An administrator is establishing a new site-to-site VPN connection on a Cisco IOS router. The organization
needs to ensure that the ISAKMP key on the hub is used only for terminating traffic from the IP address of
172.19.20.24. Which command on the hub will allow the administrator to accomplish this?
Where are individual sites specified to be block listed in Cisco Umbrella?
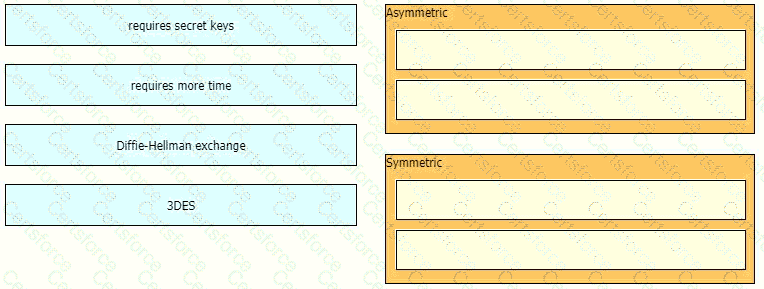
Drag and drop the descriptions from the left onto the encryption algorithms on the right.
What is the intent of a basic SYN flood attack?
A network engineer has been tasked with adding a new medical device to the network. Cisco ISE is being used as the NAC server, and the new device does not have a supplicant available. What must be done in order to securely connect this device to the network?
What is a function of the Layer 4 Traffic Monitor on a Cisco WSA?
What are two benefits of Flexible NetFlow records? (Choose two)
What is the primary role of the Cisco Email Security Appliance?
Which technology reduces data loss by identifying sensitive information stored in public computing
environments?
What is the most common type of data exfiltration that organizations currently experience?
Which compliance status is shown when a configured posture policy requirement is not met?
Drag and drop the VPN functions from the left onto the description on the right.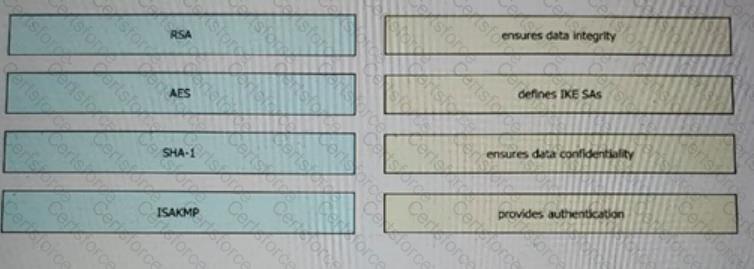
Which IETF attribute is supported for the RADIUS CoA feature?
Why should organizations migrate to a multifactor authentication strategy?
An email administrator is setting up a new Cisco ESA. The administrator wants to enable the blocking of greymail for the end user. Which feature must the administrator enable first?