Which type of attack is social engineering?
Refer to the exhibit.

What are two indications of the Cisco Firepower Services Module configuration?
(Choose two.)
What is a benefit of using GET VPN over FlexVPN within a VPN deployment?
What is the purpose of the Cisco Endpoint IoC feature?
What provides the ability to program and monitor networks from somewhere other than the DNAC GUI?
Which solution for remote workers enables protection, detection, and response on the endpoint against known and unknown threats?
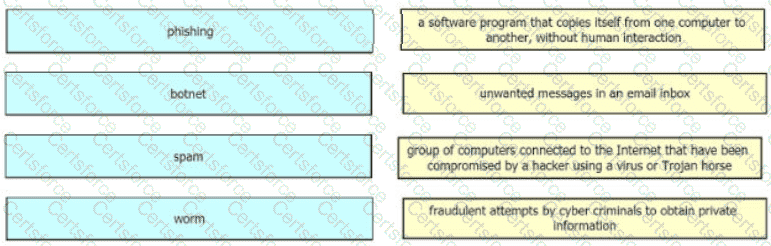
Drag and drop the common security threats from the left onto the definitions on the right.
What is the result of the ACME-Router(config)#login block-for 100 attempts 4 within 60 command on a Cisco IOS router?
Which Cisco solution extends network visibility, threat detection, and analytics to public cloud environments?
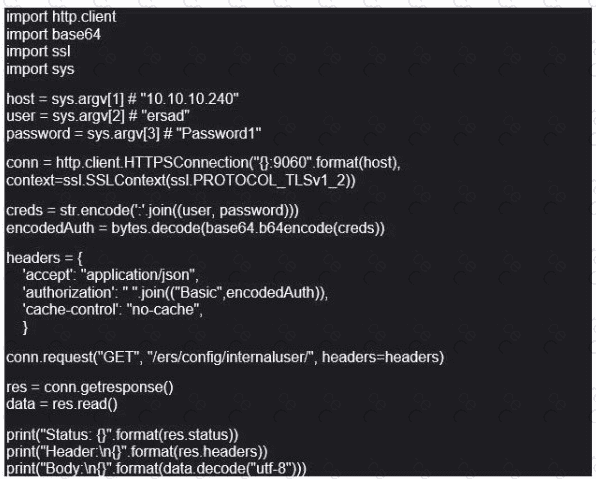
Refer to the exhibit. What does this Python script accomplish?
How is DNS tunneling used to exfiltrate data out of a corporate network?
When network telemetry is implemented, what is important to be enabled across all network infrastructure devices to correlate different sources?
Which endpoint protection and detection feature performs correlation of telemetry, files, and intrusion
events that are flagged as possible active breaches?
What is a prerequisite when integrating a Cisco ISE server and an AD domain?
A network engineer must create an access control list on a Cisco Adaptive Security Appliance firewall. The access control list must permit HTTP traffic to the internet from the organization's inside network 192.168.1.0/24. Which IOS command must oe used to create the access control list?