A network administrator is concerned about (he high number of malware files affecting users' machines. What must be done within the access control policy in Cisco FMC to address this concern?
An analyst is reviewing the Cisco FMC reports for the week. They notice that some peer-to-peer applications are being used on the network and they must identify which poses the greatest risk to the environment. Which report gives the analyst this information?
An administrator is setting up Cisco Firepower to send data to the Cisco Stealthwatch appliances. The NetFlow_Set_Parameters object is already created, but NetFlow is not being sent to the flow collector. What must be done to prevent this from occurring?
Which Cisco Firepower rule action displays an HTTP warning page?
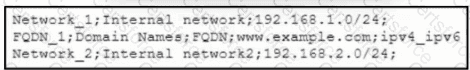
Refer to the exhibit. An engineer must import three network objects into the Cisco Secure Firewall Management Center by using a CSV file. Which header must be configured in the CSV file to accomplish the task?
What is the maximum SHA level of filtering that Threat Intelligence Director supports?
An engineer Is configuring a Cisco FTD device to place on the Finance VLAN to provide additional protection tor company financial data. The device must be deployed without requiring any changes on the end user workstations, which currently use DHCP lo obtain an IP address. How must the engineer deploy the device to meet this requirement?
What is a characteristic of bridge groups on a Cisco FTD?
A network administrator is implementing an active/passive high availability Cisco FTD pair.
When adding the high availability pair, the administrator cannot select the secondary peer.
What is the cause?
Refer to the exhibit.

An organization has an access control rule with the intention of sending all social media traffic for inspection After using the rule for some time, the administrator notices that the traffic is not being inspected, but is being automatically allowed What must be done to address this issue?