What is an advantage of the Cisco Umbrella roaming client?
An engineer must force an endpoint to re-authenticate an already authenticated session without disrupting the
endpoint to apply a new or updated policy from ISE. Which CoA type achieves this goal?
An engineer has been tasked with configuring a Cisco FTD to analyze protocol fields and detect anomalies in the traffic from industrial systems. What must be done to meet these requirements?
Which proxy mode must be used on Cisco WSA to redirect TCP traffic with WCCP?
Which Cisco DNA Center Intent API action is used to retrieve the number of devices known to a DNA Center?
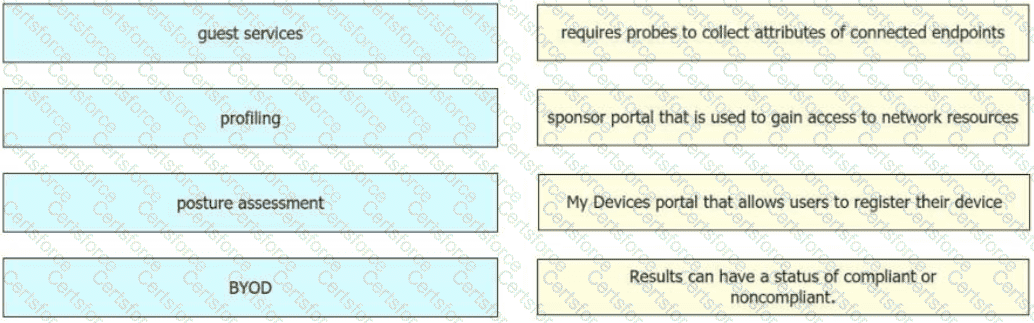
Drag and drop the concepts from the left onto the correct descriptions on the right
What are two differences between a Cisco Secure Web Appliance that is running in transparent mode and one running in explicit mode? (Choose two.)
In which form of attack is alternate encoding, such as hexadecimal representation, most often observed?
Which two services must remain as on-premises equipment when a hybrid email solution is deployed? (Choose two)
An MDM provides which two advantages to an organization with regards to device management? (Choose two)
Which two risks is a company vulnerable to if it does not have a well-established patching solution for
endpoints? (Choose two)
What is the process of performing automated static and dynamic analysis of files against preloaded
behavioral indicators for threat analysis?
What is the purpose of the Decrypt for Application Detection feature within the WSA Decryption options?
A network administrator needs a solution to match traffic and allow or deny the traffic based on the type of application, not just the source or destination address and port used. Which kind of security product must the network administrator implement to meet this requirement?
A network engineer must configure a Cisco Secure Email Gateway to prompt users to enter two forms of information before gaining access. The Secure Email Gateway must also join a cluster machine using preshared keys. What must be configured to meet these requirements?