Which type of algorithm provides the highest level of protection against brute-force attacks?
Which two actions does the Cisco identity Services Engine posture module provide that ensures endpoint security?(Choose two.)
A Cisco AMP for Endpoints administrator configures a custom detection policy to add specific MD5 signatures The configuration is created in the simple detection policy section, but it does not work What is the reason for this failure?
Which two actions does the Cisco ISE posture module provide that ensures endpoint security? (Choose two.)
Which attack is commonly associated with C and C++ programming languages?
What is the benefit of installing Cisco AMP for Endpoints on a network?
Which feature requires that network telemetry be enabled?
A network engineer is configuring a Cisco Catalyst switch. The network engineer must prevent traffic on the network from being interrupted by broadcast packets flooding the network using a predefined threshold. What must be configured on the switch?
Which RADIUS attribute can you use to filter MAB requests in an 802.1 x deployment?
An organization wants to reduce their attach surface for cloud applications. They want to understand application communications, detect abnormal application Behavior, and detect vulnerabilities within the applications. Which action accomplishes this task?
A company identified a phishing vulnerability during a pentest What are two ways the company can protect employees from the attack? (Choose two.)
On Cisco Firepower Management Center, which policy is used to collect health modules alerts from managed
devices?
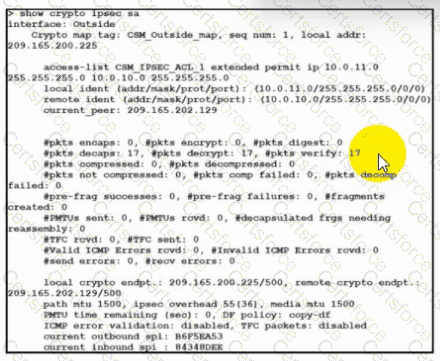
Refer to the exhibit. Traffic is not passing through IPsec site-to-site VPN on the Secure Firewall Threat Defense appliance. What is causing this issue?
An organization has noticed an increase in malicious content downloads and wants to use Cisco Umbrella to prevent this activity for suspicious domains while allowing normal web traffic. Which action will accomplish this task?
An organization plans to upgrade its current email security solutions, and an engineer must deploy Cisco Secure Email. The requirements for the upgrade are:
Implement Data Loss Prevention
Implement mail encryption
Integrate with an existing Cisco IronPort Secure Email Gateway solution
Which Cisco Secure Email license is needed to accomplish this task?