Which two Cisco Umbrella security categories are used to prevent command-and-control callbacks on port 53 and protect users from being tricked into providing confidential information? (Choose two.)
An organization is trying to implement micro-segmentation on the network and wants to be able to gain visibility on the applications within the network. The solution must be able to maintain and force compliance. Which product should be used to meet these requirements?
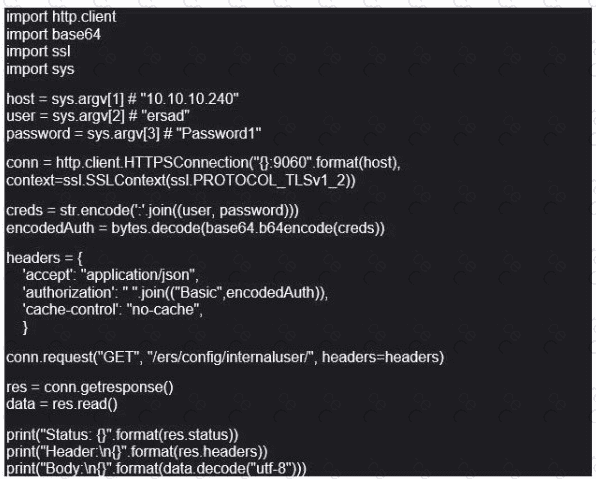
Refer to the exhibit. What does this Python script accomplish?
Which two devices support WCCP for traffic redirection? (Choose two.)
What is a benefit of performing device compliance?
An organization is using DNS services for their network and want to help improve the security of the DNS infrastructure. Which action accomplishes this task?
What is the purpose of the Trusted Automated exchange cyber threat intelligence industry standard?
A network administrator is setting up Cisco FMC to send logs to Cisco Security Analytics and Logging (SaaS). The network administrator is anticipating a high volume of logging events from the firewalls and wants lo limit the strain on firewall resources. Which method must the administrator use to send these logs to Cisco Security Analytics and Logging?
Which feature enables a Cisco ISR to use the default bypass list automatically for web filtering?
What are two functions of secret key cryptography? (Choose two)
What is the role of an endpoint in protecting a user from a phishing attack?
A network administrator is configuring a rule in an access control policy to block certain URLs and selects the “Chat and Instant Messaging” category. Which reputation score should be selected to accomplish this goal?
What are two functionalities of SDN Northbound APIs? (Choose two.)
Which action configures the IEEE 802.1X Flexible Authentication feature to support Layer 3 authentication mechanisms?
Which Cisco Advanced Malware protection for Endpoints deployment architecture is designed to keep data
within a network perimeter?