An administrator is configuring RADIUS on a Cisco switch with a key set to Cisc403012128 but is receiving the error “Authentication failed: 22040 Wrong password or invalid shared secret. “what must be done to address this issue?
A laptop was stolen and a network engineer added it to the block list endpoint identity group What must be done on a new Cisco ISE deployment to redirect the laptop and restrict access?
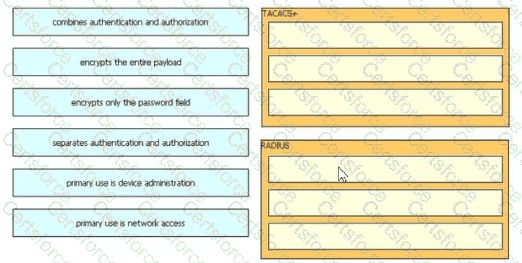
Drag and drop the description from the left onto the protocol on the right that is used to carry out system authentication, authentication, and accounting.
Which protocol must be allowed for a BYOD device to access the BYOD portal?
An employee must access the internet through the corporate network from a new mobile device that does not support native supplicant provisioning provided by Cisco ISE. Which portal must the employee use to provision to the device?
An administrator enables the profiling service for Cisco ISE to use for authorization policies while in closed mode. When the endpoints connect, they receive limited access so that the profiling probes can gather information and Cisco ISE can assign the correct profiles. They are using the default values within Cisco ISE. but the devices do not change their access due to the new profile. What is the problem'?
An engineer is configuring Central Web Authentication in Cisco ISE to provide guest access. When an authentication rule is configured in the Default Policy Set for the Wired_MAB or Wireless_MAB conditions, what must be selected for the "if user not found" setting?
Which action must be taken before configuring the Secure Client Agent profile when creating the Secure Client configuration for ISE posture services?
NO: 184
An engineer builds a five-node distributed Cisco ISE deployment The first two deployed nodes are responsible for the primary and secondary administration and monitoring personas Which persona configuration is necessary to have the remaining three Cisco ISE nodes serve as dedicated nodes in the Cisco ISE cube that is responsible only for handling the RADIUS and TACACS+ authentication requests, identity lookups, and policy evaluation?
A)
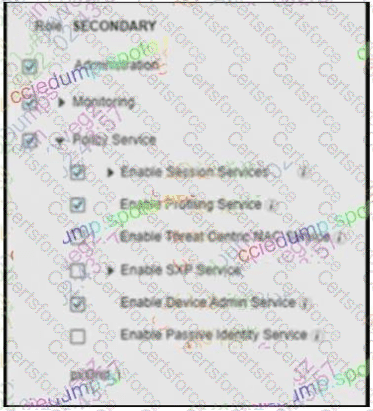
B)
C)
D)