A security engineer must determine why a new core application does not work as desired The client can send requests toward the application server but receives no response One of the requirements is to gather all packets Data needs to be reliable without any delay or packet drops Which solution best meets this need?
In a SOC environment, what is a vulnerability management metric?
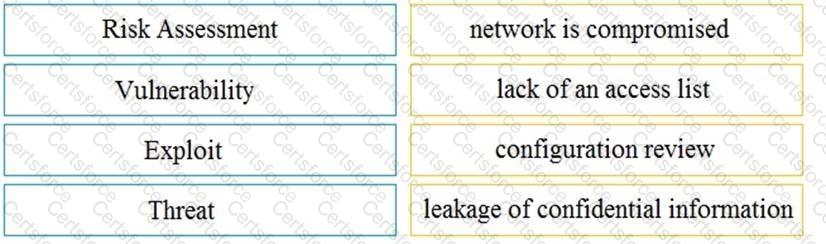
Drag and drop the security concept on the left onto the example of that concept on the right.
What is the difference between the ACK flag and the RST flag?
How does certificate authority impact a security system?

Refer to the exhibit A penetration tester runs the Nmap scan against the company server to uncover possible vulnerabilities and exploit them Which two elements can the penetration tester identity from the scan results? (Choose two.)
An analyst received a ticket about degraded processing capability for one of the HR department's servers. On the same day, an engineer noticed disabled antivirus software and could not determine when or why it occurred. According to the NIST Incident Handling Guide, what is the next phase of this investigation?
A vulnerability analyst is performing the monthly scan data review Output data is very big and getting bigger each month The analyst decides to create a more efficient process to complete the task on time All false positives and true positives are excluded from the results The remaining findings will be assigned to a technical team for further remediation What is the result of such activity?
What is the difference between inline traffic interrogation and traffic mirroring?
An analyst performs traffic analysis to detect data exfiltration and identifies a high frequency of DNS requests in a small period of time Which technology makes this behavior feasible?