What is a capability of Cisco ASA Netflow?
What is the term for when an endpoint is associated to a provisioning WLAN that is shared with guest
access, and the same guest portal is used as the BYOD portal?
What is a difference between DMVPN and sVTI?
Which two fields are defined in the NetFlow flow? (Choose two)
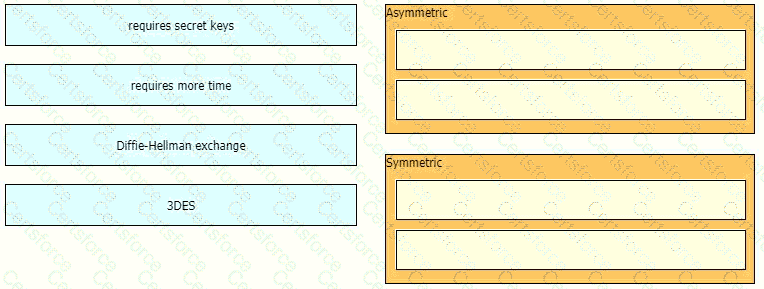
Drag and drop the descriptions from the left onto the encryption algorithms on the right.
What must be configured on Cisco Secure Endpoint to create a custom detection tile list to detect and quarantine future files?
A network administrator is configuring SNMPv3 on a new router. The users have already been created;
however, an additional configuration is needed to facilitate access to the SNMP views. What must the
administrator do to accomplish this?
Which feature is leveraged by advanced antimalware capabilities to be an effective endpomt protection platform?
What are two ways a network administrator transparently identifies users using Active Directory on the Cisco WSA? (Choose two.) The eDirectory client must be installed on each client workstation.
Which solution detects threats across a private network, public clouds, and encrypted traffic?
An engineer is implementing DHCP security mechanisms and needs the ability to add additional attributes to profiles that are created within Cisco ISE Which action accomplishes this task?
What are two recommended approaches to stop DNS tunneling for data exfiltration and command and control call backs? (Choose two.)
An engineer implements Cisco CloudLock to secure a Microsoft Office 365 application in the cloud. The engineer must configure protection for corporate files in case of any incidents. Which two actions must be taken to complete the implementation? (Choose two.)
Drag and drop the VPN functions from the left onto the description on the right.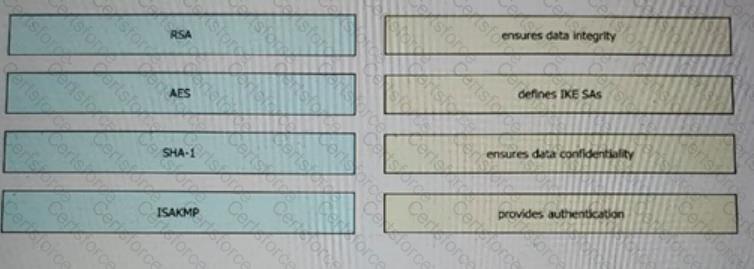
When a Cisco WSA checks a web request, what occurs if it is unable to match a user-defined policy?