Which Web Services Security (WS-Security) specification handles the management of security tokens and the underlying policies for granting access? Click on the correct specification in the image below.
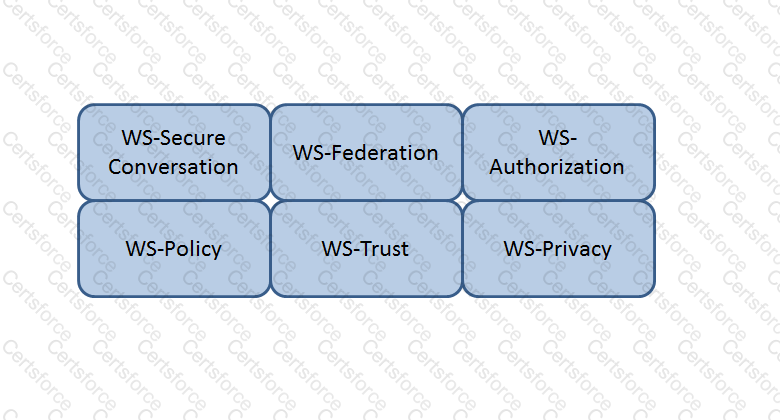
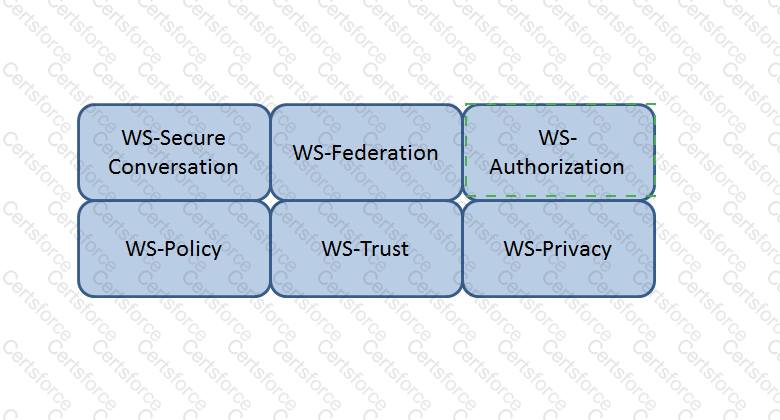
WS-Authorization
Which of the following BEST describes a Protection Profile (PP)?
A document that expresses an implementation independent set of security requirements for an IT product that meets specific consumer needs.
A document that is used to develop an IT security product from its security requirements definition.
A document that expresses an implementation dependent set of security requirements which contains only the security functional requirements.
A document that represents evaluated products where there is a one-to-one correspondence between a PP and a Security Target (ST).
A Protection Profile (PP) is a document that expresses an implementation independent set of security requirements for an IT product that meets specific consumer needs. A PP is based on the Common Criteria (CC) framework, which is an international standard for evaluating the security of IT products and systems. A PP defines the security objectives, threats, assumptions, and functional and assurance requirements for a product or a category of products. The other options are not correct descriptions of a PP. Option B is a description of a Security Target (ST), which is a document that is used to develop an IT security product from its security requirements definition. Option C is a description of an implementation dependent set of security requirements, which is not a PP, but rather a part of an ST. Option D is a description of a certified product, which is a product that has been evaluated against a PP or an ST and has met the security requirements. References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 8, p. 414; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 3, p. 147.
A global organization wants to implement hardware tokens as part of a multifactor authentication solution for remote access. The PRIMARY advantage of this implementation is
the scalability of token enrollment.
increased accountability of end users.
it protects against unauthorized access.
it simplifies user access administration.
The primary advantage of implementing hardware tokens as part of a multifactor authentication solution for remote access is that it protects against unauthorized access by requiring the user to possess something (the token) and to know something (the PIN or password) to authenticate. Hardware tokens are physical devices that generate one-time passwords (OTP) or digital certificates that are used in conjunction with a personal identification number (PIN) or a password to verify the user’s identity.
A. the scalability of token enrollment is not the primary advantage of implementing hardware tokens, but rather a challenge that requires efficient and secure processes to distribute, activate, and revoke tokens.
B. increased accountability of end users is not the primary advantage of implementing hardware tokens, but rather a benefit that depends on the proper management and usage of the tokens by the end users and the administrators.
D. it simplifies user access administration is not the primary advantage of implementing hardware tokens, but rather a potential drawback that requires additional resources and tools to manage the tokens and their lifecycle.
References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 5, page 274; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 5, page 223
Which of the following is a weakness of Wired Equivalent Privacy (WEP)?
Length of Initialization Vector (IV)
Protection against message replay
Detection of message tampering
Built-in provision to rotate keys
According to the CISSP All-in-One Exam Guide2, a weakness of Wired Equivalent Privacy (WEP) is the length of the Initialization Vector (IV). WEP is a security protocol that was designed to provide confidentiality and integrity for wireless networks, by using the RC4 stream cipher to encrypt the data and the CRC-32 checksum to verify the data. However, WEP has several flaws that make it vulnerable to various attacks, such as the IV attack, the key recovery attack, the bit-flipping attack, and the replay attack. One of the flaws of WEP is the length of the IV, which is only 24 bits long. This means that the IV space is very small, and the IVs are likely to repeat after a short period of time, especially in a busy network. This allows an attacker to capture enough IVs and ciphertexts to perform a statistical analysis and recover the encryption key. WEP does not provide protection against message replay, detection of message tampering, or built-in provision to rotate keys, but these are not weaknesses of WEP, but rather limitations or features that WEP lacks. References: 2
During the Security Assessment and Authorization process, what is the PRIMARY purpose for conducting a hardware and software inventory?
Calculate the value of assets being accredited.
Create a list to include in the Security Assessment and Authorization package.
Identify obsolete hardware and software.
Define the boundaries of the information system.
The Security Assessment and Authorization (SA&A) process is a framework that ensures that information systems meet the security requirements and standards of the organization and the applicable laws and regulations. The SA&A process consists of four phases: initiation, assessment, authorization, and monitoring. During the initiation phase, one of the primary purposes for conducting a hardware and software inventory is to define the boundaries of the information system, i.e., the scope and extent of the system components, interfaces, and data flows. Defining the boundaries of the information system helps to identify the security risks, controls, and responsibilities associated with the system, as well as to determine the level of effort and resources required for the assessment and authorization phases12. References:
Security Assessment and Authorization - NIST, Section: 2.1 Initiation Phase
Security Assessment and Authorization - NIST, Section: 2.1.1 Identify Information System Boundaries
What is the PRIMARY difference between security policies and security procedures?
Policies are used to enforce violations, and procedures create penalties
Policies point to guidelines, and procedures are more contractual in nature
Policies are included in awareness training, and procedures give guidance
Policies are generic in nature, and procedures contain operational details
The primary difference between security policies and security procedures is that policies are generic in nature, and procedures contain operational details. Security policies are the high-level statements or rules that define the goals, objectives, and requirements of security for an organization. Security procedures are the low-level steps or actions that specify how to implement, enforce, and comply with the security policies.
A. Policies are used to enforce violations, and procedures create penalties is not a correct answer, as it confuses the roles and functions of policies and procedures. Policies are used to create penalties, and procedures are used to enforce violations. Penalties are the consequences or sanctions that are imposed for violating the security policies, and they are defined by the policies. Enforcement is the process or mechanism of ensuring compliance with the security policies, and it is carried out by the procedures.
B. Policies point to guidelines, and procedures are more contractual in nature is not a correct answer, as it misrepresents the nature and purpose of policies and procedures. Policies are not merely guidelines, but rather mandatory rules that bind the organization and its stakeholders to follow the security principles and standards. Procedures are not contractual in nature, but rather operational in nature, as they describe the specific tasks and activities that are necessary to achieve the security goals and objectives.
C. Policies are included in awareness training, and procedures give guidance is not a correct answer, as it implies that policies and procedures have different audiences and functions. Policies and procedures are both included in awareness training, and they both give guidance. Awareness training is the process of educating and informing the organization and its stakeholders about the security policies and procedures, and their roles and responsibilities in security. Guidance is the process of providing direction and advice on how to comply with the security policies and procedures, and how to handle security issues and incidents.
References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 1, page 17; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 1, page 13
Sensitive customer data is going to be added to a database. What is the MOST effective implementation for ensuring data privacy?
Discretionary Access Control (DAC) procedures
Mandatory Access Control (MAC) procedures
Data link encryption
Segregation of duties
The most effective implementation for ensuring data privacy when sensitive customer data is going to be added to a database is data link encryption. Data link encryption is a type of encryption or a protection technique or mechanism that encrypts or protects the data or the information that is transmitted or communicated over the data link layer or the second layer of the Open Systems Interconnection (OSI) model, which is the layer or the level that provides or offers the reliable or the error-free transmission or communication of the data or the information between the nodes or the devices that are connected or linked by the physical layer or the first layer of the OSI model, such as the switches, the bridges, or the wireless access points. Data link encryption can provide a high level of security or protection for the data or the information that is transmitted or communicated over the data link layer, as it can prevent or reduce the risk of unauthorized or inappropriate access, disclosure, modification, or interception of the data or the information by the third parties or the attackers who capture or monitor the data or the information over the data link layer, and as it can also provide the confidentiality, the integrity, or the authenticity of the data or the information that is transmitted or communicated over the data link layer. Data link encryption is the most effective implementation for ensuring data privacy when sensitive customer data is going to be added to a database, as it can ensure or maintain the security or the quality of the sensitive customer data or the information that is transmitted or communicated over the data link layer, by encrypting or protecting the sensitive customer data or the information that is going to be added to the database, and by preventing or reducing the risk of unauthorized or inappropriate access, disclosure, modification, or interception of the sensitive customer data or the information by the third parties or the attackers who capture or monitor the sensitive customer data or the information over the data link layer.
A. Discretionary Access Control (DAC) procedures are not the most effective implementation for ensuring data privacy when sensitive customer data is going to be added to a database, but rather a type of access control or a protection mechanism or process that grants or denies the access or the permission to the resources or the data within a system or a service, based on the discretion or the decision of the owner or the creator of the resources or the data within the system or the service, such as the user, the device, or the process. Discretionary Access Control (DAC) procedures can provide a low level of security or protection for the system or the service, as it can increase or enhance the risk of unauthorized or inappropriate access or permission to the resources or the data within the system or the service, by the user or the device that is not approved or authorized by the owner or the creator of the resources or the data within the system or the service, such as the user, the device, or the process, and as it can also depend or rely on the trust or the confidence of the owner or the creator of the resources or the data within the system or the service, such as the user, the device, or the process, for the access control or the protection mechanism or process. Discretionary Access Control (DAC) procedures are not the most effective implementation for ensuring data privacy when sensitive customer data is going to be added to a database, as they do not provide or offer the encryption or the protection for the sensitive customer data or the information that is transmitted or communicated over the data link layer, and as they do not prevent or reduce the risk of unauthorized or inappropriate access, disclosure, modification, or interception of the sensitive customer data or the information by the third parties or the attackers who capture or monitor the sensitive customer data or the information over the data link layer.
B. Mandatory Access Control (MAC) procedures are not the most effective implementation for ensuring data privacy when sensitive customer data is going to be added to a database, but rather a type of access control or a protection mechanism or process that grants or denies the access or the permission to the resources or the data within a system or a service, based on the sensitivity or the classification of the resources or the data within the system or the service, such as the public, the confidential, or the secret, and the clearance or the authorization of the user or the device that accesses or handles the resources or the data within the system or the service, such as the low, the medium, or the high. Mandatory Access Control (MAC) procedures can provide a high level of security or protection for the system or the service, as it can prevent or reduce the risk of unauthorized or inappropriate access or permission to the resources or the data within the system or the service, by the user or the device that does not have the appropriate or the necessary clearance or authorization to access or to handle the resources or the data within the system or the service, based on the sensitivity or the classification of the resources or the data within the system or the service, such as the public, the confidential, or the secret. However, Mandatory Access Control (MAC) procedures are not the most effective implementation for ensuring data privacy when sensitive customer data is going to be added to a database, as they do not provide or offer the encryption or the protection for the sensitive customer data or the information that is transmitted or communicated over the data link layer, and as they do not prevent or reduce the risk of unauthorized or inappropriate access, disclosure, modification, or interception of the sensitive customer data or the information by the third parties or the attackers who capture or monitor the sensitive customer data or the information over the data link layer.
D. Segregation of duties is not the most effective implementation for ensuring data privacy when sensitive customer data is going to be added to a database, but rather a type of control or a protection technique or mechanism that separates or divides the tasks or the functions that are related or relevant to the resources or the data within a system or a service, among the different or the various users or the devices within an organization, such as the bank teller, the supervisor, or the manager, to prevent or to reduce the risk of fraud, error, or abuse of the resources or the data within the system or the service, by the user or the device that has the complete or the full control or authority over the resources or the data within the system or the service, such as the bank teller, the supervisor, or the manager. Segregation of duties can provide a moderate level of security or protection for the system or the service, as it can prevent or reduce the risk of fraud, error, or abuse of the resources or the data within the system or the service, by the user or the device that has the complete or the full control or authority over the resources or the data within the system or the service, such as the bank teller, the supervisor, or the manager, and as it can also provide the accountability, the transparency, or the auditability of the tasks or the functions that are related or relevant to the resources or the data within the system or the service, among the different or the various users or the devices within an organization, such as the bank teller, the supervisor, or the manager. However, segregation of duties is not the most effective implementation for ensuring data privacy when sensitive customer data is going to be added to a database, as it does not provide or offer the encryption or the protection for the sensitive customer data or the information that is transmitted or communicated over the data link layer, and as it does not prevent or reduce the risk of unauthorized or inappropriate access, disclosure, modification, or interception of the sensitive customer data or the information by the third parties or the attackers who capture or monitor the sensitive customer data or the information over the data link layer.
References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 5, page 146; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 5, page 211
Which of the following is the MOST important goal of information asset valuation?
Developing a consistent and uniform method of controlling access on information assets
Developing appropriate access control policies and guidelines
Assigning a financial value to an organization’s information assets
Determining the appropriate level of protection
According to the CISSP All-in-One Exam Guide2, the most important goal of information asset valuation is to assign a financial value to an organization’s information assets. Information asset valuation is the process of estimating the worth or importance of the information assets that an organization owns, creates, uses, or maintains, such as data, documents, records, or intellectual property. Information asset valuation helps the organization to measure the impact and return of its information assets, as well as to determine the appropriate level of protection, investment, and management for them. Information asset valuation also helps the organization to comply with the legal, regulatory, and contractual obligations that may require the disclosure or reporting of the value of its information assets. Developing a consistent and uniform method of controlling access on information assets is not the most important goal of information asset valuation, although it may be a benefit or outcome of it. Controlling access on information assets is the process of granting or denying the rights and permissions to access, use, modify, or disclose the information assets, based on the identity, role, or need of the users or processes. Controlling access on information assets helps the organization to protect the confidentiality, integrity, and availability of its information assets, as well as to enforce the security policies and standards for them. Developing appropriate access control policies and guidelines is not the most important goal of information asset valuation, although it may be a benefit or outcome of it. Access control policies and guidelines are the documents that define the rules, principles, and procedures for controlling access on information assets, as well as the roles and responsibilities of the stakeholders involved. Access control policies and guidelines help the organization to establish and communicate the expectations and requirements for controlling access on information assets, as well as to monitor and audit the compliance and effectiveness of the access control mechanisms. Determining the appropriate level of protection is not the most important goal of information asset valuation, although it may be a benefit or outcome of it. The level of protection is the degree or extent of the security measures and controls that are applied to the information assets, to prevent or mitigate the potential threats and risks that may affect them. The level of protection should be proportional to the value and sensitivity of the information assets, as well as the impact and likelihood of the threats and risks. References: 2
Single Sign-On (SSO) is PRIMARILY designed to address which of the following?
Confidentiality and Integrity
Availability and Accountability
Integrity and Availability
Accountability and Assurance
Single Sign-On (SSO) is primarily designed to address accountability and assurance. SSO is a mechanism that enables a user to authenticate once and gain access to multiple systems or applications without having to reauthenticate. SSO improves accountability by providing a centralized and consistent way of managing user identities and access rights across different systems or applications. SSO also improves assurance by reducing the risk of password compromise, user fatigue, and human error, as users do not have to remember or enter multiple passwords. The other options are not the primary goals of SSO, but rather secondary benefits or challenges. Option A is a description of confidentiality and integrity, which are security properties that SSO can enhance by using strong encryption and authentication methods, but they are not the main purpose of SSO. Option B is a description of availability and accountability, which are security properties that SSO can improve by simplifying the user experience and reducing the authentication overhead, but they are not the primary objectives of SSO. Option C is a description of integrity and availability, which are security properties that SSO can support by ensuring the consistency and reliability of user data and access, but they are not the main focus of SSO. References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 5, p. 281; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 6, p. 355.
A vulnerability in which of the following components would be MOST difficult to detect?
Kernel
Shared libraries
Hardware
System application
According to the CISSP CBK Official Study Guide, a vulnerability in hardware would be the most difficult to detect. A vulnerability is a weakness or exposure in a system, network, or application, which may be exploited by threats and cause harm to the organization or its assets. A vulnerability can exist in various components of a system, network, or application, such as the kernel, the shared libraries, the hardware, or the system application. A vulnerability in hardware would be the most difficult to detect, as it may require physical access, specialized tools, or advanced skills to identify and measure the vulnerability. Hardware is the physical or tangible component of a system, network, or application that provides the basic functionality, performance, and support for the system, network, or application, such as the processor, memory, disk, or network card. Hardware may have vulnerabilities due to design flaws, manufacturing defects, configuration errors, or physical damage. A vulnerability in hardware may affect the security, reliability, or availability of the system, network, or application, such as causing data leakage, performance degradation, or system failure. A vulnerability in the kernel would not be the most difficult to detect, although it may be a difficult to detect. The kernel is the core or central component of a system, network, or application that provides the basic functionality, performance, and control for the system, network, or application, such as the operating system, the hypervisor, or the firmware. The kernel may have vulnerabilities due to design flaws, coding errors, configuration errors, or malicious modifications. A vulnerability in the kernel may affect the security, reliability, or availability of the system, network, or application, such as causing privilege escalation, system compromise, or system crash. A vulnerability in the kernel may be detected by using various tools, techniques, or methods, such as code analysis, vulnerability scanning, or penetration testing. A vulnerability in the shared libraries would not be the most difficult to detect, although it may be a difficult to detect. The shared libraries are the reusable or common components of a system, network, or application, that provide the functionality, performance, and compatibility for the system, network, or application, such as the dynamic link libraries, the application programming interfaces, or the frameworks.
In which identity management process is the subject’s identity established?
Trust
Provisioning
Authorization
Enrollment
According to the CISSP CBK Official Study Guide1, the identity management process in which the subject’s identity is established is enrollment. Enrollment is the process of registering or enrolling a subject into an identity management system, such as a user into an authentication system, or a device into a network. Enrollment is the process in which the subject’s identity is established, as it involves verifying and validating the subject’s identity, as well as collecting and storing the subject’s identity attributes, such as the name, email, or biometrics of the subject. Enrollment also involves issuing and assigning the subject’s identity credentials, such as the username, password, or certificate of the subject. Enrollment helps to create and maintain the subject’s identity record or profile, as well as to enable and facilitate the subject’s access and use of the system or network. Trust is not the identity management process in which the subject’s identity is established, although it may be a factor that influences the enrollment process. Trust is the degree of confidence or assurance that a subject or an entity has in another subject or entity, such as a user in a system, or a system in a network. Trust may influence the enrollment process, as it may determine the level or extent of the identity verification and validation, as well as the identity attributes and credentials that are required or provided for the enrollment process. Provisioning is not the identity management process in which the subject’s identity is established, although it may be a process that follows or depends on the enrollment process. Provisioning is the process of creating, assigning, and configuring a subject’s account or resource with the necessary access rights and permissions to perform the tasks and functions that are required by the subject’s role and responsibilities, as well as the security policies and standards of the system or network. Provisioning is not the process in which the subject’s identity is established, as it does not involve verifying and validating the subject’s identity, or collecting and storing the subject’s identity attributes or credentials. Authorization is not the identity management process in which the subject’s identity is established, although it may be a process that follows or depends on the enrollment process. Authorization is the process of granting or denying a subject’s access or use of an object or a resource, based on the subject’s identity, role, or credentials, as well as the security policies and rules of the system or network. Authorization is not the process in which the subject’s identity is established, as it does not involve verifying and validating the subject’s identity, or collecting and storing the subject’s identity attributes or credentials. References: 1
Although code using a specific program language may not be susceptible to a buffer overflow attack,
most calls to plug-in programs are susceptible.
most supporting application code is susceptible.
the graphical images used by the application could be susceptible.
the supporting virtual machine could be susceptible.
According to the CISSP CBK Official Study Guide, although code using a specific program language may not be susceptible to a buffer overflow attack, the supporting virtual machine could be susceptible. A buffer overflow attack is a type of attack that exploits a vulnerability in the memory allocation and management of a program, by sending more data than the buffer can hold, and overwriting the adjacent memory locations, such as the return address, the stack pointer, or the registers. A buffer overflow attack can result in various consequences, such as crashing the program, executing arbitrary code, or escalating privileges. A program language is a set of rules and syntax that defines how a program is written and executed, such as C, Java, Python, or Ruby. Some program languages, such as C, are more susceptible to buffer overflow attacks, as they allow direct manipulation of memory and pointers, and do not perform bounds checking on the buffers. Other program languages, such as Java, are less susceptible to buffer overflow attacks, as they use a virtual machine to execute the code, and perform automatic memory management and garbage collection. A virtual machine is a software application that emulates a physical machine, and provides an isolated and abstracted environment for running programs, such as the Java Virtual Machine (JVM) or the .NET Framework. However, the virtual machine itself could be susceptible to buffer overflow attacks, as it may be written in a program language that is vulnerable, or it may have flaws or bugs in its implementation or configuration. Therefore, the code using a specific program language may not be susceptible to a buffer overflow attack, but the supporting virtual machine could be susceptible. The calls to plug-in programs, the supporting application code, and the graphical images used by the application are not necessarily related to the susceptibility of the code using a specific program language to a buffer overflow attack, as they may depend on other factors, such as the type, source, and quality of the plug-in programs, the application code, and the graphical images, as well as the security controls and mechanisms that are applied to them.
Which of the following is a remote access protocol that uses a static authentication?
Point-to-Point Tunneling Protocol (PPTP)
Routing Information Protocol (RIP)
Password Authentication Protocol (PAP)
Challenge Handshake Authentication Protocol (CHAP)
Password Authentication Protocol (PAP) is a remote access protocol that uses a static authentication method, which means that the username and password are sent in clear text over the network. PAP is considered insecure and vulnerable to eavesdropping and replay attacks, as anyone who can capture the network traffic can obtain the credentials. PAP is supported by Point-to-Point Protocol (PPP), which is a common protocol for establishing remote connections over dial-up, broadband, or wireless networks. PAP is usually used as a fallback option when more secure protocols, such as Challenge Handshake Authentication Protocol (CHAP) or Extensible Authentication Protocol (EAP), are not available or compatible.
When designing a vulnerability test, which one of the following is likely to give the BEST indication of what components currently operate on the network?
Topology diagrams
Mapping tools
Asset register
Ping testing
According to the CISSP All-in-One Exam Guide2, when designing a vulnerability test, mapping tools are likely to give the best indication of what components currently operate on the network. Mapping tools are software applications that scan and discover the network topology, devices, services, and protocols. They can provide a graphical representation of the network structure and components, as well as detailed information about each node and connection. Mapping tools can help identify potential vulnerabilities and weaknesses in the network configuration and architecture, as well as the exposure and attack surface of the network. Topology diagrams are not likely to give the best indication of what components currently operate on the network, as they may be outdated, inaccurate, or incomplete. Topology diagrams are static and abstract representations of the network layout and design, but they may not reflect the actual and dynamic state of the network. Asset register is not likely to give the best indication of what components currently operate on the network, as it may be outdated, inaccurate, or incomplete. Asset register is a document that lists and categorizes the assets owned by an organization, such as hardware, software, data, and personnel. However, it may not capture the current status, configuration, and interconnection of the assets, as well as the changes and updates that occur over time. Ping testing is not likely to give the best indication of what components currently operate on the network, as it is a simple and limited technique that only checks the availability and response time of a host. Ping testing is a network utility that sends an echo request packet to a target host and waits for an echo reply packet. It can measure the connectivity and latency of the host, but it cannot provide detailed information about the host’s characteristics, services, and vulnerabilities. References: 2
During the risk assessment phase of the project the CISO discovered that a college within the University is collecting Protected Health Information (PHI) data via an application that was developed in-house. The college collecting this data is fully aware of the regulations for Health Insurance Portability and Accountability Act (HIPAA) and is fully compliant.
What is the best approach for the CISO?
During the risk assessment phase of the project the CISO discovered that a college within the University is collecting Protected Health Information (PHI) data via an application that was developed in-house. The college collecting this data is fully aware of the regulations for Health Insurance Portability and Accountability Act (HIPAA) and is fully compliant.
What is the best approach for the CISO?
Document the system as high risk
Perform a vulnerability assessment
Perform a quantitative threat assessment
Notate the information and move on
The best approach for the CISO is to notate the information and move on. A CISO is a Chief Information Security Officer, who is a senior executive responsible for overseeing and managing the information security strategy, policies, and programs of an organization. A risk assessment is a process of identifying, analyzing, and evaluating the risks that may affect the information and assets of an organization. In this scenario, the CISO discovered that a college within the University is collecting Protected Health Information (PHI) data via an application that was developed in-house. The college collecting this data is fully aware of the regulations for Health Insurance Portability and Accountability Act (HIPAA) and is fully compliant. HIPAA is a federal law that sets the standards and rules for the protection and privacy of PHI, which is any information that can be used to identify a person’s health condition, treatment, or payment. The best approach for the CISO is to notate the information and move on, as there is no need to take any further action or intervention, since the college is already compliant with the HIPAA regulations and has implemented the appropriate security measures for the PHI data. The other options are not the best approaches, but rather unnecessary or excessive actions. Documenting the system as high risk is not a best approach, as there is no evidence or indication that the system poses a high risk to the organization or the PHI data, as long as the college follows the HIPAA regulations and the security best practices. Performing a vulnerability assessment is not a best approach, as it is an intrusive and costly activity that may not be warranted or authorized, since the system is already compliant and secure. Performing a quantitative threat assessment is not a best approach, as it is a complex and time-consuming activity that may not be feasible or relevant, since the system is already compliant and secure. References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 1, p. 22; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 5, p. 280.
