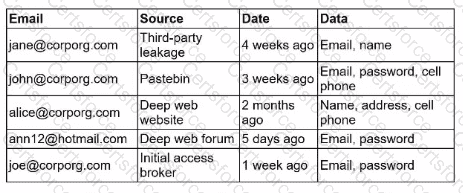
Which of the following actions should the security engineer do first?
A software engineer is creating a CI/CD pipeline to support the development of a web application The DevSecOps team is required to identify syntax errors Which of the following is the most relevant to the DevSecOps team's task'
A threat intelligence company's business objective is to allow customers to integrate data directly to different TIPs through an API. The company would like to address as many of the following objectives as possible:
• Reduce compute spend as much as possible.
• Ensure availability for all users.
• Reduce the potential attack surface.
• Ensure the integrity of the data provided.
Which of the following should the company consider to best meet the objectives?
A company hosts a platform-as-a-service solution with a web-based front end, through which customer interact with data sets. A security administrator needs to deploy controls to prevent application-focused attacks. Which of the following most directly supports the administrator's objective'
A vulnerability scan was performed on a website, and the following encryption suites were found:
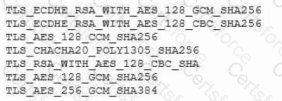
Which of the following actions will remediate the vulnerability?
A security architect is investigating instances of employees who had their phones stolen in public places through seemingly targeted attacks. Devices are able to access company resources such as email and internal documentation, some of which can persist in application storage. Which of the following would best protect the company from information exposure? (Select two).
An organization is researching the automation capabilities for systems within an OT network. A security analyst wants to assist with creating secure coding practices and would like to learn about the programming languages used on the PLCs. Which of the following programming languages is the most relevant for PLCs?
An enterprise is deploying APIs that utilize a private key and a public key to ensure the connection string is protected. To connect to the API, customers must use the private key. Which of the following would best secure the REST API connection to the database while preventing the use of a hard-coded string in the request string?
A company is having issues with its vulnerability management program New devices/lPs are added and dropped regularly, making the vulnerability report inconsistent Which of the following actions should the company lake to most likely improve the vulnerability management process'