Which Cisco security solution stops exfiltration using HTTPS?
How is DNS tunneling used to exfiltrate data out of a corporate network?
An administrator needs to configure the Cisco ASA via ASDM such that the network management system
can actively monitor the host using SNMPv3. Which two tasks must be performed for this configuration?
(Choose two.)
Which security solution uses NetFlow to provide visibility across the network, data center, branch offices, and cloud?
Which method is used to deploy certificates and configure the supplicant on mobile devices to gain access to
network resources?
While using Cisco Secure Firewall's Security Intelligence policies, which two criteria is blocking based upon? (Choose two.)
Which type of protection encrypts RSA keys when they are exported and imported?
Which type of API is being used when a controller within a software-defined network architecture dynamically
makes configuration changes on switches within the network?
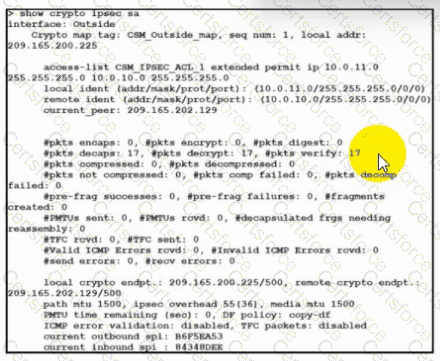
Refer to the exhibit. Traffic is not passing through IPsec site-to-site VPN on the Secure Firewall Threat Defense appliance. What is causing this issue?
An engineer integrates Cisco FMC and Cisco ISE using pxGrid Which role is assigned for Cisco FMC?
In which situation should an Endpoint Detection and Response solution be chosen versus an Endpoint Protection Platform?
What is the difference between deceptive phishing and spear phishing?
Which two features of Cisco Email Security can protect your organization against email threats? (Choose two)
Which category includes DoS Attacks?
What is a feature of Cisco NetFlow Secure Event Logging for Cisco ASAs?