When planning for the deployment of Cisco ISE, an organization's security policy dictates that they must use network access authentication via RADIUS. It also states that the deployment provide an adequate amount of security and visibility for the hosts on the network. Why should the engineer configure MAB in this situation?
What are two components of the posture requirement when configuring Cisco ISE posture? (Choose two)
An engineer is working with a distributed deployment of Cisco ISE and needs to configure various network probes to collect a set of attributes from the endpoints on the network. Which node should be used to accomplish this task?
Which advanced option within a WLAN must be enabled to trigger Central Web Authentication for Wireless users on AireOS controller?
An administrator is configuring posture with Cisco ISE and wants to check that specific services are present on the workstations that are attempting to access the network. What must be configured to accomplish this goal?
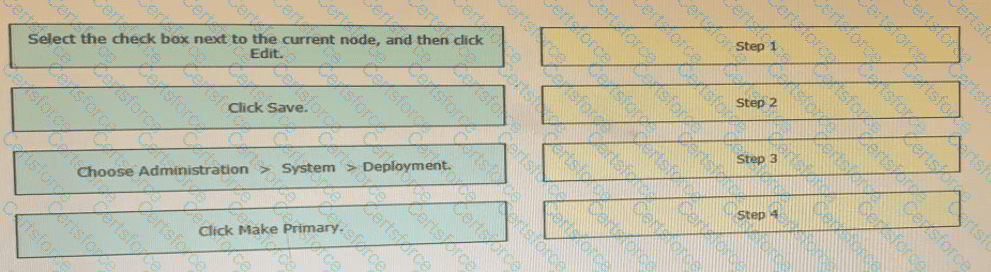
Drag the steps to configure a Cisco ISE node as a primary administration node from the left into the correct order on the night.
What is a requirement for Feed Service to work?
A Cisco ISE server sends a CoA to a NAD after a user logs in successfully using CWA Which action does the CoA perform?
Which two actions must be verified to confirm that the internet is accessible via guest access when configuring a guest portal? (Choose two.)
A user changes the status of a device to stolen in the My Devices Portal of Cisco ISE. The device was originally onboarded in the BYOD wireless Portal without a certificate. The device is found later, but the user cannot re-onboard the device because Cisco ISE assigned the device to the Blocklist endpoint identity group. What must the user do in the My Devices Portal to resolve this issue?