Price negotiation is most appropriate when purchasing which of the following product categories?
A security engineer must address resource sharing between various applications without adding physical hardware to the environment. Which secure design principle is used to BEST segregate applications?
Exhibit:
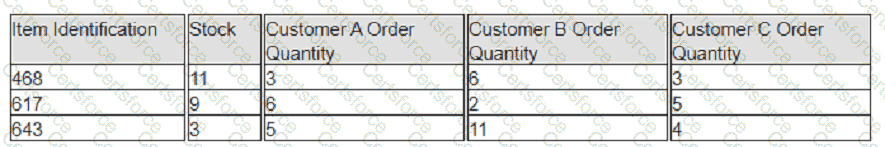
A company has prioritized customers A, B, and C, filling orders in that sequence. What are the impacts to customer service levels for customers B and C?
An organization has been struggling to improve their security posture after a recent breach. Where should the organization focus their efforts?
An Information Technology (IT) professional is seeking a control objective framework that is widely accepted around the world and focuses specifically on information security controls. Which of the following frameworks BEST meets this need?
During the sales and operations planning (S&OP) process, which of the following tasks is the primary responsibility of the functional representatives on the supply planning team?
An organization donates used computer equipment to a non-profit group. A system administrator used a degausser on both the magnetic and Solid State Drives (SSD) before delivery. A volunteer at the non-profit group discovered some of the drives still contained readable data and alerted the system administrator. What is the BEST solution to ensure that computer equipment does not contain data before release?
Why would a network administrator monitor Internet of Things (IoT) security differently than the security of standards network devices?
A new organization building is being designed and the security manager has been asked for input on needed security requirements. Which of the following controls are MOST applicable to this scenario?
Which of the following production activity control (PAC) techniques focuses on optimizing output?
An organization is running a cloud-based application to process the information obtained at point-of-sale devices. Which guideline should be applied to the application?
A company is having trouble with raw material deliveries and has decided to develop a supplier certification program. The certification process most appropriately would start with which of the following suppliers?
Which of the following actions hinders the transition from a push system to a pull system?
Which of the following is the workflow of the identity and access provisioning lifecycle?
A firm that currently produces all items to stock is implementing the concept of postponement in all new product designs. Which of the following outcomes is most likely to result?