Refer to the exhibit.
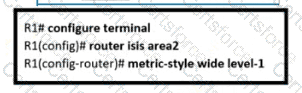
An engineer is configuring multitopology IS-IS for IPv6 on router R1. Which additional configuration must be applied to the router to complete the task?

Refer to the exhibit.

A network engineer must implement SNMPv3 on a Cisco IOS XR router running BGP. The engineer configures SNMPv3 to use SHA for authentication and AES for privacy on the routers, which are in a different data center in the same exchange as other routers. The engineer must also verify the associated MIB view family name, storage type, and status. Which set of actions meets these requirements?
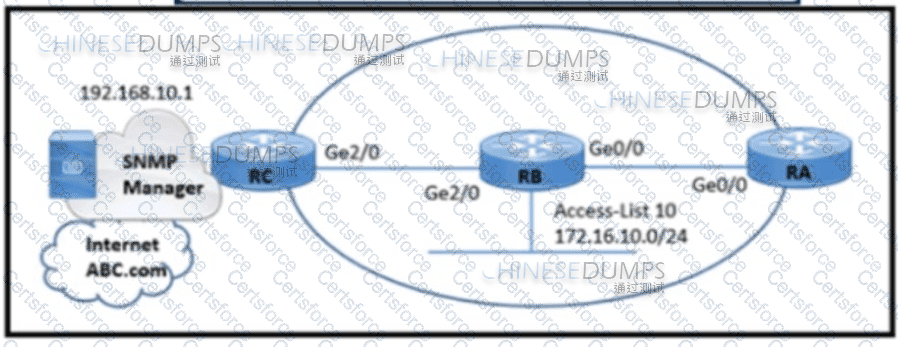
Refer to the exhibit. A network engineer is configuring an SNMP community on router RB with these requirements:
Allow read-only access for all objects to members of Access-List 10 that use the comaccess community string.
Other SNMP managers must not have access to objects.
SNMP authentication failure traps must be sent to SNMPv2c and then to the host using SNMPv2c with the public community string.
Which configuration meets these requirements?
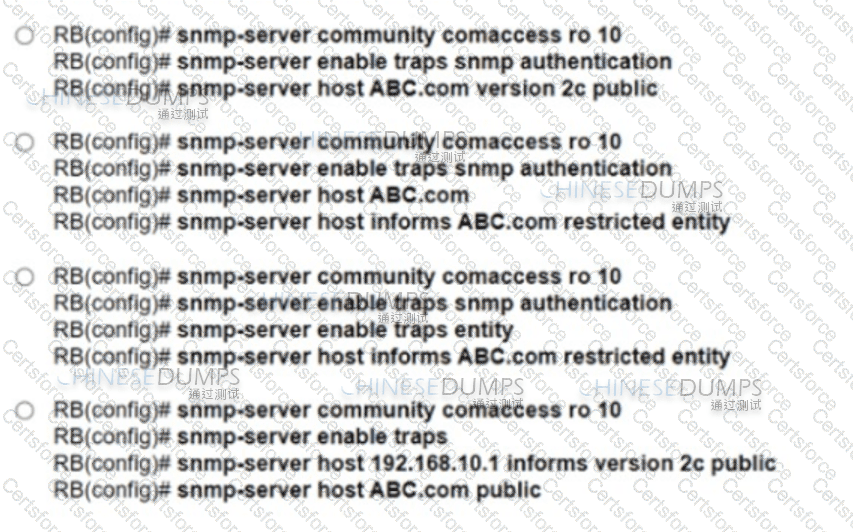
A mod-size service provider uses L2VPN as its standard for connectivity between offices. A small company wants the service provider to connect the company’s two sites across the service provider core. To meet service requirements, the service provider must extend the layer 2 domain between the company’s two locations. Which configuration must the engineer apply to implement an attachment circuit between the two sites using a VLAN tag of 12?
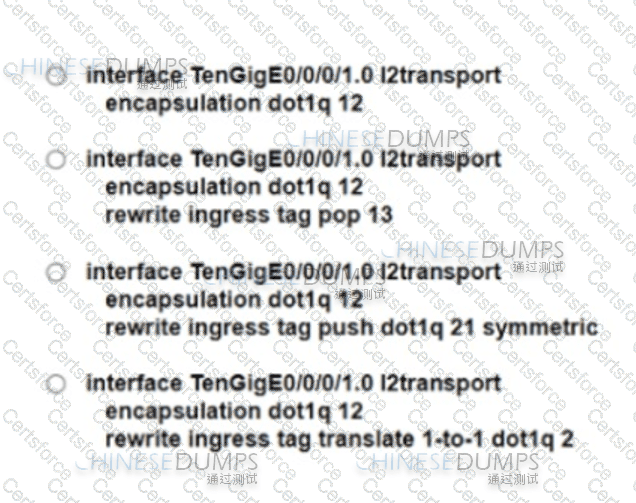
Refer to the exhibit.
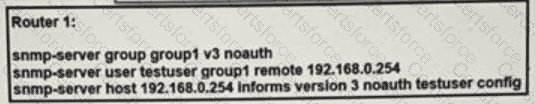
A network engineer is deploying SNMP configuration on client's routers. Encrypted authentication must be included on router 1 to provide security and protect message confidentially. Which action should the engineer perform on the routers to accomplish this task?
An ISP Is Implementing end-to-end fault monitoring for a customer based on the IEEE 802.3ah standard. The solution must detect when 15 or more corrupted Ethernet packets arrive within 10 ms and stop propagating traffic through the ISP backbone network or to the customer side. Which configuration must the ISP engineer apply?
Which two tasks must an engineer perform when implementing LDP NSF on the network? (Choose two.)
What is the primary purpose of containers in a service-provider virtualization environment?
Refer to the exhibit. After a networking team configured this MPLS topology, the supervisor wants to view MPLS labels to verify the path that packets take from router R1 to router R7 The team already Issued an ICMP ping to verify connectivity between the devices. Which task must the team perform to allow the supervisor to view the label switch path?
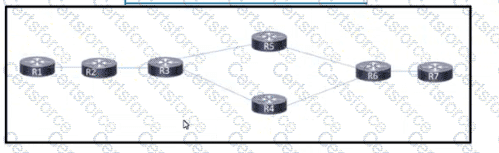
Refer to the exhibit:

R1 and R2 are directly connected with Fast Ethernet interfaces and have the above configuration applied OSPF adjacency is not formed. When the debug ip ospf hello command is issued on R1. these log messages are seen.

Which command can be configured on routers R1 and R2 on fO/O interfaces to form OSPF adjacency?
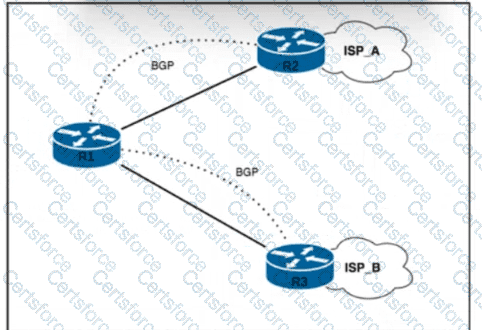
Refer to the exhibit. R1 has two upstream Tier 1 service providers. BGP is in use as the exterior routing protocol, and ISP_A and ISP_B are sending the full BGP table. A network engineer must assign local-preference 70 to all routes with multiple exit discriminator 30. Which configuration must the network engineer apply?

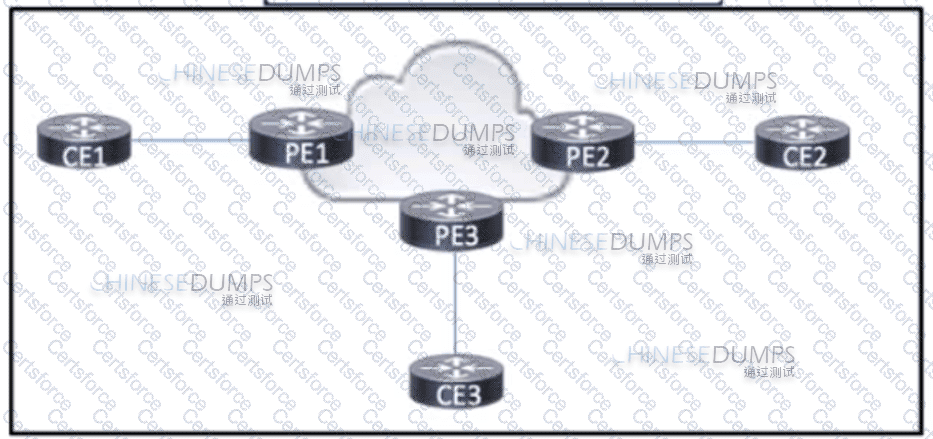
Refer to the exhibit. A large enterprise has multiple branch offices that span several geographic regions. The enterprise runs MPLS within the core to propagate VPNv4 routes using BGP. After a recent series of DDoS attacks disrupted the network, a network engineer has been asked to reconfigure BGP to help mitigate future attacks. Which configuration must the engineer apply?
A)

B)

C)
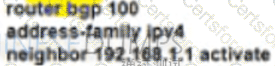
D)

Refer to the exhibit.

Which show command shows statistics for the control plane policy and is used to troubleshoot?
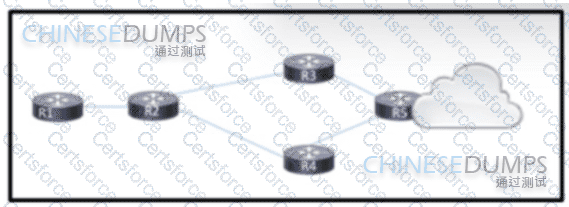
Refer to the exhibit. An engineer is scripting ACLs to handle traffic on the given network. The engineer must block users on the network between R1 and R2 from leaving the network through R5. but these users must still be able to access all resources within the administrative domain. How must the engineer implement the ACL configuration?
Refer to the exhibit.
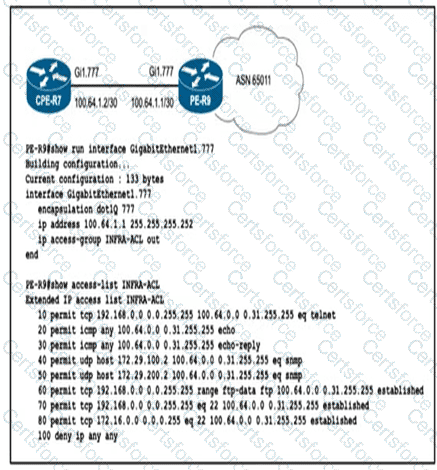
To protect in-band management access to CPE-R7, an engineer wants to allow only SSH management and provisioning traffic from management network 192.168.0.0/16. Which infrastructure ACL change must be applied to router PE-R9 to complete this task?
A)

B)

C)
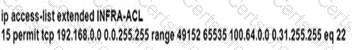
D)
