Which of the following methods most likely Introduces a temporary variance between the inventory balance and the inventory record?
If all other factors remain the same, when finished goods inventory investment is increased, service levels typically will:
An organization’s external auditors have issued a management letter identifying significant deficiencies related to the effectiveness of the previous year’s global access certification. The organization wants to move from a department-based access control system to a Role-Based Access Control (RBAC) system. In addition to quickly and securely provisioning users by granting membership into predefined and approved roles, which of these presents the BEST reason to do so?
A large volume of outbound Transmission Control Protocol (TCP) connections from the same source Internet Protocol (IP) address was observed at a satellite office firewall. Which of the following is the MOST likely explanation?
Which security concept states that a subject (user, application, or asset) be given only the access needed to complete a task?
In a large organization, the average time for a new user to receive access is seven days. Which of the following is the BEST enabler to shorten this time?
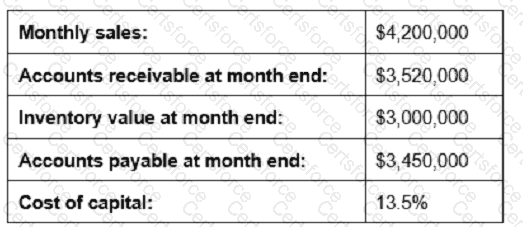
Given the information below, reducing which measure by 10% would contribute most to shortening the cash-to-cash cycle time?
An organization is attempting to address the security risk introduced by employees writing down door entry passcodes. Which of the following security measures BEST mitigates this risk?
Which of the following BEST describes the responsibility of an information System Security Officer?
What General Data Protection Regulation (GDPR) principle says that data should be collected lawfully and with the person’s consent?
An support technician is contacted by an imposter claiming to be a supervisor and is asked specifically to perform a task that violates the organization’s security policies. What type of attack is this?
The time spent In queue by a specific manufacturing job is determined by which of the following factors related to the order?
One of the most useful tools for analyzing the sustainable footprint is:
Before securing a email system using OpenPGP in an organization, Which of the following actions MUST be performed?
A manufacturing facility uses common wireless technologies to communicate. The head of security is concerned about eavesdropping by attackers outside the perimeter fence. The distance between the facility and fence is at least 300 feet (100 m). Which of the following wireless technologies is MOST likely to be available to an attacker outside the fence?