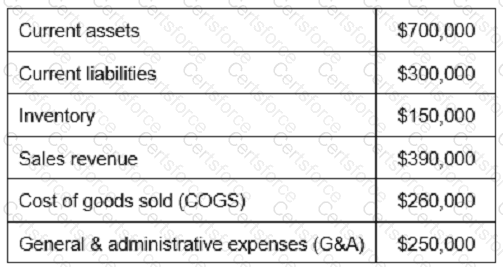
Based on the values reported in the table below, what is the inventory turnover?
Which of the following measurements indicates there may be bias In the forecast model?
Which of the following BEST describes the purpose of black hat testing during an assessment?
An organization has a call center that uses a Voice Over Internet Protocol (VoIP) system. The conversations are sensitive, and the organization is concerned about employees other than the call agents accessing these conversations. What is the MOST effective additional security measure to make?
A company decided not to pursue a business opportunity In a foreign market due to political Instability and currency fluctuations. Which risk control strategy did this business utilize?
Health information stored in paper form may be destroyed using which of the following methods?
Disaster Recovery (DR) training plan outcomes should have which KEY quality?
What is the HIGHEST security concern on trans-border data?
A cybersecurity analyst has recently been assigned to work with a product development team. The team has usually needed to perform a lot of rework late in the development cycle on past projects due to application security concerns. They would like to minimize the amount of rework necessary. Which would be the BEST option to enable secure code review early in the product development?
In restoring the entire corporate email system after a major outage and data loss, an email administrator reads a few email message exchanges between the human resources manager and a candidate for an open position. Which of the following BEST describes the behavior of the email administrator, and why?
When resolving conflicts, which canon within the ISC2 Code of Ethics requires members to consider duties to principals and Individuals?
Which of the following is typically used to control physical access to highly secure facilities?
Which of the following actions best supports a company's strategic focus on delivery speed to improve competitive advantage?
While doing a penetration test, auditors found an old credential hash for a privileged user. To prevent a privileged user's hash from being cached, what is the MOST appropriate policy to mandate?
Which of the following circumstances would cause a move from acceptance sampling to 100% inspection?