Which are two denial-of-service attacks? (Choose two.)
Which action should be taken if the system is overwhelmed with alerts when false positives and false negatives are compared?
Refer to the exhibit.
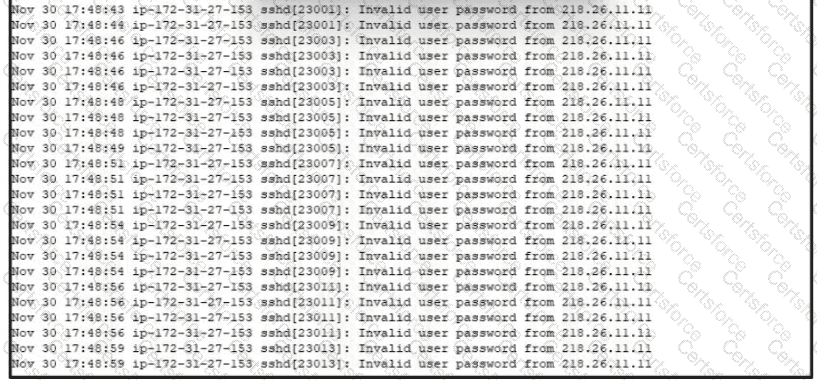
A security analyst is investigating unusual activity from an unknown IP address Which type of evidence is this file1?
What is a difference between a threat and a risk?
Which vulnerability type is used to read, write, or erase information from a database?
What is a difference between signature-based and behavior-based detection?
What is the difference between a threat and a risk?
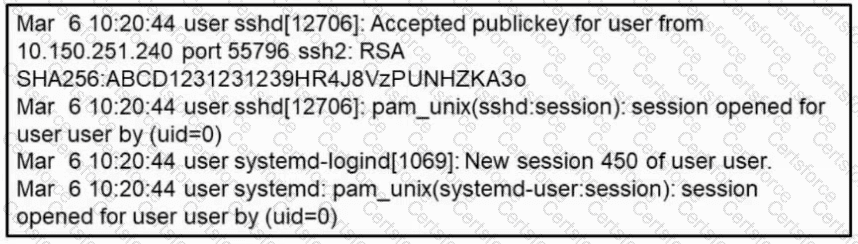
Refer to the exhibit. What occurred on this system based on this output?
Which type of evasion technique is accomplished by separating the traffic into smaller segments before transmitting across the network?
Refer to the exhibit.
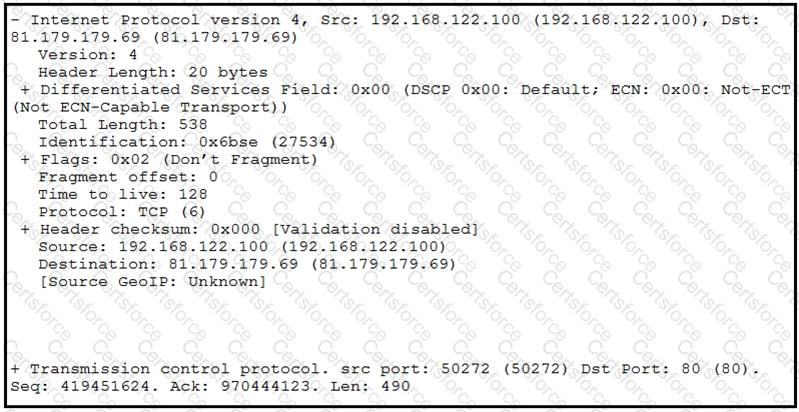
What should be interpreted from this packet capture?