What should a security analyst consider when comparing inline traffic interrogation with traffic tapping to determine which approach to use in the network?
Which security technology guarantees the integrity and authenticity of all messages transferred to and from a web application?
Refer to the exhibit.
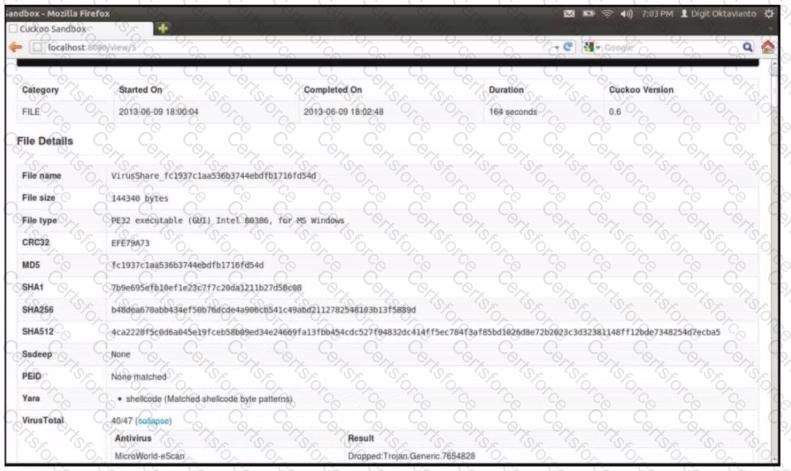
What does this Cuckoo sandbox report indicate?
How is SQL injection prevented?
An engineer runs a suspicious file in a sandbox analysis tool to see the outcome. The analysis report shows that outbound callouts were made post infection.
Which two pieces of information from the analysis report are needed to investigate the callouts? (Choose two.)
Which step in the incident response process researches an attacking host through logs in a SIEM?
What is the difference between attack surface and vulnerability?
What are two categories of DDoS attacks? (Choose two.)
What is threat hunting?
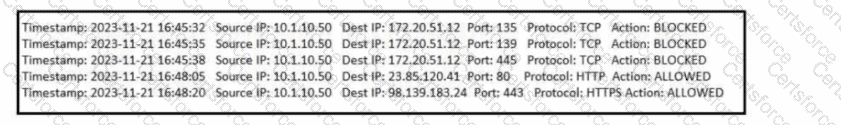
Refer to the exhibit. What type of event is occurring?