A network engineer wants to add a third-party threat feed into the Cisco FMC for enhanced threat detectionWhich action should be taken to accomplish this goal?
An engineer is configuring Cisco Security Devices by using Cisco Secure Firewall Management Center. Which configuration command must be run to compare the CA certificate bundle on the local system to the latest CA bundle from the Cisco server?
In a multi-tennent deployment where multiple domains are in use. which update should be applied outside of the Global Domain?
An organization has noticed that malware was downloaded from a website that does not currently have a known bad reputation. How will this issue be addresses globally in the quickest way possible and with the least amount of impact?
Which CLI command is used to generate firewall debug messages on a Cisco Firepower?
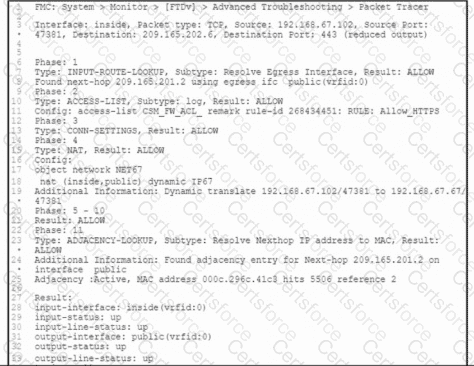

Refer to the exhibit. A client that has IP address 192.168.67.102 reports issues when connecting to a remote server. Based on the topology and output of packet tracer tool, which action resolves the connectivity issue?
A network engineer must monitor threat events from the console of Cisco Secure Firewall Management Center. The engineer integrates the Cisco Secure Firewall Malware Defense in Secure Firewall Management Center. Which action must the engineer take next?
Which two actions can be used in an access control policy rule? (Choose two.)
An organization wants to secure traffic from their branch office to the headquarter building using Cisco Firepower devices, They want to ensure that their Cisco Firepower devices are not wasting resources on inspecting the VPN traffic. What must be done to meet these requirements?
A network administrator reviews the file report for the last month and notices that all file types, except exe. show a disposition of unknown. What is the cause of this issue?