What makes HTTPS traffic difficult to monitor?
Refer to the exhibit.
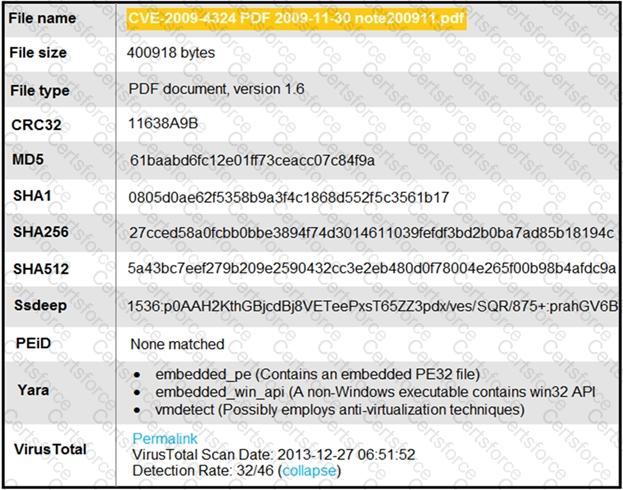
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?
Which piece of information is needed for attribution in an investigation?
Refer to the exhibit.
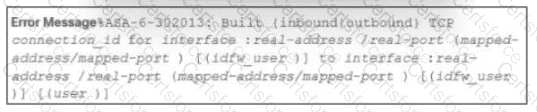
During the analysis of a suspicious scanning activity incident, an analyst discovered multiple local TCP connection events Which technology provided these logs?
A network engineer informed a security team of a large amount of traffic and suspicious activity from an unknown source to the company DMZ server The security team reviewed the data and identified a potential DDoS attempt According to NIST, at which phase of incident response is the security team?
Which type of data is used to detect anomalies in the network?
Which category relates to improper use or disclosure of PII data?
What should an engineer use to aid the trusted exchange of public keys between user tom0411976943 and dan1968754032?
Which security technology allows only a set of pre-approved applications to run on a system?
Which difficulty occurs when log messages are compared from two devices separated by a Layer 3 device that performs Network Address Translation?