An analyst see that this security alert "Default-Botnet-Communication-Detection-By-Endpoint" has been raised from the IPS. The analyst checks and finds that an endpoint communicates to the C&C. How must an impact from this event be categorized?
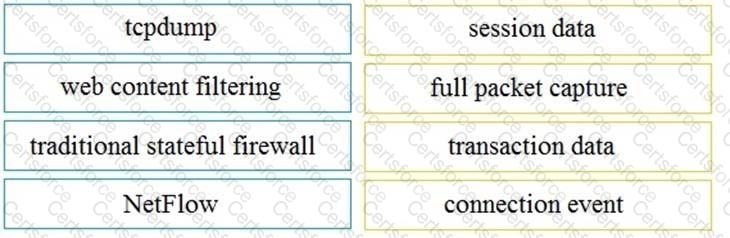
Drag and drop the technology on the left onto the data type the technology provides on the right.
Developers must implement tasks on remote Windows environments. They decided to use scripts for enterprise applications through PowerShell. Why does the functionality not work?
Which type of data consists of connection level, application-specific records generated from network traffic?
Which SOC metric represents the time to stop the incident from causing further damage to systems or data?
Which data format is the most efficient to build a baseline of traffic seen over an extended period of time?
What is an advantage of symmetric over asymmetric encryption?
Refer to the exhibit.

In which Linux log file is this output found?
What is the purpose of command and control for network-aware malware?
A company receptionist received a threatening call referencing stealing assets and did not take any action assuming it was a social engineering attempt. Within 48 hours, multiple assets were breached, affecting the confidentiality of sensitive information. What is the threat actor in this incident?