A user reports difficulties accessing certain external web pages. When an engineer examines traffic to and from the external domain in full packet captures, they notice that many SYNs have the same sequence number, source, and destination IP address, but they have different payloads. What is causing this situation?
What is the difference between an attack vector and attack surface?
What describes the impact of false-positive alerts compared to false-negative alerts?
Refer to the exhibit.
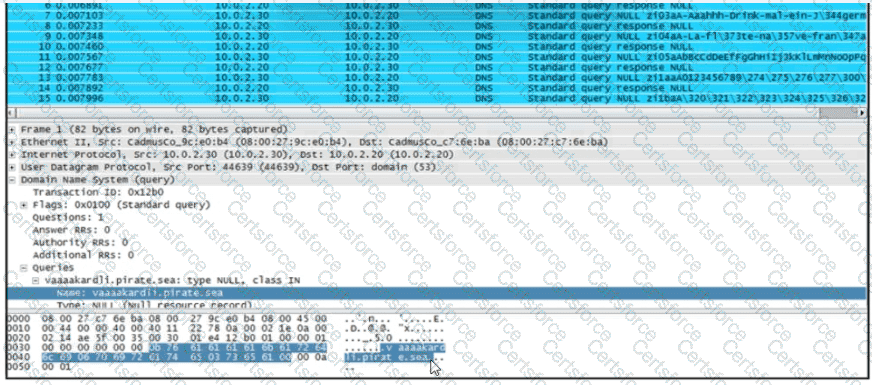
What is occurring?
Which CVSS metric group identifies other components that are affected by a successful security attack?
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
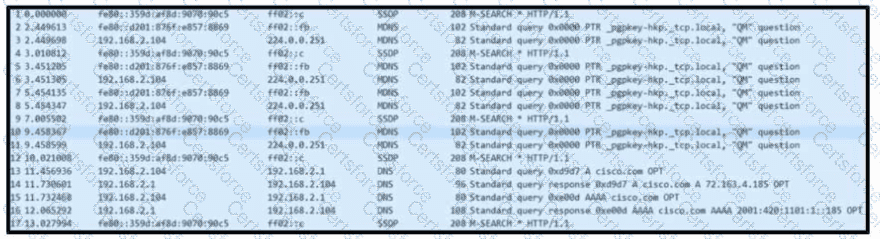
Refer to the exhibit. Based on the .pcap file, which DNS server is used to resolve cisco.com?
An engineer needs to fetch logs from a proxy server and generate actual events according to the data received. Which technology should the engineer use to accomplish this task?
Refer to the exhibit.
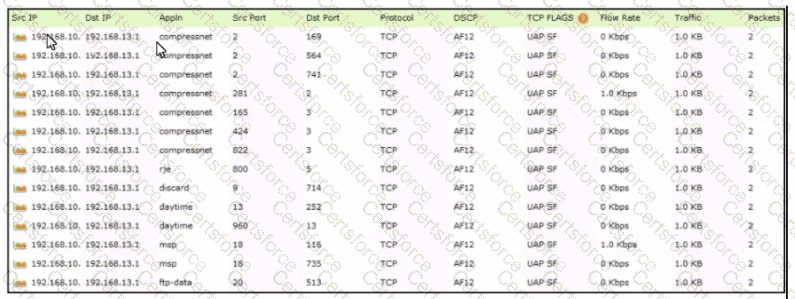
Which tool was used to generate this data?
What is the difference between inline traffic interrogation (TAPS) and traffic mirroring (SPAN)?