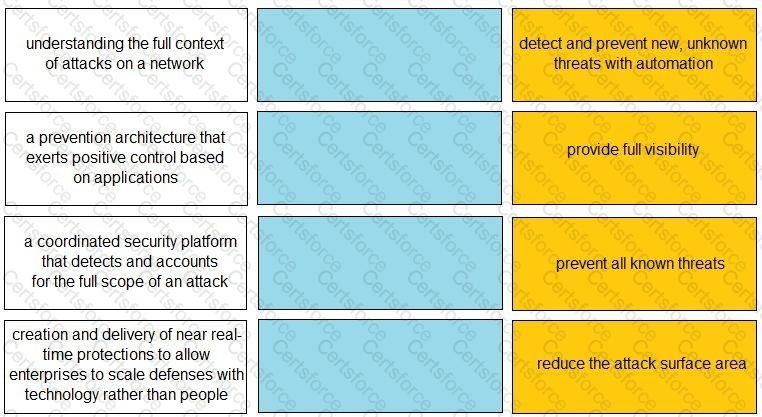
Match each description to a Security Operating Platform key capability.
Which item accurately describes a security weakness that is caused by implementing a “ports first” data security solution in a traditional data center?
Given the graphic, match each stage of the cyber-attack lifecycle to its description.


At which layer of the OSI model are routing protocols defined?
Which scenario highlights how a malicious Portable Executable (PE) file is leveraged as an attack?
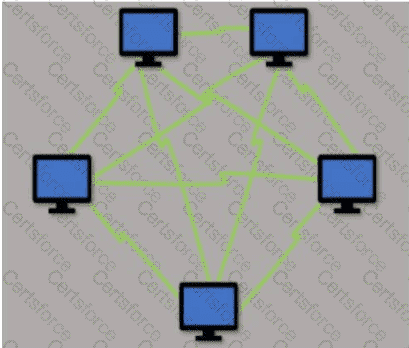
Which type of LAN technology is being displayed in the diagram?
What are two examples of an attacker using social engineering? (Choose two.)
Which type of IDS/IPS uses a baseline of normal network activity to identify unusual patterns or levels of network activity that may be indicative of an intrusion attempt?
What is the ptrpose of automation in SOAR?
Which characteristic of serverless computing enables developers to quickly deploy application code?