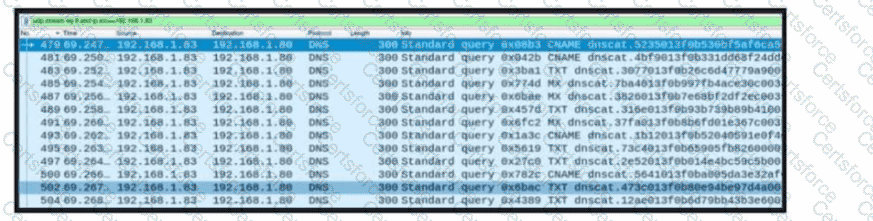
Refer to the exhibit. A network engineer received a report that a host is communicating with unknown domains on the internet. The network engineer collected packet capture but could not determine the technique or the payload used. What technique is the attacker using?
What matches the regular expression c(rgr)+e?
Which management concept best describes developing, operating, maintaining, upgrading, and disposing of all resources?
An engineer is sharing folders and files with different departments and got this error: "No such file or directory". What must the engineer verify next?
Which items is an end-point application greylist used?
In digital communications, which method is recommended for securely exchanging public keys between users T0n2262144790 and D4n4126220794?
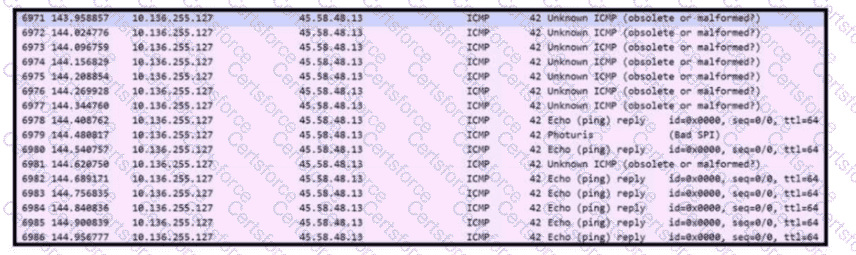
Refer to the exhibit. An engineer received a ticket to analyze unusual network traffic. What is occurring?
Refer to the exhibit.

Which type of log is displayed?
Which two elements of the incident response process are stated in NIST Special Publication 800-61 r2? (Choose two.)
How does an SSL certificate impact security between the client and the server?