Which attack represents the evasion technique of resource exhaustion?
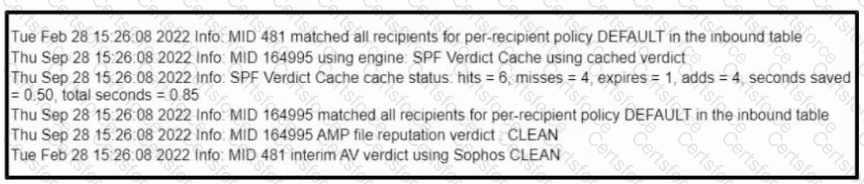
Refer to the exhibit. Which type of data filtering is provided?
Refer to the exhibit.
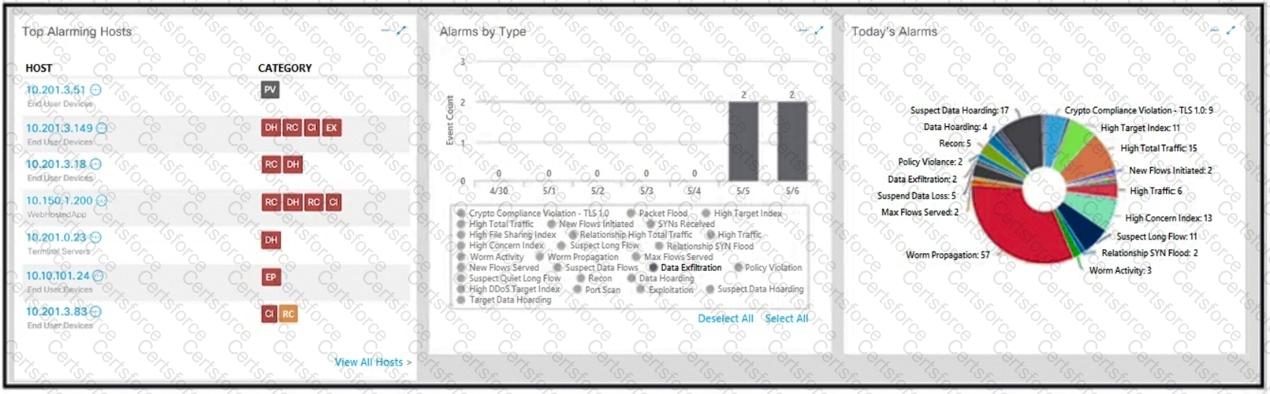
What is the potential threat identified in this Stealthwatch dashboard?
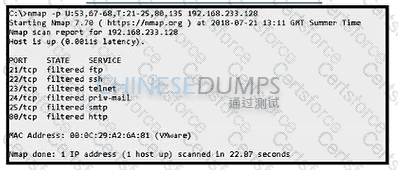
Refer to the exhibit. An attacker scanned the server using Nmap. What did the attacker obtain from this scan?
How low does rule-based detection differ from behavioral detection?
An analyst received a ticket regarding a degraded processing capability for one of the HR department's servers. On the same day, an engineer noticed a disabled antivirus software and was not able to determine when or why it occurred. According to the NIST Incident Handling Guide, what is the next phase of this investigation?
Refer to the exhibit.
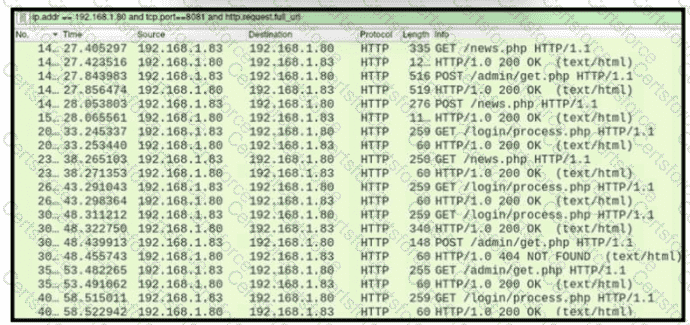
A network administrator is investigating suspicious network activity by analyzing captured traffic. An engineer notices abnormal behavior and discovers that the default user agent is present in the headers of requests and data being transmitted What is occurring?
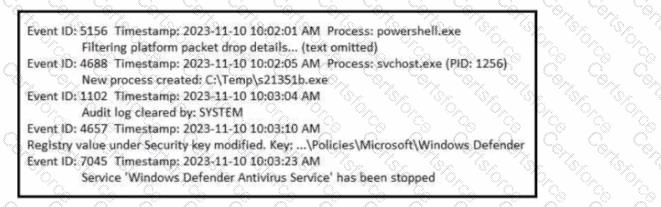
Refer to the exhibit. A SOC analyst is examining the Windows security logs of one of the endpoints. What is the possible reason for this event log?
Which tool is used by threat actors on a webpage to take advantage of the software vulnerabilities of a system to spread malware?
What is the difference between vulnerability and risk?