Which of the following are effective countermeasures against passive network-layer attacks?
Federated security and authenticated access controls
Trusted software development and run time integrity controls
Encryption and security enabled applications
Enclave boundary protection and computing environment defense
Encryption ensures that data is transformed into a code that can only be accessed by authorized parties. Security-enabled applications ensure that only authorized users can access specific network resources, protecting against passive network-layer attacks like eavesdropping or sniffing. References: ISC2 CISSP
Which of the following BEST describes the purpose of performing security certification?
To identify system threats, vulnerabilities, and acceptable level of risk
To formalize the confirmation of compliance to security policies and standards
To formalize the confirmation of completed risk mitigation and risk analysis
To verify that system architecture and interconnections with other systems are effectively implemented
The best description of the purpose of performing security certification is to formalize the confirmation of compliance to security policies and standards. Security certification is the process of evaluating and validating the security posture and compliance of a system or network against a set of predefined criteria, such as security policies, standards, regulations, or best practices. Security certification results in a formal statement or document that attests the level of security and compliance achieved by the system or network.
A. To identify system threats, vulnerabilities, and acceptable level of risk is not the best description of the purpose of performing security certification, but rather the purpose of performing security assessment. Security assessment is the process of identifying and analyzing the security threats, vulnerabilities, and risks of a system or network, and determining the acceptable level of risk and the risk mitigation strategies.
C. To formalize the confirmation of completed risk mitigation and risk analysis is not the best description of the purpose of performing security certification, but rather the purpose of performing security accreditation. Security accreditation is the process of authorizing and approving the operation of a system or network based on the results of security certification and risk analysis, and the acceptance of residual risk.
D. To verify that system architecture and interconnections with other systems are effectively implemented is not the best description of the purpose of performing security certification, but rather one of the possible aspects or objectives of security certification. Security certification can cover various aspects of system security, such as architecture, design, implementation, configuration, operation, maintenance, or interconnection.
References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 3, page 147; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 3, page 123
Which of the following statements is TRUE regarding value boundary analysis as a functional software testing technique?
It is useful for testing communications protocols and graphical user interfaces.
It is characterized by the stateless behavior of a process implemented in a function.
Test inputs are obtained from the derived threshold of the given functional specifications.
An entire partition can be covered by considering only one representative value from that partition.
Value boundary analysis is a functional software testing technique that tests the behavior of a software system or component when it receives inputs that are at the boundary or edge of the expected range of values. Value boundary analysis is based on the assumption that errors are more likely to occur at the boundary values than at the normal values. Test inputs are obtained from the derived threshold of the given functional specifications, such as the minimum, maximum, or just above or below the boundary values. Value boundary analysis can help identify errors or defects in the software system or component that may cause unexpected or incorrect outputs, crashes, or failures34 References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 8: Software Development Security, p. 497; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Domain 8: Software Development Security, p. 1015.
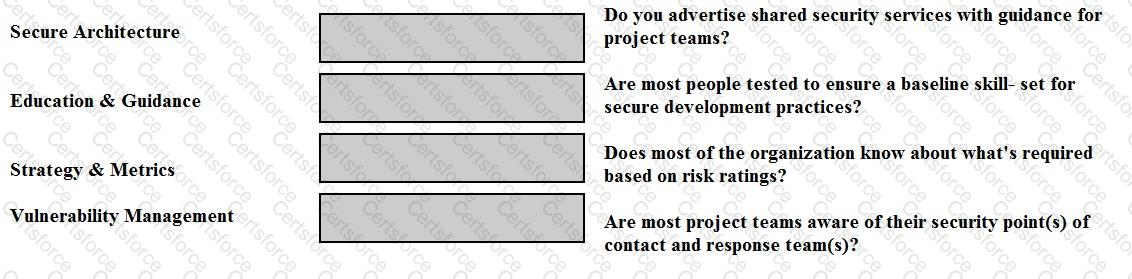
Match the objectives to the assessment questions in the governance domain of Software Assurance Maturity Model (SAMM).
The correct matches are as follows:
Secure Architecture -> Do you advertise shared security services with guidance for project teams?
Education & Guidance -> Are most people tested to ensure a baseline skill-set for secure development practices?
Strategy & Metrics -> Does most of the organization know about what’s required based on risk ratings?
Vulnerability Management -> Are most project teams aware of their security point(s) of contact and response team(s)?
Comprehensive Explanation: These matches are based on the definitions and objectives of the four governance domain practices in the Software Assurance Maturity Model (SAMM). SAMM is a framework to help organizations assess and improve their software security posture. The governance domain covers the organizational aspects of software security, such as policies, metrics, and roles.
Secure Architecture: This practice aims to provide a consistent and secure design for software projects, as well as reusable security services and components. The assessment question measures the availability and guidance of these shared security services for project teams.
Education & Guidance: This practice aims to raise the awareness and skills of the staff involved in software development, as well as provide them with the necessary tools and resources. The assessment question measures the level of testing and verification of the staff’s secure development knowledge and abilities.
Strategy & Metrics: This practice aims to define and communicate the software security strategy, goals, and priorities, as well as measure and monitor the progress and effectiveness of software security activities. The assessment question measures the degree of awareness and alignment of the organization with the risk-based requirements for software security.
Vulnerability Management: This practice aims to identify and remediate the vulnerabilities in the software products, as well as prevent or mitigate the impact of potential incidents. The assessment question measures the level of awareness and collaboration of the project teams with the security point(s) of contact and response team(s).
References: SAMM Governance Domain; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 8, page 452
Which of the following activities BEST identifies operational problems, security misconfigurations, and malicious attacks?
Policy documentation review
Authentication validation
Periodic log reviews
Interface testing
The activity that best identifies operational problems, security misconfigurations, and malicious attacks is periodic log reviews. Log reviews are the process of examining and analyzing the records of events or activities that occur on a system or network, such as user actions, system errors, security alerts, or network traffic. Periodic log reviews can help to identify operational problems, such as system failures, performance issues, or configuration errors, by detecting anomalies, trends, or patterns in the log data. Periodic log reviews can also help to identify security misconfigurations, such as weak passwords, open ports, or missing patches, by comparing the log data with the security policies, standards, or baselines. Periodic log reviews can also help to identify malicious attacks, such as unauthorized access, data breaches, or denial of service, by recognizing signs of intrusion, compromise, or exploitation in the log data. The other options are not the best activities to identify operational problems, security misconfigurations, and malicious attacks, but rather different types of activities. Policy documentation review is the process of examining and evaluating the documents that define the rules and guidelines for the system or network security, such as policies, procedures, or standards. Policy documentation review can help to ensure the completeness, consistency, and compliance of the security documents, but not to identify the actual problems or attacks. Authentication validation is the process of verifying and confirming the identity and credentials of a user or device that requests access to a system or network, such as passwords, tokens, or certificates. Authentication validation can help to prevent unauthorized access, but not to identify the existing problems or attacks. Interface testing is the process of checking and evaluating the functionality, usability, and reliability of the interfaces between different components or systems, such as modules, applications, or networks. Interface testing can help to ensure the compatibility, interoperability, and integration of the interfaces, but not to identify the problems or attacks. References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 7, p. 377; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 7, p. 405.
In order for a security policy to be effective within an organization, it MUST include
strong statements that clearly define the problem.
a list of all standards that apply to the policy.
owner information and date of last revision.
disciplinary measures for non compliance.
In order for a security policy to be effective within an organization, it must include disciplinary measures for non compliance. A security policy is a document or a statement that defines and communicates the security goals, the objectives, or the expectations of the organization, and that provides the guidance or the direction for the security activities, the processes, or the functions of the organization. A security policy must include disciplinary measures for non compliance, which are the actions or the consequences that the organization will take or impose on the users or the devices that violate or disregard the security policy or the security rules. Disciplinary measures for non compliance can help ensure the effectiveness of the security policy, as they can deter or prevent the users or the devices from engaging in the behaviors or the practices that could jeopardize or undermine the security of the organization, and they can also enforce or reinforce the accountability or the responsibility of the users or the devices for the security of the organization. References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 1, page 18; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 1, page 26
Which of the following standards/guidelines requires an Information Security Management System (ISMS) to be defined?
International Organization for Standardization (ISO) 27000 family
Information Technology Infrastructure Library (ITIL)
Payment Card Industry Data Security Standard (PCIDSS)
ISO/IEC 20000
The International Organization for Standardization (ISO) 27000 family of standards/guidelines requires an Information Security Management System (ISMS) to be defined. An ISMS is a systematic approach to managing the security of information assets, such as data, systems, processes, and people. An ISMS includes policies, procedures, controls, and activities that aim to protect the confidentiality, integrity, and availability of information, as well as to comply with the legal and regulatory requirements. The ISO 27000 family provides best practices and guidance for establishing, implementing, maintaining, and improving an ISMS. The ISO 27001 standard specifies the requirements for an ISMS, while the other standards in the family provide more detailed or specific guidance on different aspects of information security34 References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 1: Security and Risk Management, p. 23; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Domain 1: Security and Risk Management, p. 25.
Which of the following is the BEST method to reduce the effectiveness of phishing attacks?
User awareness
Two-factor authentication
Anti-phishing software
Periodic vulnerability scan
According to the CISSP For Dummies4, the best method to reduce the effectiveness of phishing attacks is user awareness. This means that the users should be educated and trained on how to recognize and avoid phishing emails and websites, which are fraudulent attempts to obtain sensitive information or credentials from the users by impersonating legitimate entities or persons. User awareness can help users to identify the common signs and indicators of phishing, such as spoofed sender addresses, misleading links, spelling and grammar errors, urgent or threatening messages, and requests for personal or financial information. User awareness can also help users to follow the best practices and preventive measures to protect themselves from phishing, such as verifying the source and content of the messages, using strong and unique passwords, enabling two-factor authentication, reporting and deleting suspicious messages, and using anti-phishing software and tools. Two-factor authentication is not the best method to reduce the effectiveness of phishing attacks, as it may not prevent the users from falling for phishing in the first place. Two-factor authentication is a security mechanism that requires the users to provide two pieces of evidence to prove their identity, such as a password and a one-time code. However, some phishing attacks may be able to bypass or compromise two-factor authentication, such as by using man-in-the-middle techniques, intercepting the codes, or tricking the users into entering the codes on fake websites. Anti-phishing software is not the best method to reduce the effectiveness of phishing attacks, as it may not detect or block all phishing attempts. Anti-phishing software is a software application that helps the users to identify and avoid phishing emails and websites, by using various methods such as blacklists, whitelists, heuristics, and machine learning. However, anti-phishing software may not be able to keep up with the evolving and sophisticated techniques of phishing, such as using encryption, obfuscation, or personalization. Anti-phishing software may also generate false positives or negatives, which may confuse or mislead the users. Periodic vulnerability scan is not the best method to reduce the effectiveness of phishing attacks, as it may not address the human factor of phishing. Periodic vulnerability scan is a process that scans and tests the network, systems, and applications for potential weaknesses and exposures that may be exploited by attackers. However, phishing attacks mainly target the users, not the technical vulnerabilities, by exploiting their emotions, curiosity, or trust. Periodic vulnerability scan may not be able to prevent or detect phishing attacks, unless they are combined with user awareness and education. References: 4
Which of the following command line tools can be used in the reconnaisance phase of a network vulnerability assessment?
dig
ifconfig
ipconfig
nbtstat
Dig is a command line tool that can be used in the reconnaissance phase of a network vulnerability assessment. Dig stands for domain information groper, and it is used to query Domain Name System (DNS) servers and obtain information about domains, hosts, and records. Dig can help discover the network topology, the IP addresses, and the services running on the target network.
B. ifconfig is a command line tool that can be used to configure and display the network interfaces on a system, but it is not useful for the reconnaissance phase of a network vulnerability assessment, as it only shows the local information and not the target information.
C. ipconfig is a command line tool that can be used to configure and display the network settings on a Windows system, but it is not useful for the reconnaissance phase of a network vulnerability assessment, as it only shows the local information and not the target information.
D. nbtstat is a command line tool that can be used to display the NetBIOS over TCP/IP statistics and information on a Windows system, but it is not useful for the reconnaissance phase of a network vulnerability assessment, as it only works for NetBIOS-enabled systems and not for other protocols.
References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 7, page 411; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 7, page 365
Which of the following is the PRIMARY security concern associated with the implementation of smart cards?
The cards have limited memory
Vendor application compatibility
The cards can be misplaced
Mobile code can be embedded in the card
The primary security concern associated with the implementation of smart cards is that the cards can be misplaced, lost, stolen, or damaged, resulting in the compromise of the user’s identity, credentials, or data stored on the card. The other options are not the primary security concern, but rather secondary or minor issues. The cards have limited memory, which may affect the performance or functionality of the card, but not the security. Vendor application compatibility may affect the interoperability or usability of the card, but not the security. Mobile code can be embedded in the card, which may introduce malicious or unauthorized functionality, but this is a rare and sophisticated attack that requires physical access to the card and specialized equipment. References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 5, p. 275; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 6, p. 348.
A manufacturing organization wants to establish a Federated Identity Management (FIM) system with its 20 different supplier companies. Which of the following is the BEST solution for the manufacturing organization?
Trusted third-party certification
Lightweight Directory Access Protocol (LDAP)
Security Assertion Markup language (SAML)
Cross-certification
Security Assertion Markup Language (SAML) is the best solution for the manufacturing organization that wants to establish a Federated Identity Management (FIM) system with its 20 different supplier companies. FIM is a process that allows the sharing and recognition of identities across different organizations that have a trust relationship. FIM enables the users of one organization to access the resources or services of another organization without having to create or maintain multiple accounts or credentials. FIM can provide several benefits, such as:
Improving the user experience and convenience by reducing the need for multiple logins and passwords
Enhancing the security and privacy by minimizing the exposure and duplication of sensitive information
Increasing the efficiency and productivity by streamlining the authentication and authorization processes
Reducing the cost and complexity by simplifying the identity management and administration
SAML is a standard protocol that supports FIM by allowing the exchange of authentication and authorization information between different parties. SAML uses XML-based messages, called assertions, to convey the identity, attributes, and entitlements of a user to a service provider. SAML defines three roles for the parties involved in FIM:
Identity provider (IdP): the party that authenticates the user and issues the SAML assertion
Service provider (SP): the party that provides the resource or service that the user wants to access
User or principal: the party that requests access to the resource or service
SAML works as follows:
The user requests access to a resource or service from the SP
The SP redirects the user to the IdP for authentication
The IdP authenticates the user and generates a SAML assertion that contains the user’s identity, attributes, and entitlements
The IdP sends the SAML assertion to the SP
The SP validates the SAML assertion and grants or denies access to the user based on the information in the assertion
SAML is the best solution for the manufacturing organization that wants to establish a FIM system with its 20 different supplier companies, because it can enable the seamless and secure access to the resources or services across the different organizations, without requiring the users to create or maintain multiple accounts or credentials. SAML can also provide interoperability and compatibility between different platforms and technologies, as it is based on a standard and open protocol.
The other options are not the best solutions for the manufacturing organization that wants to establish a FIM system with its 20 different supplier companies, but rather solutions that have other limitations or drawbacks. Trusted third-party certification is a process that involves a third party, such as a certificate authority (CA), that issues and verifies digital certificates that contain the public key and identity information of a user or an entity. Trusted third-party certification can provide authentication and encryption for the communication between different parties, but it does not provide authorization or entitlement information for the access to the resources or services. Lightweight Directory Access Protocol (LDAP) is a protocol that allows the access and management of directory services, such as Active Directory, that store the identity and attribute information of users and entities. LDAP can provide a centralized and standardized way to store and retrieve identity and attribute information, but it does not provide a mechanism to exchange or federate the information across different organizations. Cross-certification is a process that involves two or more CAs that establish a trust relationship and recognize each other’s certificates. Cross-certification can extend the trust and validity of the certificates across different domains or organizations, but it does not provide a mechanism to exchange or federate the identity, attribute, or entitlement information.
Which of the following BEST describes an access control method utilizing cryptographic keys derived from a smart card private key that is embedded within mobile devices?
Derived credential
Temporary security credential
Mobile device credentialing service
Digest authentication
Derived credential is the best description of an access control method utilizing cryptographic keys derived from a smart card private key that is embedded within mobile devices. A smart card is a device that contains a microchip that stores a private key and a digital certificate that are used for authentication and encryption. A smart card is typically inserted into a reader that is attached to a computer or a terminal, and the user enters a personal identification number (PIN) to unlock the smart card and access the private key and the certificate. A smart card can provide a high level of security and convenience for the user, as it implements a two-factor authentication method that combines something the user has (the smart card) and something the user knows (the PIN).
However, a smart card may not be compatible or convenient for mobile devices, such as smartphones or tablets, that do not have a smart card reader or a USB port. To address this issue, a derived credential is a solution that allows the user to use a mobile device as an alternative to a smart card for authentication and encryption. A derived credential is a cryptographic key and a certificate that are derived from the smart card private key and certificate, and that are stored on the mobile device. A derived credential works as follows:
The user inserts the smart card into a reader that is connected to a computer or a terminal, and enters the PIN to unlock the smart card
The user connects the mobile device to the computer or the terminal via a cable, Bluetooth, or Wi-Fi
The user initiates a request to generate a derived credential on the mobile device
The computer or the terminal verifies the smart card certificate with a trusted CA, and generates a derived credential that contains a cryptographic key and a certificate that are derived from the smart card private key and certificate
The computer or the terminal transfers the derived credential to the mobile device, and stores it in a secure element or a trusted platform module on the device
The user disconnects the mobile device from the computer or the terminal, and removes the smart card from the reader
The user can use the derived credential on the mobile device to authenticate and encrypt the communication with other parties, without requiring the smart card or the PIN
A derived credential can provide a secure and convenient way to use a mobile device as an alternative to a smart card for authentication and encryption, as it implements a two-factor authentication method that combines something the user has (the mobile device) and something the user is (the biometric feature). A derived credential can also comply with the standards and policies for the use of smart cards, such as the Personal Identity Verification (PIV) or the Common Access Card (CAC) programs.
The other options are not the best descriptions of an access control method utilizing cryptographic keys derived from a smart card private key that is embedded within mobile devices, but rather descriptions of other methods or concepts. Temporary security credential is a method that involves issuing a short-lived credential, such as a token or a password, that can be used for a limited time or a specific purpose. Temporary security credential can provide a flexible and dynamic way to grant access to the users or entities, but it does not involve deriving a cryptographic key from a smart card private key. Mobile device credentialing service is a concept that involves providing a service that can issue, manage, or revoke credentials for mobile devices, such as certificates, tokens, or passwords. Mobile device credentialing service can provide a centralized and standardized way to control the access of mobile devices, but it does not involve deriving a cryptographic key from a smart card private key. Digest authentication is a method that involves using a hash function, such as MD5, to generate a digest or a fingerprint of the user’s credentials, such as the username and password, and sending it to the server for verification. Digest authentication can provide a more secure way to authenticate the user than the basic authentication, which sends the credentials in plain text, but it does not involve deriving a cryptographic key from a smart card private key.
What is the BEST approach for controlling access to highly sensitive information when employees have the same level of security clearance?
Audit logs
Role-Based Access Control (RBAC)
Two-factor authentication
Application of least privilege
Applying the principle of least privilege is the best approach for controlling access to highly sensitive information when employees have the same level of security clearance. The principle of least privilege is a security concept that states that every user or process should have the minimum amount of access rights and permissions that are necessary to perform their tasks or functions, and nothing more. The principle of least privilege can provide several benefits, such as:
Improving the security and confidentiality of the information by limiting the access and exposure of the sensitive data to the authorized users and purposes
Reducing the risk and impact of unauthorized access or disclosure of the information by minimizing the attack surface and the potential damage
Increasing the accountability and auditability of the information by tracking and logging the access and usage of the sensitive data
Enhancing the performance and efficiency of the system by reducing the complexity and overhead of the access control mechanisms
Applying the principle of least privilege is the best approach for controlling access to highly sensitive information when employees have the same level of security clearance, because it can ensure that the employees can only access the information that is relevant and necessary for their tasks or functions, and that they cannot access or manipulate the information that is beyond their scope or authority. For example, if the highly sensitive information is related to a specific project or department, then only the employees who are involved in that project or department should have access to that information, and not the employees who have the same level of security clearance but are not involved in that project or department.
The other options are not the best approaches for controlling access to highly sensitive information when employees have the same level of security clearance, but rather approaches that have other purposes or effects. Audit logs are records that capture and store the information about the events and activities that occur within a system or a network, such as the access and usage of the sensitive data. Audit logs can provide a reactive and detective layer of security by enabling the monitoring and analysis of the system or network behavior, and facilitating the investigation and response of the incidents. However, audit logs cannot prevent or reduce the access or disclosure of the sensitive information, but rather provide evidence or clues after the fact. Role-Based Access Control (RBAC) is a method that enforces the access rights and permissions of the users based on their roles or functions within the organization, rather than their identities or attributes. RBAC can provide a granular and dynamic layer of security by defining and assigning the roles and permissions according to the organizational structure and policies. However, RBAC cannot control the access to highly sensitive information when employees have the same level of security clearance and the same role or function within the organization, but rather rely on other criteria or mechanisms. Two-factor authentication is a technique that verifies the identity of the users by requiring them to provide two pieces of evidence or factors, such as something they know (e.g., password, PIN), something they have (e.g., token, smart card), or something they are (e.g., fingerprint, face). Two-factor authentication can provide a strong and preventive layer of security by preventing unauthorized access to the system or network by the users who do not have both factors. However, two-factor authentication cannot control the access to highly sensitive information when employees have the same level of security clearance and the same two factors, but rather rely on other criteria or mechanisms.
Users require access rights that allow them to view the average salary of groups of employees. Which control would prevent the users from obtaining an individual employee’s salary?
Limit access to predefined queries
Segregate the database into a small number of partitions each with a separate security level
Implement Role Based Access Control (RBAC)
Reduce the number of people who have access to the system for statistical purposes
Limiting access to predefined queries is the control that would prevent the users from obtaining an individual employee’s salary, if they only require access rights that allow them to view the average salary of groups of employees. A query is a request for information from a database, which can be expressed in a structured query language (SQL) or a graphical user interface (GUI). A query can specify the criteria, conditions, and operations for selecting, filtering, sorting, grouping, and aggregating the data from the database. A predefined query is a query that has been created and stored in advance by the database administrator or the data owner, and that can be executed by the authorized users without any modification. A predefined query can provide several benefits, such as:
Improving the performance and efficiency of the database by reducing the processing time and resources required for executing the queries
Enhancing the security and confidentiality of the database by restricting the access and exposure of the sensitive data to the authorized users and purposes
Increasing the accuracy and reliability of the database by preventing the errors or inconsistencies that might occur due to the user input or modification of the queries
Reducing the cost and complexity of the database by simplifying the query design and management
Limiting access to predefined queries is the control that would prevent the users from obtaining an individual employee’s salary, if they only require access rights that allow them to view the average salary of groups of employees, because it can ensure that the users can only access the data that is relevant and necessary for their tasks, and that they cannot access or manipulate the data that is beyond their scope or authority. For example, a predefined query can be created and stored that calculates and displays the average salary of groups of employees based on certain criteria, such as department, position, or experience. The users who need to view this information can execute this predefined query, but they cannot modify it or create their own queries that might reveal the individual employee’s salary or other sensitive data.
The other options are not the controls that would prevent the users from obtaining an individual employee’s salary, if they only require access rights that allow them to view the average salary of groups of employees, but rather controls that have other purposes or effects. Segregating the database into a small number of partitions each with a separate security level is a control that would improve the performance and security of the database by dividing it into smaller and manageable segments that can be accessed and processed independently and concurrently. However, this control would not prevent the users from obtaining an individual employee’s salary, if they have access to the partition that contains the salary data, and if they can create or modify their own queries. Implementing Role Based Access Control (RBAC) is a control that would enforce the access rights and permissions of the users based on their roles or functions within the organization, rather than their identities or attributes. However, this control would not prevent the users from obtaining an individual employee’s salary, if their roles or functions require them to access the salary data, and if they can create or modify their own queries. Reducing the number of people who have access to the system for statistical purposes is a control that would reduce the risk and impact of unauthorized access or disclosure of the sensitive data by minimizing the exposure and distribution of the data. However, this control would not prevent the users from obtaining an individual employee’s salary, if they are among the people who have access to the system, and if they can create or modify their own queries.
With data labeling, which of the following MUST be the key decision maker?
Information security
Departmental management
Data custodian
Data owner
With data labeling, the data owner must be the key decision maker. The data owner is the person or entity that has the authority and responsibility for the data, including its classification, protection, and usage. The data owner must decide how to label the data according to its sensitivity, criticality, and value, and communicate the labeling scheme to the data custodians and users. The data owner must also review and update the data labels as needed. The other options are not the key decision makers for data labeling, as they either do not have the authority or responsibility for the data (A, B, and C), or do not have the knowledge or interest in the data (B and C). References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 2, page 63; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 2, page 69.
