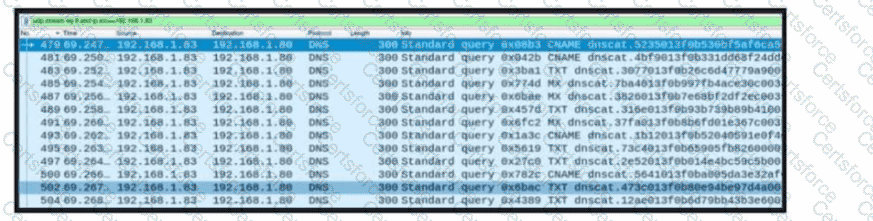
Refer to the exhibit. A network engineer received a report that a host is communicating with unknown domains on the internet. The network engineer collected packet capture but could not determine the technique or the payload used. What technique is the attacker using?
Submit