Due to an Increase in malicious events, a security engineer must generate a threat report to include intrusion in events, malware events, and security intelligence events. How Is this information collected in a single report?
A security engineer is configuring an Access Control Policy for multiple branch locations. These locations share a common rule set and utilize a network object called INSIDE_NET which contains the locally significant internal network subnets at each location. Which technique will retain the policy consistency at each location but allow only the locally significant network subnet within the applicable rules?
An engineer wants to change an existing transparent Cisco FTD to routed mode.
The device controls traffic between two network segments. Which action is mandatory to allow hosts to reestablish communication between these two segments after the change?
An engineer wants to add an additional Cisco FTD Version 6.2.3 device to their current 6.2.3 deployment to create a high availability pair.
The currently deployed Cisco FTD device is using local management and identical hardware including the available port density to enable the failover and stateful links required in a proper high availability deployment. Which action ensures that the environment is ready to pair the new Cisco FTD with the old one?
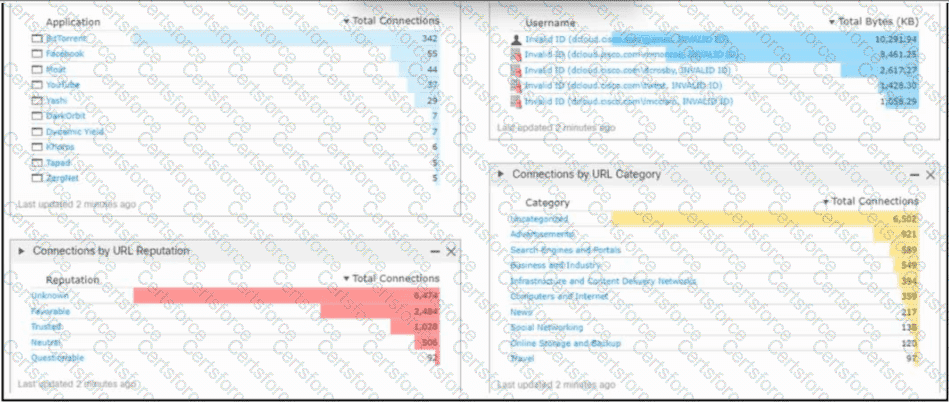
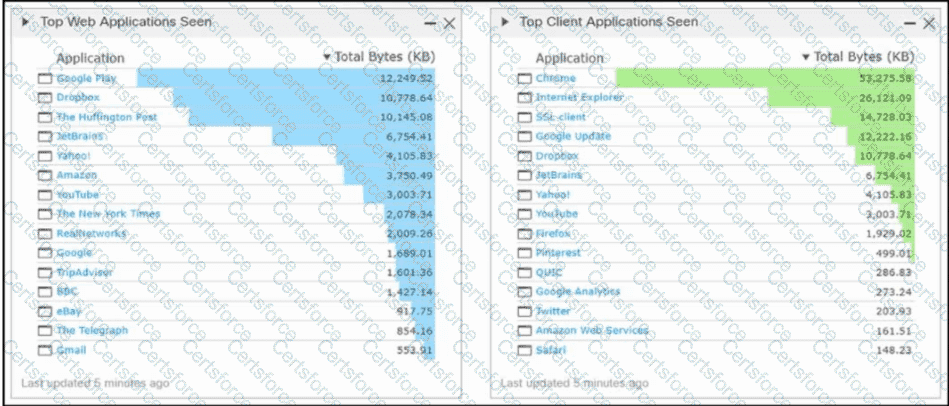
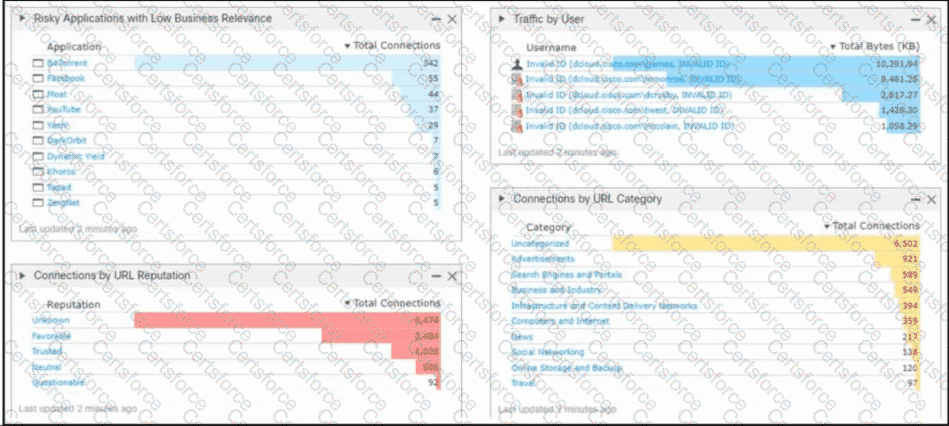
Refer to the exhibit. An engineer analyzes a Cisco Firepower Management Center dashboard. Which action must be taken by the user to decrease the risk of data loss?
An engineer is configuring two new Cisco FTD devices to replace the existing high availability firewall pair in a highly secure environment. The information exchanged between the FTD devices over the failover link must be encrypted. Which protocol supports this on the Cisco FTD?
Which firewall design allows a firewall to forward traffic at layer 2 and layer 3 for the same subnet?
Which two statements about bridge-group interfaces in Cisco FTD are true? (Choose two.)
An engineer is configuring a Cisco Secure Firewall Threat Defense device and warns to create a new intrusion rule based on the detection of a specific pattern in the data payload for a new zero-day exploit. Which keyword type must be used to add a Line that identifies the author of the rule and the date it was created?
A security engineer manages a firewall console and an endpoint console and finds it challenging and the consuming to review events and modify blocking of specific files in both consoles. Which action must the engineer take to streamline this process?