For Cisco IOS PKI, which two types of Servers are used as a distribution point for CRLs? (Choose two)
Which two solutions help combat social engineering and phishing at the endpoint level? (Choose two.)
What are two things to consider when using PAC files with the Cisco WSA? (Choose two.)
What are two benefits of using an MDM solution? (Choose two.)
What is a characteristic of a bridge group in ASA Firewall transparent mode?
An engineer is configuring Cisco Secure Endpoint to enhance security by preventing the execution of certain files by users. The engineer needs to ensure that the specific executable file name Cisco_Software_0505446151.exe is blocked from running while never being quarantined. What must the engineer configure to meet the requirement?
Which Cisco security solution protects remote users against phishing attacks when they are not connected to
the VPN?
Which system performs compliance checks and remote wiping?
An engineer is trying to decide whether to use Cisco Umbrella, Cisco CloudLock, Cisco Stealthwatch, or Cisco AppDynamics Cloud Monitoring for visibility into data transfers as well as protection against data exfiltration Which solution best meets these requirements?
What are two characteristics of the RESTful architecture used within Cisco DNA Center? (Choose two.)
Which two probes are configured to gather attributes of connected endpoints using Cisco Identity Services
Engine? (Choose two)
What features does Cisco FTDv provide over ASAv?
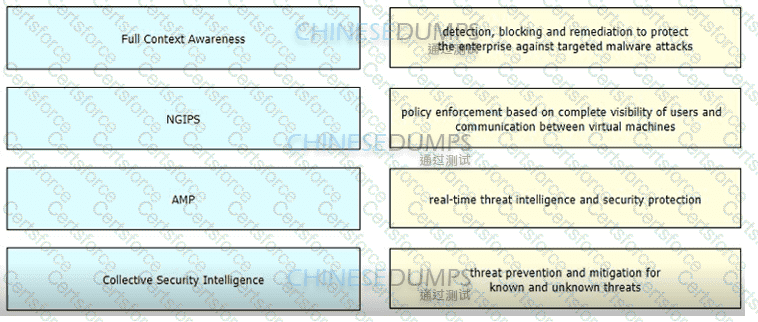
Drag and drop the features of Cisco ASA with Firepower from the left onto the benefits on the right.
Which two behavioral patterns characterize a ping of death attack? (Choose two)
Which Cisco network security device supports contextual awareness?