Which of the following BEST characterizes the operational benefit of using immutable workloads when working on a cloud-based project?
The primary consideration In maintenance, repair, and operating (MRO) supply systems typically is:
Exhibit:
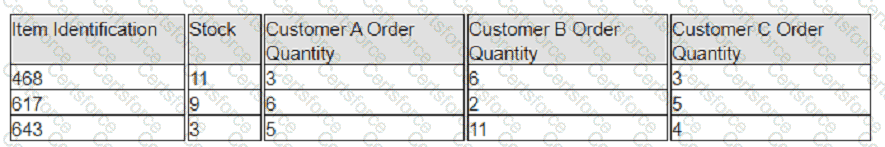
A company has prioritized customers A, B, and C, filling orders in that sequence. What are the impacts to customer service levels for customers B and C?
An organization is attempting to address the security risk introduced by employees writing down door entry passcodes. Which of the following security measures BEST mitigates this risk?
Which of the following circumstances would cause a move from acceptance sampling to 100% inspection?
A security analyst has been asked to build a data retention policy for a hospital. What is the FIRST action that needs to be performed in building this policy?
Components of an organization's Immediate industry and competitive environment Include:
In the Session layer of the Open Systems Interconnection (OSI) model, which of the following modes allows only one host to send information to its peer?
One of the most useful tools for analyzing the sustainable footprint is:
Disaster Recovery (DR) training plan outcomes should have which KEY quality?
An organization has been the subject of increasingly sophisticated phishing campaigns in recent months and has detected unauthorized access attempts against its Virtual Private Network (VPN) concentrators. Which of the following implementations would have the GREATEST impact on reducing the risk of credential compromise?
A health care organization's new cloud-based customer-facing application is constantly receiving security events from dubious sources. What BEST describes a security event that compromises the confidentiality, integrity or availability of the application and data?
During an investigation, a forensic analyst executed a task to allow for the authentication of all documents, data, and objects collected, if required. Which of the options below BEST describes this task?
A company has a demand for 30 units of A, 40 units of B, and 50 units of C. These products are scheduled to run daily in batches of 10 as follows: ABC, ABC, ABC, CBC. What is this scheduling
technique called?
Which of the following are steps involved in the identity and access provisioning lifecycle?