What protocol requires all routers in the same domain to maintain a map of the network?
Which protocol is used by both internet service providers (ISPs) and network service providers (NSPs)?
Which type of malware takes advantage of a vulnerability on an endpoint or server?
Which option would be an example of PII that you need to prevent from leaving your enterprise network?
In which step of the cyber-attack lifecycle do hackers embed intruder code within seemingly innocuous files?
Which product functions as part of a SASE solution?
Which Palo Alto Networks tool is used to prevent endpoint systems from running malware executables such as viruses, trojans, and rootkits?
A high-profile company executive receives an urgent email containing a malicious link. The sender appears to be from the IT department of the company, and the email requests an update of the executive's login credentials for a system update.
Which type of phishing attack does this represent?
What type of area network connects end-user devices?
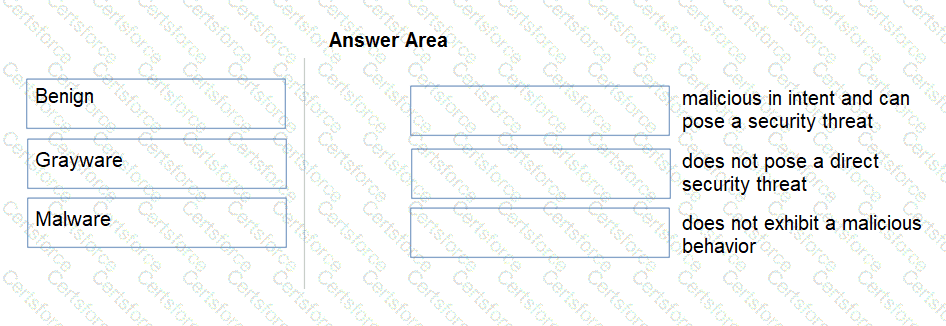
Match the Palo Alto Networks WildFire analysis verdict with its definition.