Which two cryptographic algorithms are used with IPsec? (Choose two)
An organization wants to provide visibility and to identify active threats in its network using a VM. The
organization wants to extract metadata from network packet flow while ensuring that payloads are not retained
or transferred outside the network. Which solution meets these requirements?
Which method of attack is used by a hacker to send malicious code through a web application to an unsuspecting user to request that the victim's web browser executes the code?
Which two descriptions of AES encryption are true? (Choose two)
What is the function of the Context Directory Agent?
A network security engineer must export packet captures from the Cisco FMC web browser while troubleshooting an issue. When navigating to the address https://
Which Cisco security solution secures public, private, hybrid, and community clouds?
An engineer implements Cisco CloudLock to secure a Microsoft Office 365 application in the cloud. The engineer must configure protection for corporate files in case of any incidents. Which two actions must be taken to complete the implementation? (Choose two.)
An MDM provides which two advantages to an organization with regards to device management? (Choose two)
Which encryption algorithm provides highly secure VPN communications?
How does a WCCP-configured router identify if the Cisco WSA is functional?
An administrator is configuring a DHCP server to better secure their environment. They need to be able to ratelimit the traffic and ensure that legitimate requests are not dropped. How would this be accomplished?
Which two fields are defined in the NetFlow flow? (Choose two)
Which two endpoint measures are used to minimize the chances of falling victim to phishing and social
engineering attacks? (Choose two)
Refer to the exhibit.
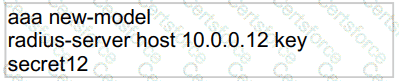
Which statement about the authentication protocol used in the configuration is true?