What is the function of Cisco Cloudlock for data security?
Refer to the exhibit.
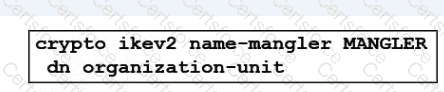
An engineer is implementing a certificate based VPN. What is the result of the existing configuration?
What does Cisco AMP for Endpoints use to help an organization detect different families of malware?
Which term describes when the Cisco Secure Firewall downloads threat intelligence updates from Cisco Tables?
Which two global commands must the network administrator implement to limit the attack surface of an internet-facing Cisco router? (Choose two.)
A Cisco Firepower administrator needs to configure a rule to allow a new application that has never been seen
on the network. Which two actions should be selected to allow the traffic to pass without inspection? (Choose
two)
How does Cisco Advanced Phishing Protection protect users?
An engineer is trying to securely connect to a router and wants to prevent insecure algorithms from being used.
However, the connection is failing. Which action should be taken to accomplish this goal?
Which Cisco solution extends network visibility, threat detection, and analytics to public cloud environments?
Why should organizations migrate to an MFA strategy for authentication?
A network administrator is modifying a remote access VPN on an FTD managed by an FMC. The administrator wants to offload traffic to certain trusted domains. The administrator wants this traffic to go out of the client's local internet and send other internet-bound traffic over the VPN Which feature must the administrator configure?
How many interfaces per bridge group does an ASA bridge group deployment support?
What is a difference between FlexVPN and DMVPN?
An organization is selecting a cloud architecture and does not want to be responsible for patch management of the operating systems. Why should the organization select either Platform as a Service or Infrastructure as a Service for this environment?
An organization has noticed an increase in malicious content downloads and wants to use Cisco Umbrella to prevent this activity for suspicious domains while allowing normal web traffic. Which action will accomplish this task?