You need to configure the compliance settings to meet the technical requirements.
What should you do in the Microsoft Endpoint Manager admin center?
You create the planned DLP policies.
You need to configure notifications to meet the technical requirements.
What should you do?
You need to create the DLP policy to meet the technical requirements.
What should you configure first?
You need to create the Safe Attachments policy to meet the technical requirements.
Which option should you select?
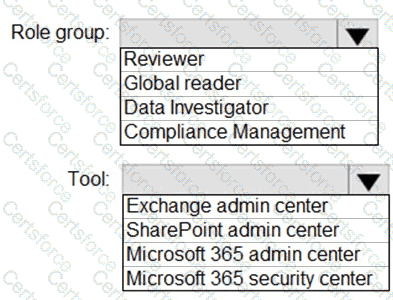
You need to ensure that User2 can review the audit logs. The solutions must meet the technical requirements.
To which role group should you add User2, and what should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to configure Office on the web to meet the technical requirements.
What should you do?
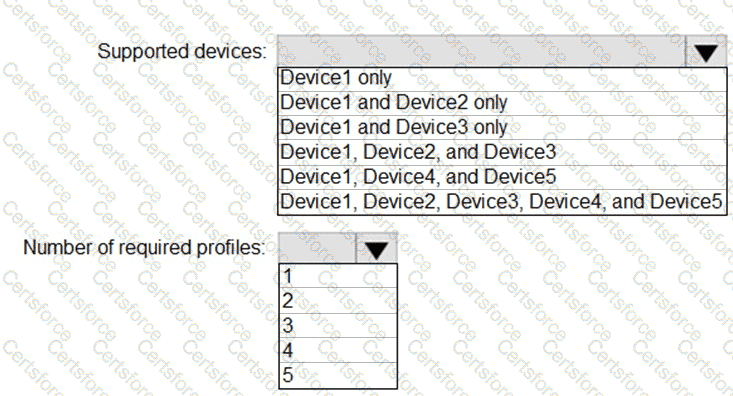
You plan to implement the endpoint protection device configuration profiles to support the planned changes.
You need to identify which devices will be supported, and how many profiles you should implement.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
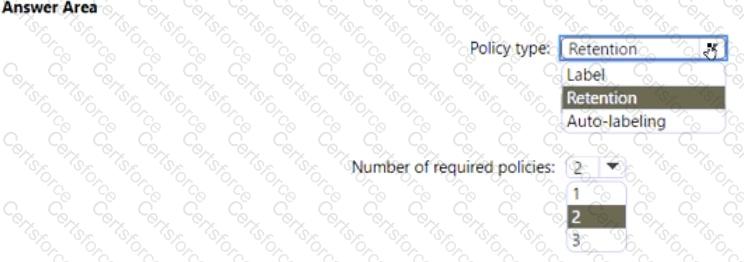
You need to configure the information governance settings to meet the technical requirements.
Which type of policy should you configure, and how many policies should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 tenant that contains a user named User1.
You plan to implement insider risk management.
You need to ensure that User1 can perform the following tasks:
Review alerts.
Manage cases.
Create notice templates.
Review user emails by using Content explorer.
The solution must use the principle of least privilege.
To which role group should you add User1?
You have a Microsoft 365 E5 subscription. You are implementing Microsoft Defender for Cloud Apps. You need to ensure that you can create OAuth app policies.
Solution: You add an API token to Defender for Cloud Apps.
Does this meet the goal?