Which utility must be used to locate MPLS faults?
Refer to the exhibit.

What does the script configure?
A network engineer must implement an ACL-based solution to mitigate availability issues on a web service that is hosted on a server at IP address 172.16.15.18/23. Access to the web server should be allowed over HTTP from RFC 1918 addresses only. The network architect has already enabled PMTUD in the network. Which ACL configuration must the engineer implement to complete the task?
Refer to the exhibit:
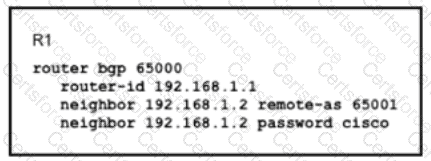
Router R1 and its peer R2 reside on the same subnet in the network, If does it make connections to R27
A regional company is planning to bolster the security of their LAN infrastructure by implementing advanced encryption techniques between their core switch and their distribution switch. The solution must leverage hardware-accelerated encryption capabilities to transparently encrypt all traffic between the two switches at the data-link layer to safeguard against unauthorized access. However, it is important for the solution to have minimal impact on network performance and latency.
Which action must the engineer take to meet the requirements?
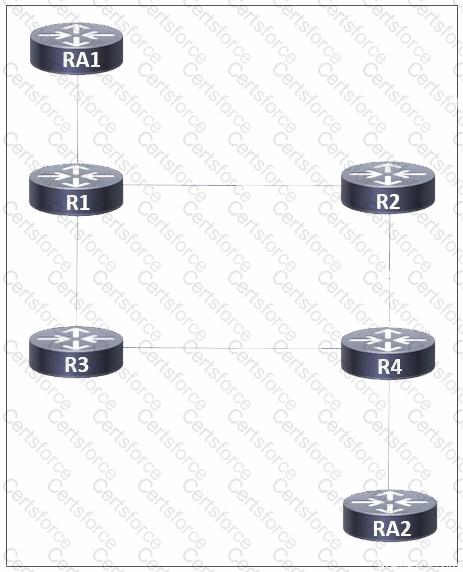
Refer to the exhibit. A network administrator implemented MPLS routing between routers R1, R2, R3, and R4. AToM is configured between R1 and R4 to allow Layer 2 traffic from hosts on RA1 and RA2. A targeted MPLS session is established between R1 and R4. Which additional action must the administrator take on all routers so that LDP synchronization occurs between connected LDP sessions?
Under which circumstance does BGP ignore the best-path algorithm after receiving multiple routes to a destination?
Refer to the exhibit:
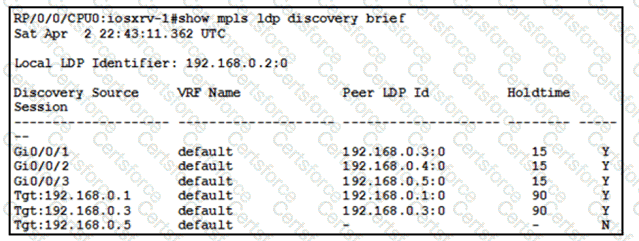
With which router does IOSXRV-1 have LDP session protection capability enabled but session hold up is not active?

Guidelines
-
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
Topology
Tasks
-
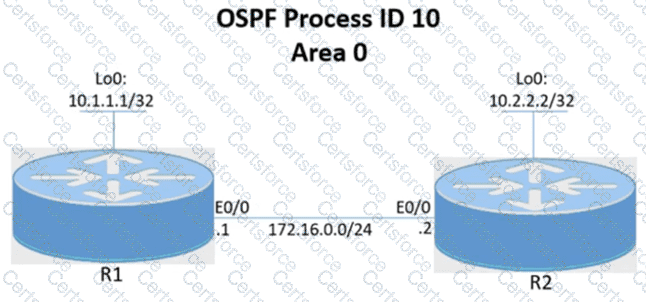
Configure and verify the OSPF neighbor adjacency between R1 and R2 in OSPF area 0 according to the topology to achieve these goals:
1. Establish R1 and R2 OSPF adjacency. All interfaces must be advertised in OSPF by using the OSPF interface command method. Use Loopback0 as the OSPF ID.
2. There must be no DR/BDR elections in OSPF Area 0 when establishing the neighbor relationship between R1 and R2. OSPF must not generate the host entries /32 for the adjacent interfaces.
3. Enable OSPF MD5 Authentication between both routers at the interface level with password C1sc0!.
Which type of attack is an application attack?
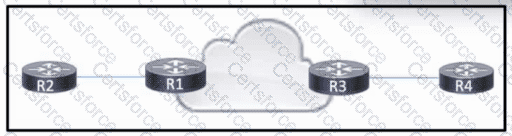
Refer to the exhibit. R1 and R3 have a pseudowire connection between them, which allows R2 and R4 to communicate via Layer 2. R2 uses VLAN 10. R4 also uses VLAN 10, but with a different subnet associated.
Which configuration should the engineer apply to R3 to rewrite the VLAN on traffic from R2 to VLAN 15?
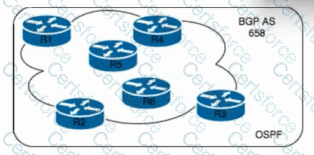
Refer to the exhibit. An ISP is providing online registration services for a new social program. OSPF is being used as an interior routing protocol with TE capabilities. A network engineer with an employee ID: 5209:82:636 must provide faster MPLS-enabled convergence in case of failure. The ip cef distributed command has already been configured on all MPLS-enabled routers, and connectivity between the core routers has been verified following IETF RFC 4379. Which additional task must the engineer perform to complete the implementation?
What is the main purpose of EVPN?
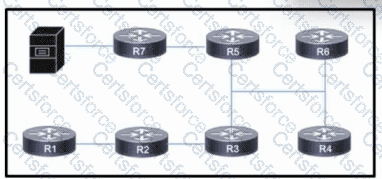
Refer to the exhibit. The network is configured with OSPF. A networking team just connected a streaming multicast server to router R7, and they now must enable access for users throughout the network to stream video from the server.
Which action must the team take so that users can stream video without overloading the network?
How is a telemetry session established for data analytics?